Analyse of a crypto scam
May 6, 2024 by Arnaud Stoz | 1310 views
If you ever connected to a discord server related to ethereum (geth, ethereum.org) you probably noticed that despite very useful information given about the technology, those servers are also unfortunately full of scammer… Let’s have a look at one of them and analyze the scam it proposes.
Scammer methodology
The methodology of those scammers are really simple and can be resumed to the following
- They will contact you by private message pretending to be from the support team.

- If you show a little of interest, they will redirect you to a website where you will be asked to connect your wallet. They will ask you to input all your information about your wallet. This information includes:
Website analysis
Now that we know a bit more the methodology used by those scammers, let’s analyze it.
When looking at the page source we notice that clicking on the button call the function sendEmail().

Let’s have a look at the sendEmail function
 We have a lot of interesting insight of how the website is working.
We have a lot of interesting insight of how the website is working.
- first it check if the value input is matching certain condition. If not it shows a pop-up to kindly ask to complete correctly all data
- then it sends an email to a hardcoded recipient with a hardcoded sender. It uses the smtpjsV3 for sending an email.
We now have a good understanding on how the scam is working. It tricks the victim to enter his wallet details and send them via email from a hardcoded address to a hardcoded receiver.
By replacing the receiver address to a temporary email address in our control we can have a look at the email received by the attacker.
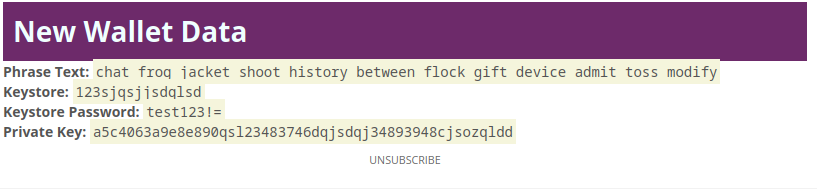 .
.
⚠️ Disclaimer
Once a scammer has been identified, the best thing to do is to report it to all the services used by this scammer.
The next part is explained purely for educational purpose, to show how javascript can be manipulated to completely change the behavior of a page.
⚠️ Do not reproduce, simply report all scam to appropriate service.
Manipulating Javascript
Now that we have all the information about the scam, let’s have a deeper look at the smtpjs library.
The smtpjs rely on elasticemail to works properly.
Having a look at the elasticemail we can see it is a paid service used to send and manage marketing email campaign.
We can then use the account created by the scammer to send him a lot of email with fake credentials.
Simply by modifying the code of the sendMail function, we can remove the check on the input and put the Email.send call in a for loop.
Once the code is modified we can click the button. After some email sent, we receive the following message:
Service not available, closing transmission channel. The server response was: 026aac1d-071a-426f-b432-1e41d73ad719 Error: 421 Error: Not enough credit.
That means all the credit bought by the scammer to send email has been exhausted. Nobody else can be scammed using this specific website.
In the meantime, the scammer has been reported to the appropriated service, namely smtpjs and discord
Conclusion
As we have seen here, this scam is very basic
- it asks for credentials of the user on the web page with a basic javascript in it.
- Then send an email to the scammer container the credentials entered on the webpage.
When dealing with blockchain technology on discord, please remember:
- ** Do not trust any support guy contacting you via DM**
- ** Report any scam you identify**
- Never ever share your private key or recovery phrase with anybody
This blog post is licensed under
CC BY-SA 4.0