Check your PHP dependencies for vulnerabilities
Feb 4, 2021 by Thibault Debatty | 5677 views
https://cylab.be/blog/126/check-your-php-dependencies-for-vulnerabilities
Enlightn Security Checker is a composer tool that uses the Security Advisories Database to check your dependencies for known vulnerabilities. It is actually the same database that is used by GitHub Action “PHP Security Checker”. Here is how you can use it locally or with GitLab.
Installation and usage
Installation is a classical composer require:
composer require --dev enlightn/security-checker
To check your dependencies:
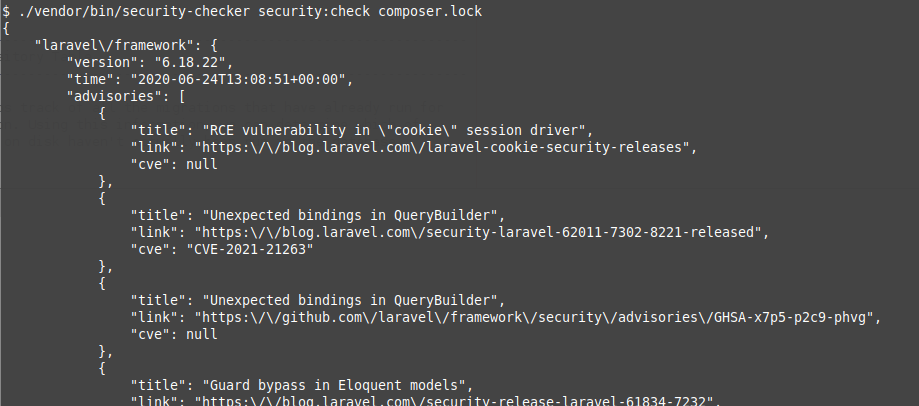
./vendor/bin/security-checker security:check [path/to/composer.lock]
If no vulnerability was found in your dependencies, the tool will simply return with an exit code 0 (and show nothing). However, if one or more vulnerabilities are found it will list the vulnerabilities in json format, and return with an exit code 1.
GitLab
Here is a job you can add to your .gitlab-ci.yaml:
test:dependencies:
image: cylab/php:7.2
script:
# in cylab/php:7.2, security-checker is already installed...
- ~/.composer/vendor/bin/security-checker security:check composer.lock
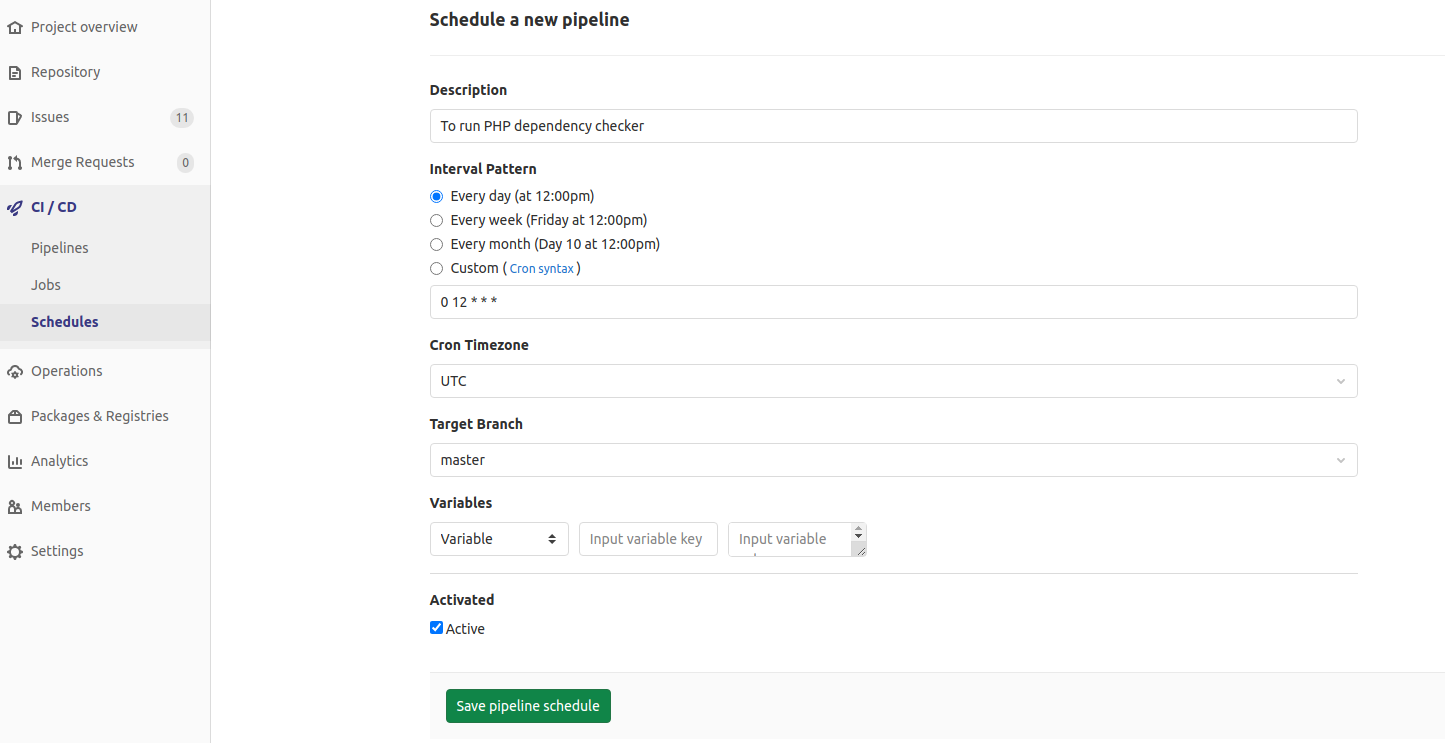
Obviously, new vulnerabilities may be discovered at any time, not only when you push changes to your repository. So you should add a job schedule for your project pipeline in CI / CD > Schedules:
This blog post is licensed under
CC BY-SA 4.0