Pwndrop - Self-hosting payloads
Jul 24, 2020 by Alexandre Croix | 3039 views
A tedious step for all red-teamers is set up a system to upload payloads on the victim's machine. Kuba Gretzky, the author of Evilginx, released a nice tool to simplify this task.
Pwndrop is a self-deployable file hosting service allowing to easily upload and download payloads over HTTP and WebDAV.
In practice, you have to deploy the tool on a small server or a VPS, register a domain name for your server, and... that's it. You are ready to upload your payloads.
Installation
Set up Pwndrop is very easy. Only a few steps are required: you have to deploy a server (the smallest VPS on DigitalOcean is perfect), install Pwndrop on it and register a domain name.
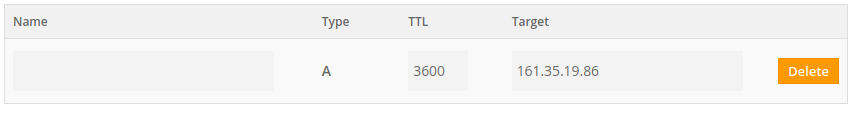
In this example, we deployed a VPS with the public IP address: 161.35.19.86. We used a free domain name provider: Freenom.com. We registered cylab.ga domain and added a A type DNS record.
We are now ready to install Pwndrop on the server. The installation is straightforward. On your server, run the following commands:
wget https://github.com/kgretzky/pwndrop/releases/download/1.0.1/pwndrop-linux-amd64.tar.gz
tar zxvf pwndrop-linux-amd64.tar.gz
./pwndrop stop
./pwndrop install
./pwndrop start
./pwndrop statusThere is only one more step for the configuration: add the IP address of your server in the pwndrop.ini file.
cd /usr/local/pwndrop
nano pwndrop.iniThe file content should looks like:
[pwndrop]
data_dir = /usr/local/pwndrop/data
admin_dir = /usr/local/pwndrop/admin
listen_ip = 161.35.19.86
http_port = 80
https_port = 443Usage
Pwndrop is a plug and play tool. No complex configuration is required.
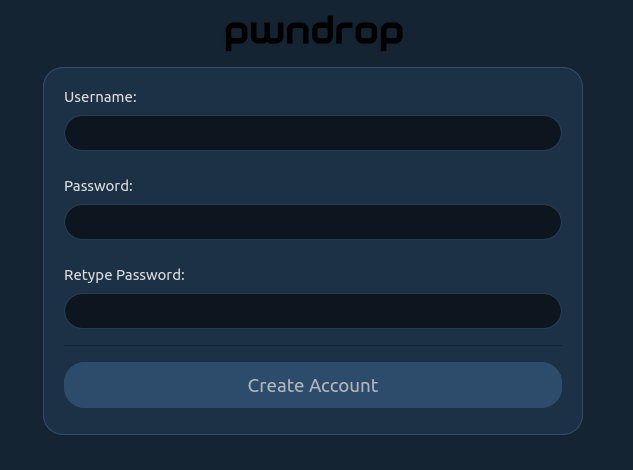
You can access the tool with the URL: https://cylab.ga/pwndrop. You have to create an account on this page.
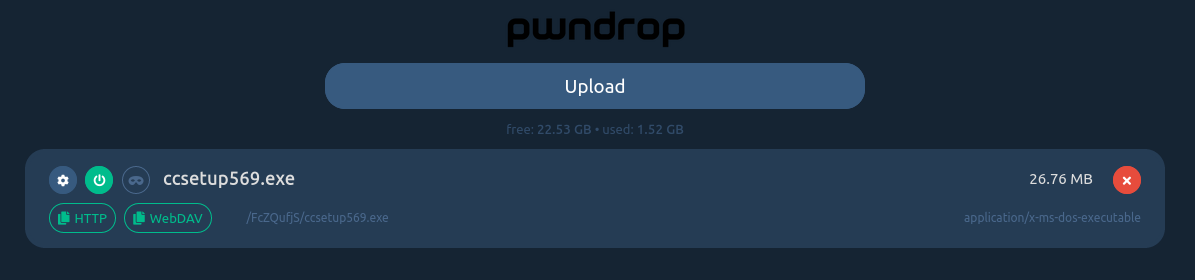
After that, it is possible to upload your payloads or your files.
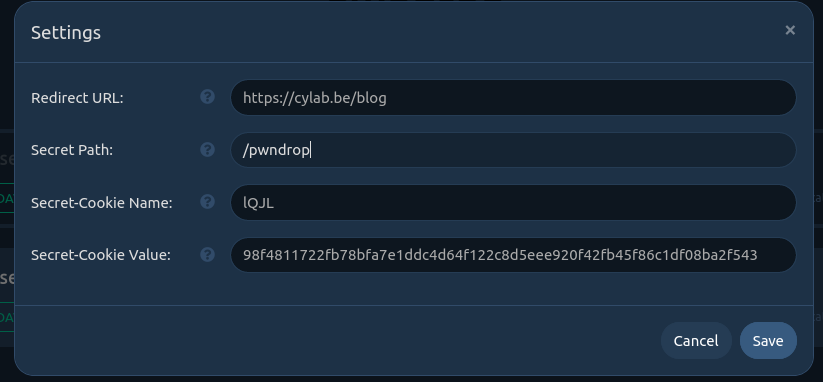
Pwndrop provides several very interesting features that are available in the settings window.
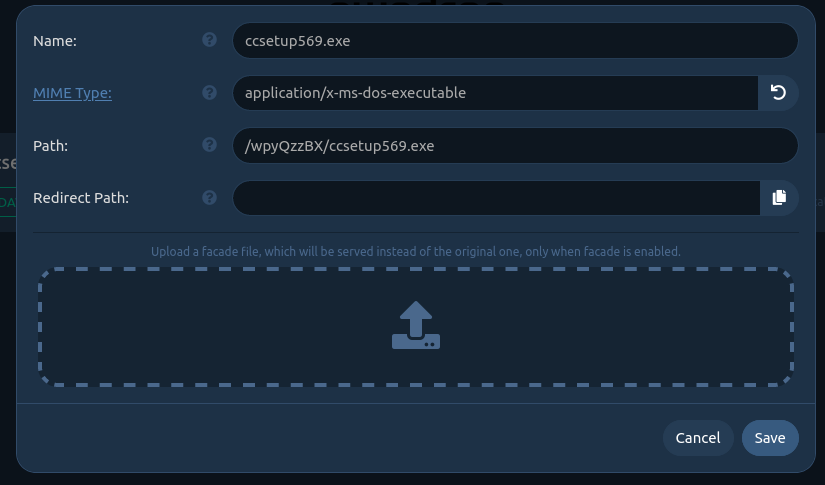
- Name is a friendly name for the admin.
- Path is the URL shared to download the file. The path can be whatever you want.
- Redirect Path is the URL path which the request will be redirected to. It can be very useful to spoof a file extension.
- MIME-Type is metadata linked to a file. An Internet browser will use the MIME to know how to process a downloaded file. Firefox, for example, will automatically open a PDF file if the MIME-type is application/pdf. This feature is very interesting to perform MIME-type confusion exploits.
Below all these fields, there is a place to upload a facade file. The facade file will be downloaded instead of the real payload file if the facade mode is enabled. It is also possible to specify a MIME-type for the facade file.
The following figure is a complete example completely configured.
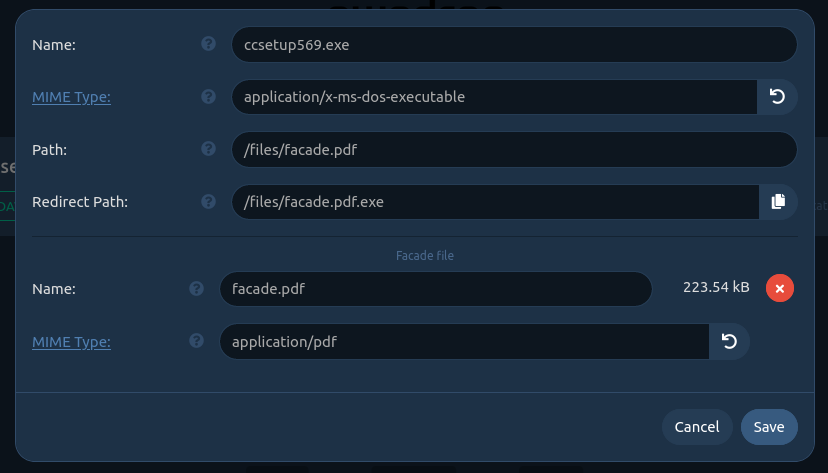
The facade file is facade.pdf and its MIME-type is pdf. That means Firefox or Chrome will automatically open the file when the user will click on the link https://cylab.ga/files/facade.pdf if the facade mode is enabled.
If the facade mode is disabled, the URL will be redirected to https://cylab.ga/files/facade.pdf.exe that is an exe file. The browser will execute the executable file when the user will click on the link.
Features
The tool has some very nice features:
- Pwndrop retrieves automatically TLS certificates from LetsEncrypt
- The admin panel is hidden thanks to a secret URL. Any wrong URL attempts will redirect the user to another chosen URL.
- Admin panel is protected by a password.
- A cookie is used to keep access to the admin panel without use the secret URL each time you want to connect to your Pwndrop server.
Conclusions
Like the great Evilginx, Pwndrop is a very cool tool. It is easy to use, no complex configuration and can be very useful! Kuba Gretzky will continue to upgrade his tool with some other features like password protection, a download file counter or a download tracker!
This blog post is licensed under
CC BY-SA 4.0