SMS-based 2-Factor Authentication is insecure !
Sep 1, 2021 by Charles Beumier | 4978 views
https://cylab.be/blog/171/sms-based-2-factor-authentication-is-insecure
The US National Institute of Standards and Technology (NIST) has declared in its Digital Authentication Guideline that SMS-based two-factor authentication should be banned due to security concerns [End of SMS-based 2-Factor Authentication; Yes, It’s Insecure!]. We explain why in this blog.
Two-factor Authentication (2FA) adds a layer of protection to the classical login procedure based on username and password, thanks to a random code which is sent via SMS. The classical authentication procedure based on what you know is upgraded to one which uses what you own: your telephone.
The Digital Authentication Guideline indicates that the use of SMS should occur through the mobile telephone network and not with VoIP (or other software-based) service. IP indeed opens up the door for attacks. But even in the mobile network, a SMS can be obtained by a Man-In-The-Middle technique as explained below.
Why SS7 is vulnerable
Mobile networks started to evolve from the 1980’s around the SS7 stack of protocols designed in the 70’s, when national operators had little reason not to trust each other. In the mid 90’s, the number of network actors increased and hence the risks, due to the telecom deregulation (multiplication of providers) and the development on IP to offload the GSM traffic. About 10 years later, research groups started to report SS7 vulnerabilities and to demonstrate exploits such as location tracking, call or SMS interception and Denial of Service. We concentrate here on the SMS interception which represents a breach for 2-FA authentication.
As said before, SS7 was designed with little concern about security. In 2G networks, the mobile phone is authenticated by a network thanks to its SIM card but the network is not. This leads for instance to the possibility to place fake antennas that can capture the radio traffic for mobile phones relatively close to the antenna. This traffic contains the voice or text messages, possibly encrypted according to the operator. After decryption exploits were demonstrated, better algorithms were developed and operators paid more attention to use them.
Unfortunately, aside from the access network and its antennas, the core network is also prone to attacks. The mobility requirement in GSM led to the creation of a big network based on operator agreement to offer world-wide roaming. Here the biggest vulnerability is due to the lack of authentication of the network equipments. If an attacker has an entry point to the SS7 network, he/she can impersonate some equipment to send requests to other network equipments world-wide. And nearly all requests are valid and not suspicious.
SMS man-in-the-middle
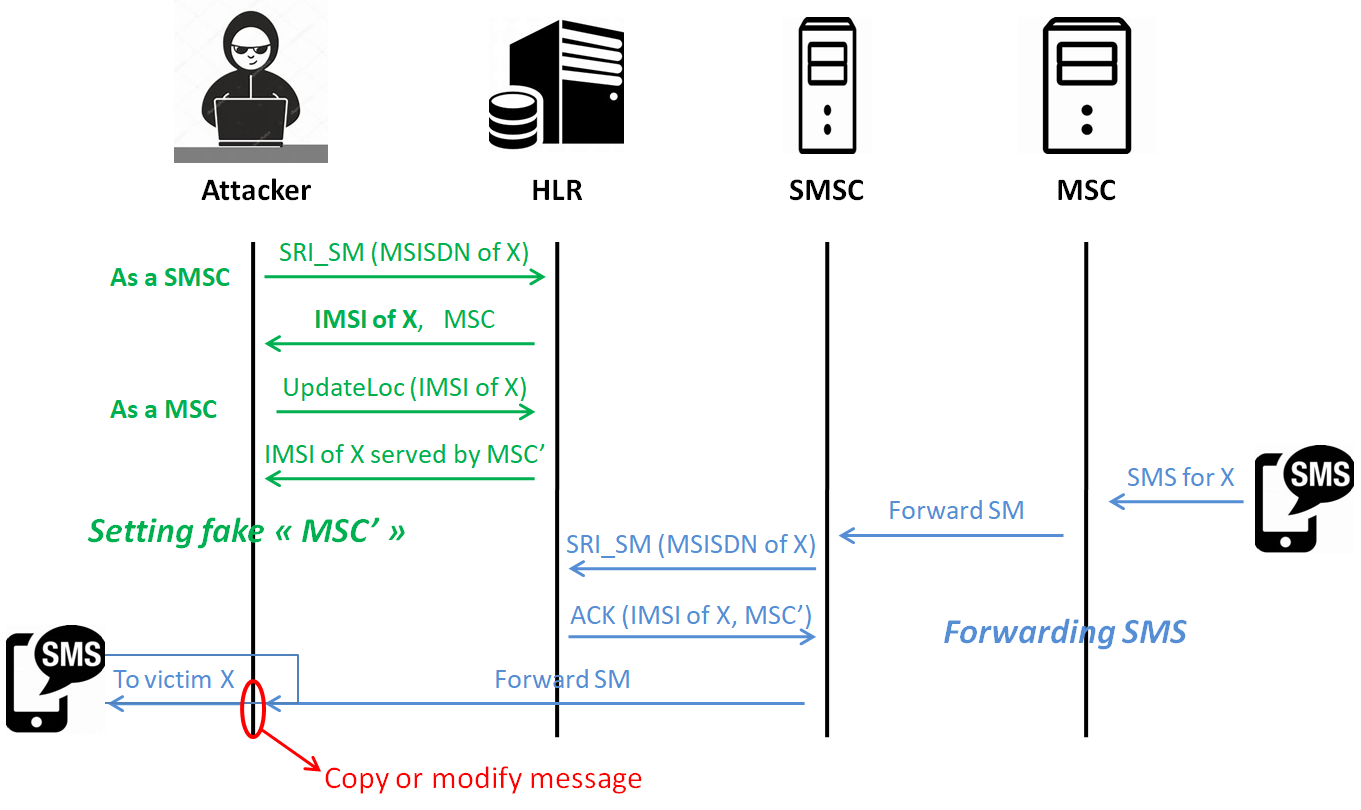
When a subscriber sends a SMS in a 2G network, communication between different equipments occurs thanks to the SS7 MAP (Mobile Application Part) protocol. The Mobile Station (MS: cellular phone) sends text to the Mobile Switching Centre (MSC, routing calls and SMS) in which it is currently located, with the recipient MSISDN (telephone number) and SMS Center (SMSC) address. The MSC sends the message and MSISDN to the SMSC that stores the message for delivery when possible. The SMSC contacts the HLR associated with the MSISDN to learn how to reach the recipient thanks to the MAP operation SendRoutingInfo_forShortMessage (SRI_SM). The HLR is the Home Location Register, a database which stores subscriber information about its current location and the subscription details. The HLR replies to the SMSC with the IMSI (International Mobile Subscriber Identifier) of the recipient and the MSC address where the recipient is located. The IMSI is a unique identifier used in SS7. When possible, the SMSC sends the message to the serving MSC which will forward it to the recipient.
An attacker can have an access to the SS7 network, using some network equipment badly configured, buying a connection from a less scrupulous provider or from the black market, to name a few options. He/She can impersonate as a SMSC and send a MAP SRI_SM message to the HLR of a targeted MSISDN to collect its IMSI and the address of its serving MSC. The HLR will reply since there is no equipment authentication in SS7. Then the attacker can pose as a MSC, providing for this an address that he/she controls, and can send a MAP UpdateLocation operation. This will update the serving MSC associated with the victim MSISDN stored in the HLR. When a SMS is sent to the victim, it is forwarded to the MSC controlled by the attacker who can copy, modify and forward it to the actual recipient, realising a Man-In-The-Middle attack.
This attack is discreet since neither the sender nor the recipient is aware of the interception. It can be exploited by intelligence or law enforcement services as well as by malevolent people. The first big SS7 exploit with financial consequences, reported in the media in 2017, concerned several accounts of a German bank being drained. The thieves collected user bank account credentials and mobile numbers from malware spammed out to victims’ computer. They got 2FA codes thanks to SMS interception [https://www.mobilepaymentsworld.com/hackers-exploit-ss7-security-flaws-access-german-bank-accounts/].
Final words
SS7 will continue offering its vulnerabilities because the 2G and 3G networks will remain many years to serve older equipments. Many operators reacted in the last years to improve security by activating encryption or by installing SS7 firewalls. The problem is however not solved and new vulnerabilities are regularly discovered. In 4G networks where SS7 is replaced by the DIAMETER protocol, similar vulnerabilities were found, although fewer exploits have been seen so far, probably because SS7 is still much available. These are all reasons to stay prudent with SMS-based 2FA authentication.
This blog post is licensed under
CC BY-SA 4.0