OSINT - Simple tips #3 - Google Dorks
Jan 4, 2021 by Alexandre Croix | 5585 views
In the OSINT field, perform good queries in search engines is very important. Search engines collect a lot of data every day and it could be very difficult and challenging to find good information.
A basic query in a search engine produces usually too many results. For example, if you want to find some information about the Cylab unit research in Brussels, you will find more than 2,000 results.
Google (and other search engines) accept different advanced search operators. The following table shows some of the most used operators.
| Operator | Command |
|---|---|
| Quotation mark | “…” |
| Negation | - (dash) |
| Conditional | OR |
| And | AND |
| In Title | intitle: |
| In Body/Text | intext |
| File extension | ext: or filetype: |
| Domain | site: |
| Price (€ or $) | €value |
| Index date | before:YYYY after:YYYY-MM-DD |
Of course, all these operators can be used together for more precise queries.
Use Google Dorks to find sensitive data
These operators allow us to obtain very interesting results on Google (or any another search engine). A well-known query to (maybe) find some Excel spreadsheet containing passwords is:
filetype:xls intitle:password
This query will return xls file with the string “password” in the title of the document. You can combine this query with the domain name of your target by adding site:example.com
Another example:
intext:"INTERNAL USE ONLY" ext:doc OR ext:pdf OR ext:xls
This query will return all files with .doc, .pdf and .xls that contains the exact string INTERNAL USE ONLY
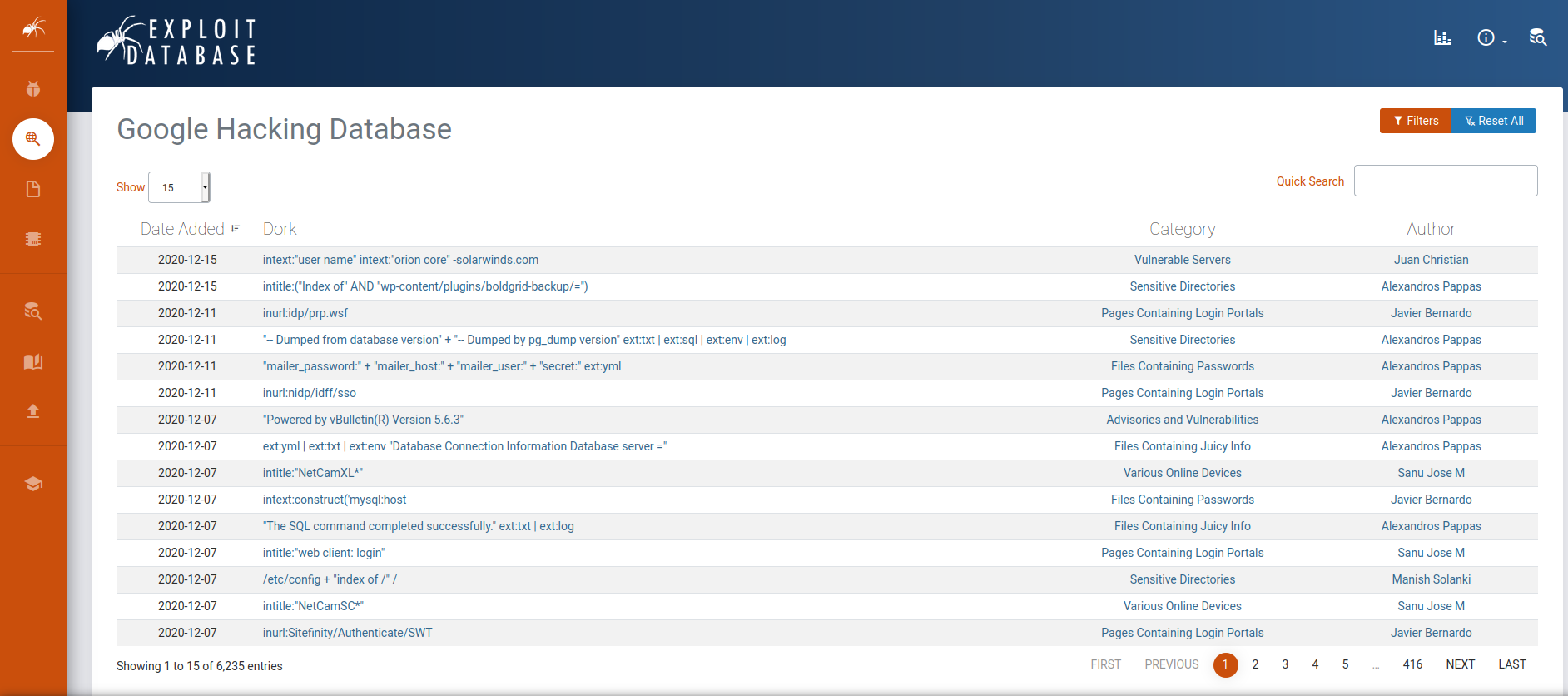
Google Hacking Database
In 2002, Johnny Long created an online database of the most commons Google dorks query. The project is called Google Hacking Database (GHDB) and contains today more than 6,000 queries.
This database is a very valuable resource to find specific information about your OSINT target. It is also possible to use it to find potential issues on the website of your company or project! It is a good practice to test some of the most well-known Dorks on your website to check if it is not leaking sensitive information.
This blog post is licensed under
CC BY-SA 4.0