MITRE ATT&CK and the ATT&CK Matrix
Apr 7, 2022 by Georgi Nikolov | 4205 views
Defining cyber attacks is a difficult task. They vary in origins, goals and, at first glance, the techniques used might seem very different. Luckily a popular model was defined by Lockheed Martin, still used to this day, which illustrates very well the lifecycle of a typical cyber attack. The Cyber Kill Chain, popular but controversial, defines the 7 principal steps of an attack. There have been many advances, since its original conception, one of which is the wildly acclaimed ATT&CK Matrix for Enterprise.
The Cyber Kill Chain
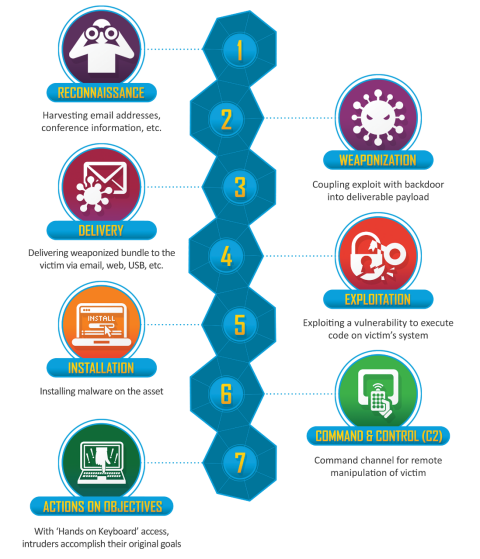
The Cyber Kill Chain was conceived as an adaptation of the military’s kill chain, a step-by-step approach that identifies and sets countermeasures to stop enemy activity. Its goal is to map and define the intricate steps, that sophisticated cyber attacks may undertake to bypass or neutralize defense systems. Such attacks have become more and more common of late, as hacker groups have developed more elaborate tools and on many occasions have been sponsored or even established by governments, to help them gain a foothold in the ever persistent war on information. Advanced Persistent Threats (APTs) are defined in the scope of the Cyber Kill Chain as multi-stage attacks, where the adversaries will spend a large portion of their time collecting information through surveillance and social engineering, before crafting dedicated attack vectors, which they will use to penetrate their target and exploit its vulnerabilities. At this stage a remote connection will be established, better known as a Command & Control channel, where the hackers have direct control over the compromised systems and they can accomplish their objectives. First defined as early as 2011, many advancement on the side of the attackers and defenders have made it so the Kill Chain became too simplistic and needed to be expanded.
MITRE ATT&CK
The Mitre Corporation is an American not-for-profit organization, centered around management of research and development, supporting various U.S. government agencies in various fields. In 2015 the MITRE ATT&CK framework was launched, described in their own words as:
MITRE ATT&CK is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations. The ATT&CK knowledge base is used as a foundation for the development of specific threat models and methodologies in the private sector, in government, and in the cybersecurity product and service community.
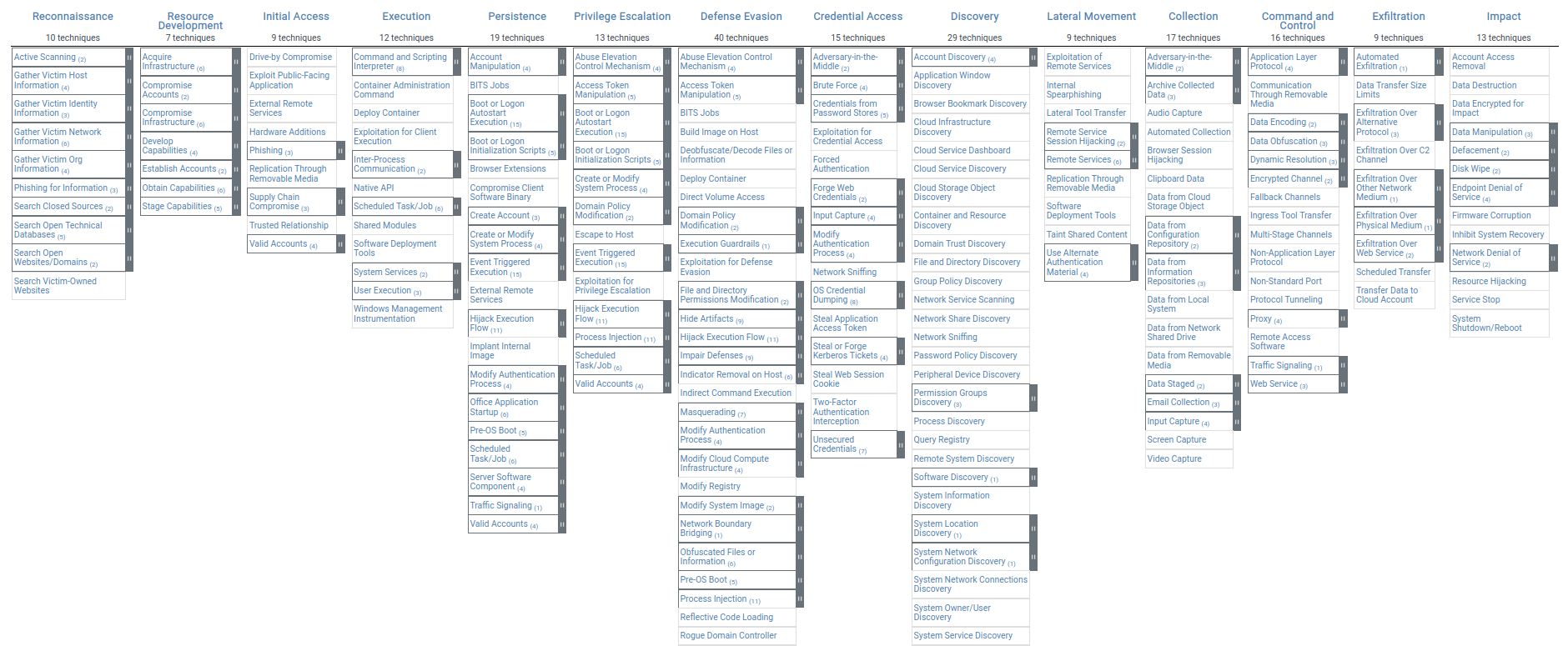
In simpler terms, the MITRE ATT&CK offers a huge catalog of information on various cyber attack techniques, collecting research detailing examples of how these techniques have been used in the past and offering possible solution to defend against them. To better organize and visualize the huge amount of data, the ATT&CK Matrix was developed, a powerful tool, which security experts and researchers can use to quickly find concrete information.
As we can observe, the ATT&CK Matrix is closely based on the Cyber Kill Chain, expanding it, largely in the steps taken by adversaries once they have gained access to a system. The initial 7 steps of the Kill Chain have grown to 14 steps, elaborating more in-depth how hackers would establish and maintain a Command & Control channel to the compromised machine. To do so, the malicious actors will more often than not pass through various stages, some of which are:
- “Establishing Persistence” - find a way to be able to reconnect to the compromised machine if the initial connection is interrupted. This can include, for example, the installation of back-doors or accessing account information
- “Privilege Escalation” - usually a typical system user does not have Administration privileges for their own and the network’s security. The adversaries will often try to find a way to get these privileges to be able to install programs or manipulate the system for their goals
- “Discovery” - once inside a system, the hackers need to gather information on the users of the machine, the topology of the network and any other services that may be present, giving them more options for spreading deeper into the network (which would lead to “Lateral Movement”). By collecting this information, they can also discover if there are more vulnerabilities present, which they can exploit in the future
The great thing about the ATT&CK Matrix is that it does not only present all the possible techniques in a more digestible view, but if we want to dig deeper, we can navigate the different techniques to get more information about them.
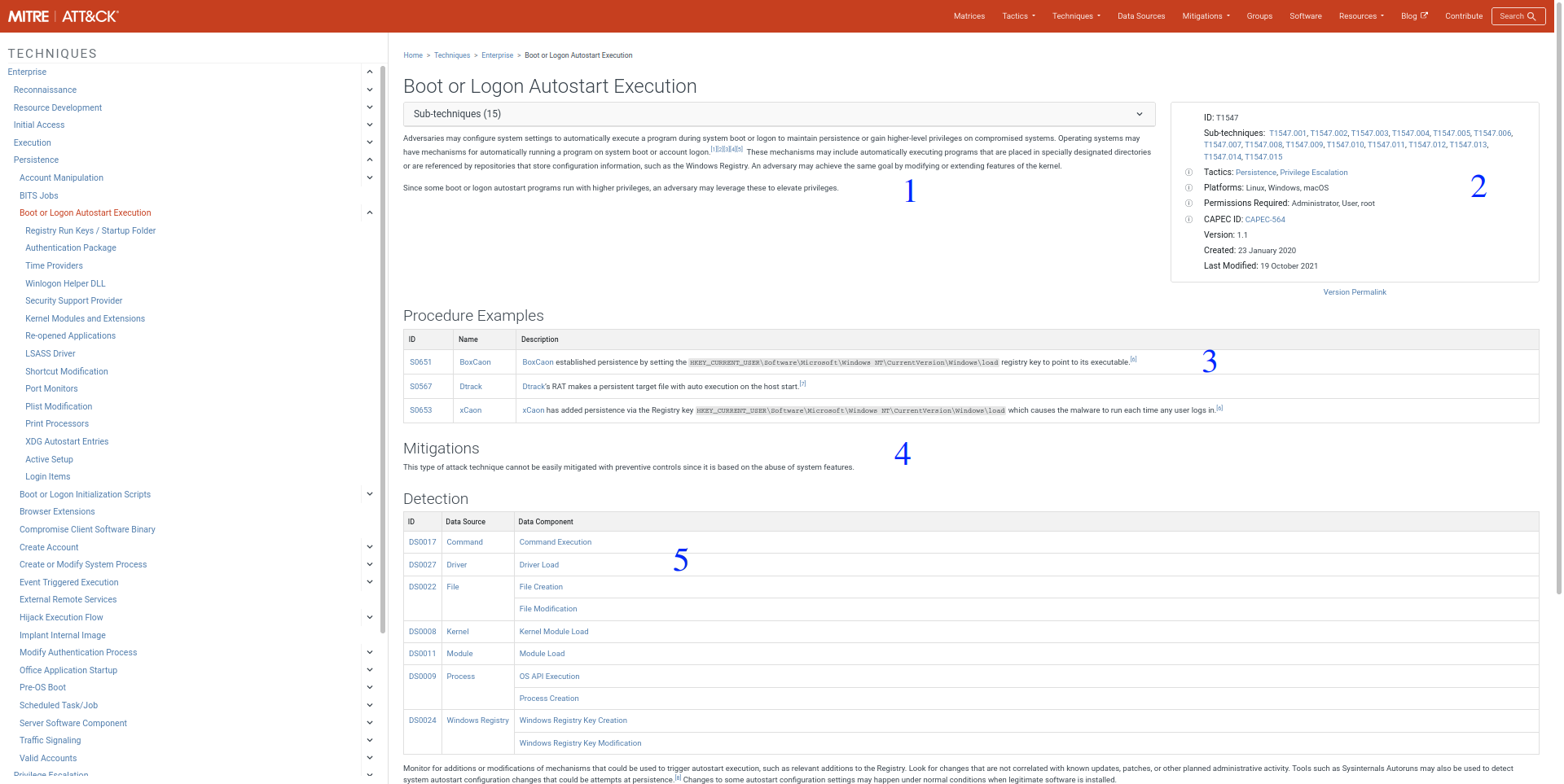
An in-depth overview of each technique is provided, separated in couple of major key points:
- General description and use of the technique.
- General overview of the techniques characteristics, such as the family of Tactics it belongs to, possible susceptible platforms, etc.
- Examples of the technique used by real APTs, usually defined by an ID and the name of the APT group responsible.
- Mitigation techniques, which can be used to defend against it.
- Detection techniques, ways to detect this specific attack technique through various system analysis
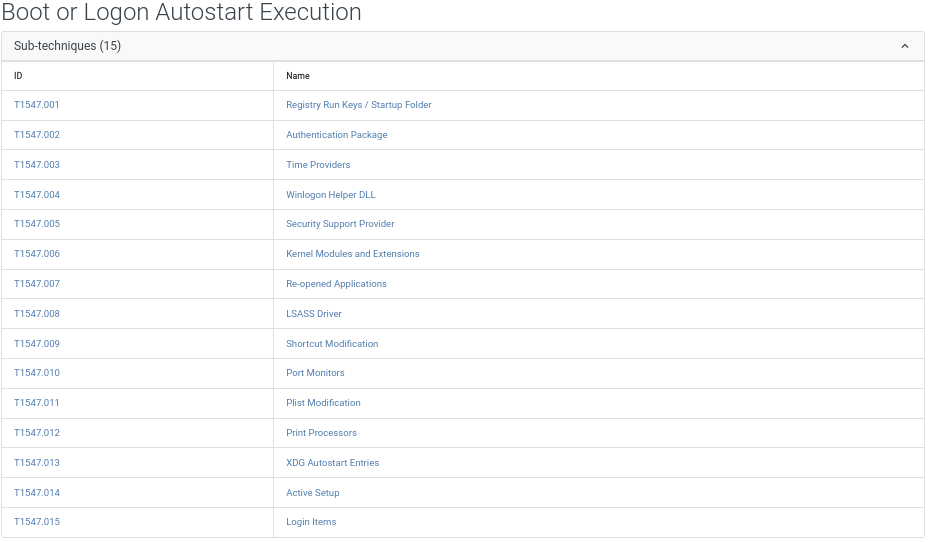
There is also the possibility to view precise listing of the sub-techniques, various ways this technique can be actually applied in the real-world. The sub-techniques are defined in the same way as their parent, detailing in-depth how they are implemented, examples of use, mitigation techniques and detection possibilities.
Each page also contains a collection of various references, which can also be viewed to gather even more information on it.
Final Words
The MITRE ATT&CK framework has become a cornerstone of cyber security, offering an open-source service for awareness training, risk mitigation and attack detection and prevention. It has grown into a global knowledge base, used by a multitude of agencies across the world, and continues to grow with each passing year. The community also organizes a conference, dubbed “MITRE ATT&CKCON“, showcasing speakers from around the world and helping grow the awareness and introducing people to new ways to use the framework to better defend themselves and their organizations.
This blog post is licensed under
CC BY-SA 4.0