Network reconnaissance with arp-scan
Jun 5, 2022 by Thibault Debatty | 15236 views
https://cylab.be/blog/220/network-reconnaissance-with-arp-scan
arp-scan is a simple tool that can be used list the IP addresses (and devices) used in a network. It works by sender ARP ‘who-has’ requests for every IP address of the subnet. If the IP address is used by a device, it will reply with an ARP ‘reply’ packet.
Installation
arp-scan is available in the repositories of most distributions:
sudo apt install arp-scan
Usage
You can run a scan from the command line. The only caveat is that you should indicate the network interface on which arp-scan must send the ARP requests:
sudo arp-scan -I <interface> <subnet>
For example:
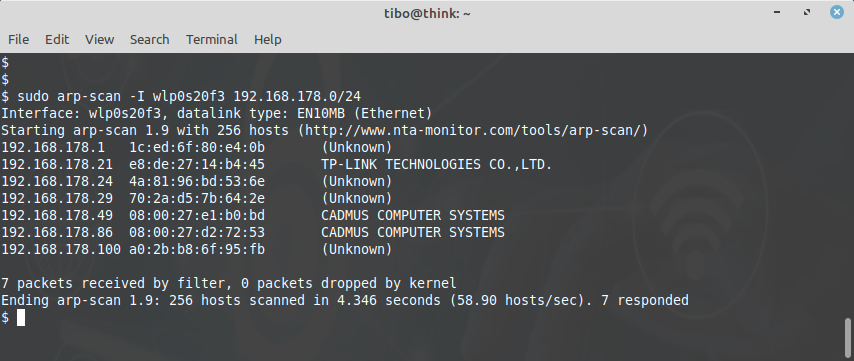
sudo arp-scan -I wlp0s20f3 192.168.178.0/24
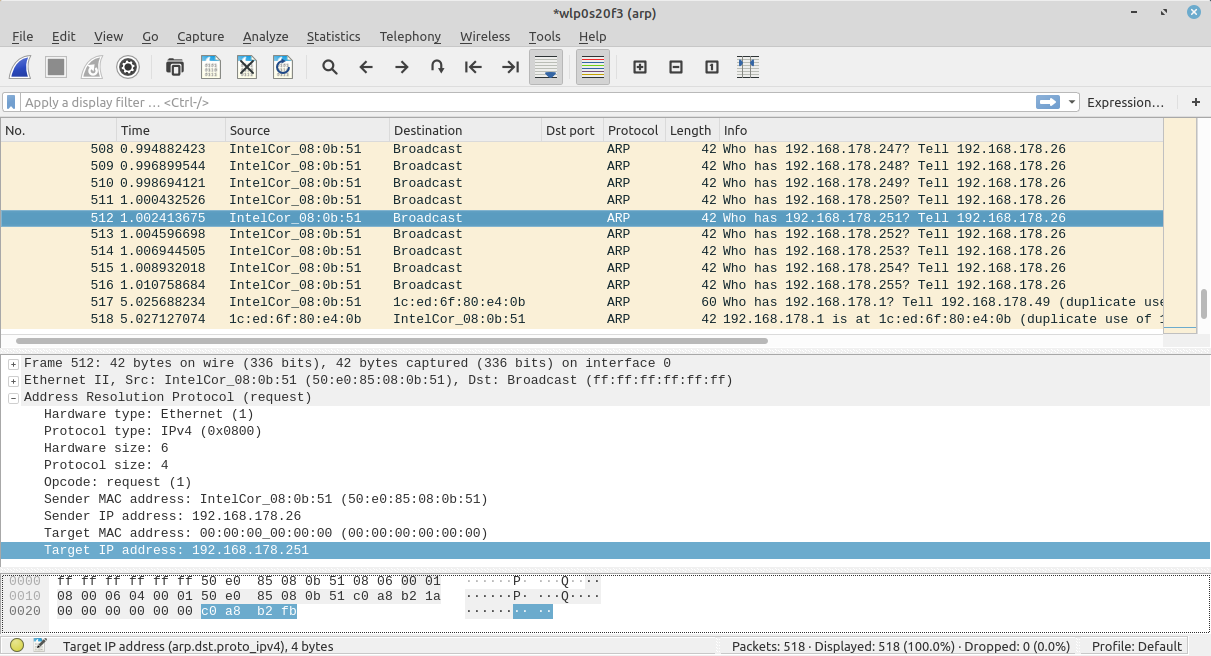
To list devices, arp-scan will send a series of ARP request packets.
The result will show the MAC address and manufacturer of each device, like on the screenshot below:
Database update
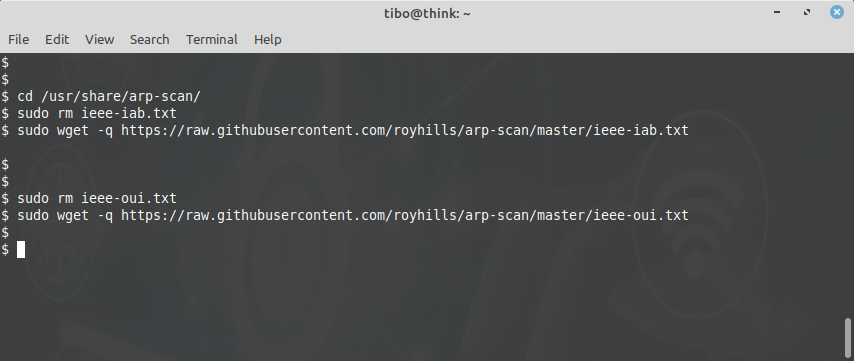
As you may know, the 3 first Bytes of a MAC address allow to find the vendor of a network interface (unless the administrator has manually changed the MAC address of the device). This block of 3 Bytes is called the Organizationally Unique Identifier (OUI). arp-scan uses a database to find the manufacturer of each device. You can update this database by downloading the latest version directly from the GitHub repository of the project:
cd /usr/share/arp-scan/
sudo rm ieee-iab.txt
sudo wget -q https://github.com/royhills/arp-scan/raw/master/ieee-iab.txt
sudo rm ieee-oui.txt
sudo wget -w https://github.com/royhills/arp-scan/raw/master/ieee-oui.txt
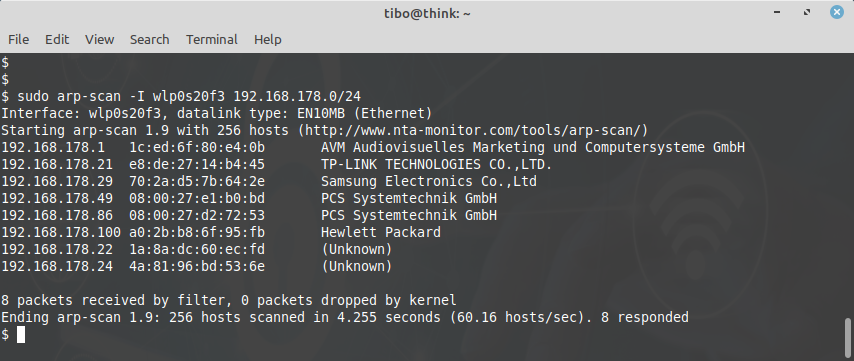
This time, you should get more information about the different vendors:
Individual Address Block (IAB)
As you may have noticed, we downloaded 2 files to update the arp-scan database: the OUI and the IAB. The IAB is a legacy system, similar to the OUI, but where each manufacturer receives a block of only 12 bits. Hence a single IAB allows to assign a unique MAC address to maximum 4096 (2^12) network interfaces.
This blog post is licensed under
CC BY-SA 4.0