Using LaBrea Tarpit to hinder network scans
Jul 10, 2019 by Thibault Debatty | 3816 views
https://cylab.be/blog/29/using-labrea-tarpit-to-hinder-network-scans
When hackers prepare a network attack, they usually start with a network scan to detect running computers and installed software.
LaBrea Tarpit is a Python script written by David Hoelzer that makes the process more difficult. It has two functionalities:
-
It automatically sends a SYN ACK packet to any incoming "SYN" packets. This simulates that all ports are open on the scanned system.
-
It sends packets with a very small TCP window option to slow down OS and application fingerprinting by the scanner.
Requirements
LaBrea Tarpit currently requires Python 2 and Scapy:
sudo apt-get install python2.7-minimal python-pip
sudo pip install scapyPreparation and usage
Normally, when a computer receives a packet but there is no application listening on this port, the Operating System will send a RESET packet. This is used by network scanners to detect that a port is closed. To work properly, the target system must be configured to not send these RESET packets. This can be achieved using iptables:
sudo iptables -A OUTPUT -p tcp --tcp-flags RST RST -j DROP
sudo python labrea.pyExample
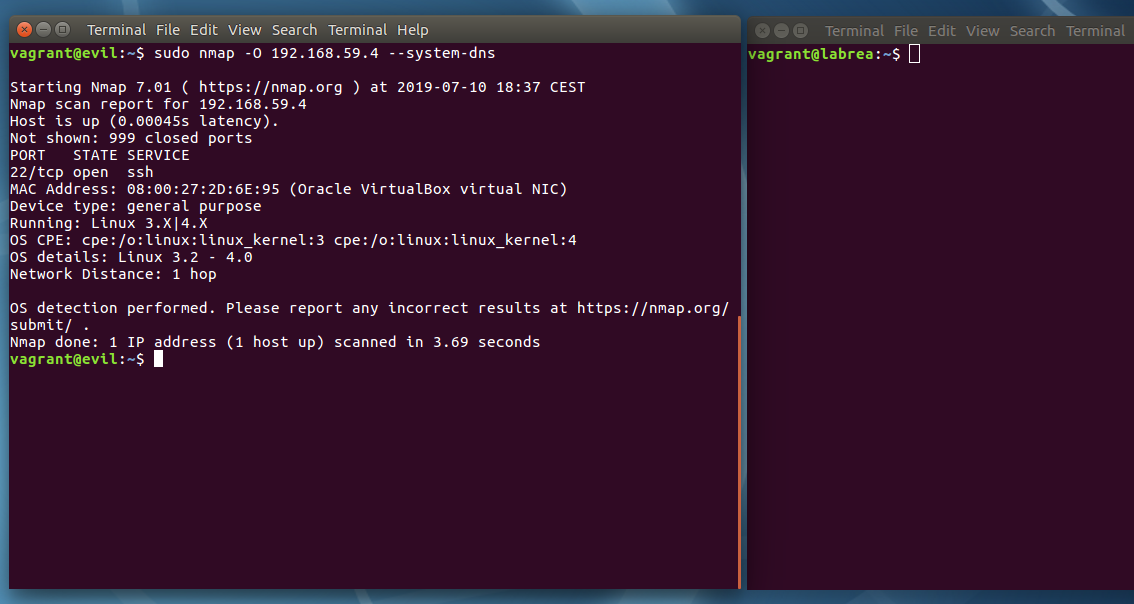
This first screenshot shows a standard scan with nmap. The full machine scan is quite accurate and takes 4 seconds.
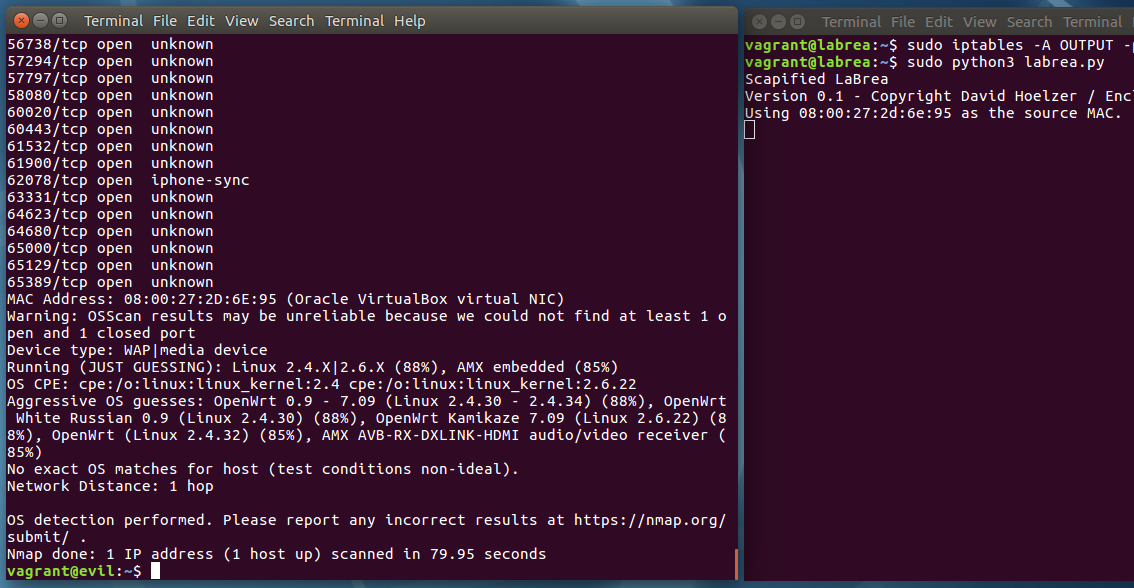
Now we run the same scan, with LaBrea activated. This time the scan is very inaccurate and takes 80 seconds. Hence a 20 fold slow down...
Deployment scenario
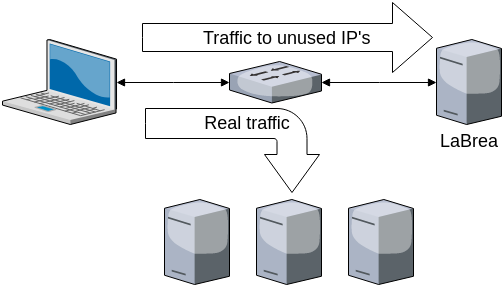
To be more effectif in a real deployment, the computer running LaBrea could be connected to the "copy port" of a switch, and it should be configured to respond to SYN packets sent to any unused IP address.
This blog post is licensed under
CC BY-SA 4.0