Change the MAC address of your Linux system
Apr 13, 2021 by Thibault Debatty | 3494 views
https://cylab.be/blog/138/change-the-mac-address-of-your-linux-system
Still today, some network monitoring tools and security systems rely on the MAC address of the host. However, a MAC address is not an authentication mechanism! It can be easily changed. More precisely, by default most operating systems will use the MAC address burnt into the network interface as the source MAC address for all emitted Ethernet frames. But you can easily reconfigure your system to change this behavior. Here is how to do that on a Linux computer.
Command line
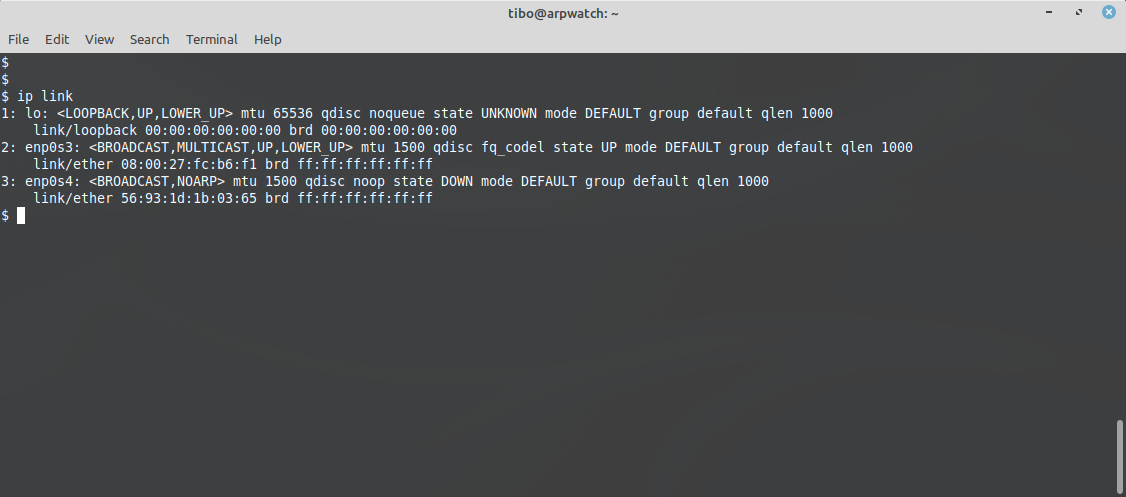
From the command line, let’s list the network interfaces and current MAC addresses:
ip link
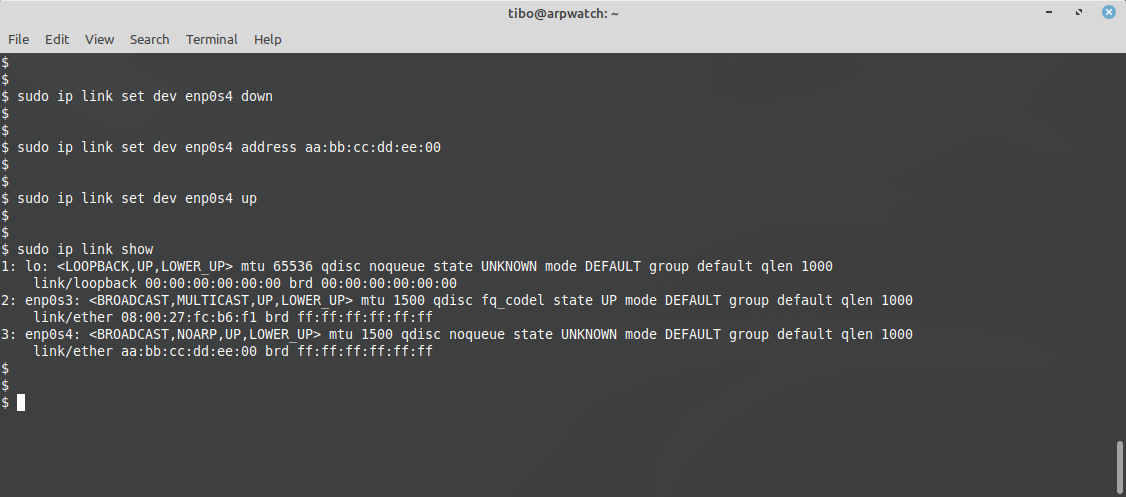
To change the MAC address, we must actually turn the network interface down, then set the MAC address, and finally turn it up again:
sudo ip link set dev <interface> down
sudo ip link set dev <interface> address <XX:XX:XX:XX:XX:XX>
sudo ip link set dev <interface> up
But pay attention, this modification will be discarded after reboot…
machanger
macchanger is a small tool that makes it even easier to change your MAC address from the command line.
Installation is as simple as:
sudo apt install macchanger
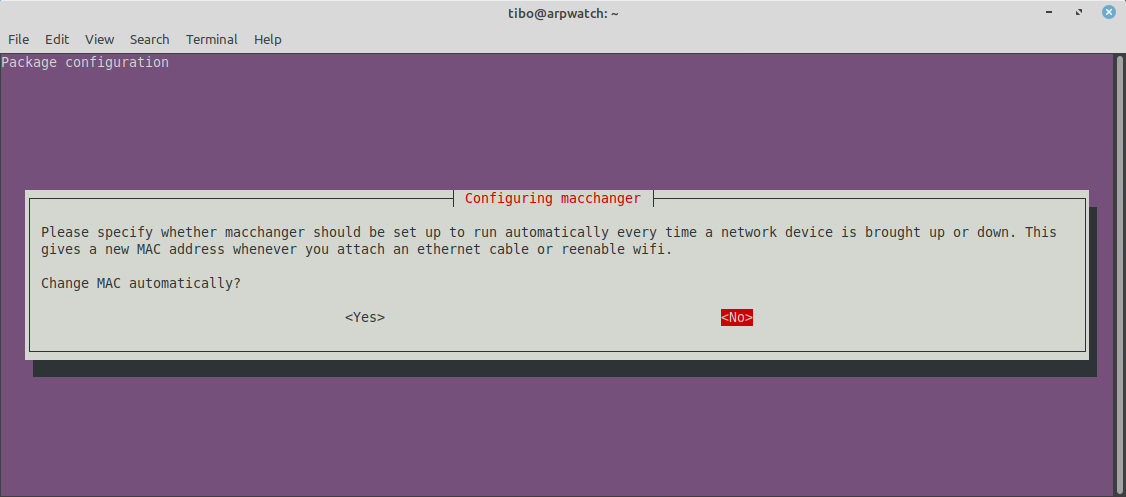
macchanger can change your MAC address each time you plug a network cable or connect to a wifi, but I would not use this feature, so better answer “No”:
macchanger has 3 main commands:
- assign a random MAC address to an interface;
- assign a provided MAC address;
- restore to the default MAC address.
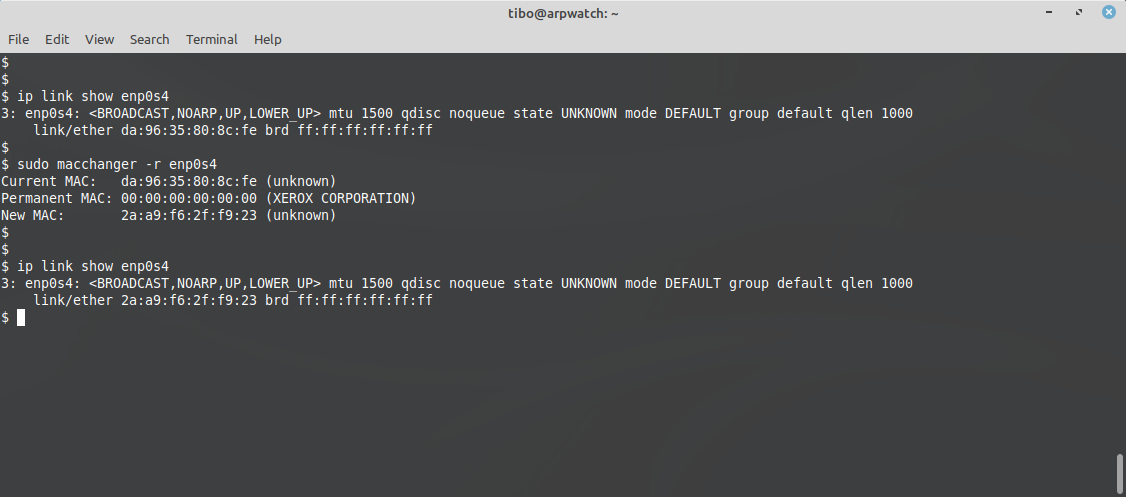
To assign a random MAC address:
sudo macchanger -r <interface>
To assign a provided MAC address:
sudo macchanger -m <XX:XX:XX:XX:XX:XX> <interface>
Finally, to reset the default MAC address:
sudo macchanger -p <interface>
This blog post is licensed under
CC BY-SA 4.0