Design and Implementation of a Naval Cyber Range for Cybersecurity Awareness and Research
Sep 3, 2025 by Louis-Henri Laquay | 1229 views
▶ Watch the Demonstration Video of the Naval Cyber Range
This post presents a condensed overview of the research and development conducted as part of a master thesis on maritime cybersecurity. The work focuses on the design and implementation of a naval cyber range tailored for training and research purposes, with particular reference to the new Belgian Mine Countermeasure (MCM) warships. By simulating realistic shipboard network environments and integrating cyber-attack scenarios, the project aims to raise awareness and improve resilience against cyber threats in the naval domain.
Introduction
The digital transformation of modern warships has created highly connected environments where navigation, propulsion, and mission systems depend on integrated IT (Information Technology) and OT (Operational Technology) infrastructures. While this enhances operational capability, it also introduces growing cybersecurity risks. High-profile incidents, such as the NotPetya attack on Maersk and GPS spoofing in critical waters, underscore the need for increased maritime cyber preparedness.
However, realistic environments for training and research remain limited. Existing cyber ranges rarely reflect the complexity of naval systems or operational contexts. To address this, the thesis presents the design of a modular, resource-efficient Naval Cyber Range that simulates the digital architecture of a Mine Countermeasure (MCM) warship. It supports scenario-based training and controlled cyber attacks while enabling future research, including AI-based threat detection.
Problem Statement and Objectives
The upcoming Belgian MCM vessels rely on a complex digital ecosystem that, while operationally effective, presents significant cyber vulnerabilities. No existing simulation platform accurately models such environments, and real-world testing remains impractical due to cost, security, and classification.
This thesis proposes a realistic, modular cyber range for simulating onboard ship systems and representative network behaviour. It enables cyber awareness training, threat injection, and future integration with research tools. The platform prioritizes flexibility and extensibility while maintaining operational relevance.
Deliverables include a working prototype, a scenario library, and an open architecture. Although simplified and focused on onboard systems, the platform provides a strong foundation for both training and academic research.
Research Gaps and Opportunities
Current maritime cyber ranges are often costly, hardware-dependent, and poorly suited for national defence applications. This work addresses those gaps by offering an affordable, fully virtualized alternative tailored to Belgian Defence needs.
It builds on architectural best practices, such as using ship simulators, virtual IT/OT networks, and modular control systems, and emphasizes hands-on, scenario-driven training. While the open-source MaCySTe (Maritime Cyber Security Testbed) project from the university of Genoa [1] provides a useful starting point, it lacks naval focus and multi-user support. Selected components are adapted to meet the specific needs of naval training and experimentation.
These insights guide the development of a lightweight, scalable, and mission-relevant cyber range platform.
Simplification of the MCM Warship Network Architecture
A central contribution of this thesis lies in the abstraction and simplification of the highly complex and classified network architecture of the new Belgian Mine Countermeasure (MCM) warships. Drawing on restricted-distribution technical documentation provided by Naval Group [2-6], the work presented in this study distills the essential characteristics of the vessel’s cyber environment into a form suitable for simulation within a naval cyber range.
The real-world architecture of the MCM warships includes:
- Over 40 servers
- More than 100 virtual machines (totaling over 400 vCPUs)
- Approximately 20 operator consoles
- Around 30 distinct shipboard systems
- 10+ routers and 40+ switches
Reproducing this structure in full fidelity would be infeasible for research purposes due to resource constraints, system complexity, and classification restrictions. To address this, a carefully designed simplification strategy has been applied, preserving key operational domains and data flows while dramatically reducing technical overhead.
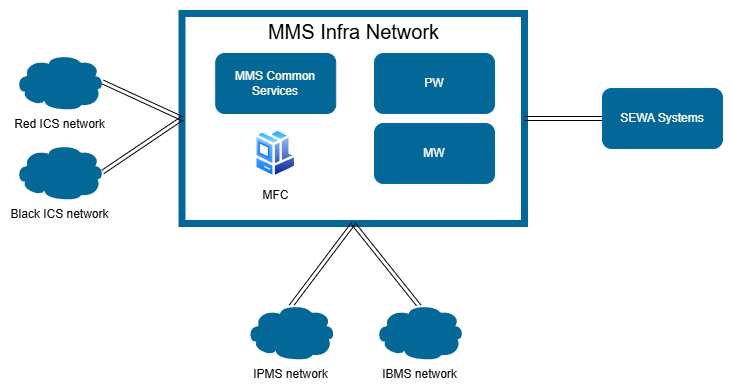
The resulting simplified architecture of the warship network consists of:
- 11 servers
- 4 routers
- 15 switches
As shown in the scheme, these elements are organized around a central backbone network dedicated to mission management (Mission Management System, MMS) and the integration of Sensors and Weapon systems (SEWA) used in combination with the Principal Warfare (PW) and Mine Warfare (MW) systems. This core network is interconnected with four distinct subnetworks, each designed to emulate a key operational domain of the warship:
- Black Integrated Communication System (Black ICS): for handling unclassified military communications.
- Red Integrated Communication System (Red ICS): supporting classified military communications.
- Integrated Platform Management System (IPMS): responsible for platform control and interaction with Operational Technology (OT) systems.
- Integrated Bridge Management System (IBMS): hosting the ship’s navigation and bridge management systems.
This network organisation reflects the functional segmentation of a modern warship while remaining practical for research and training. The simplification preserves key interdependent functionalities, navigation, propulsion, surveillance, and communication, enabling scalable simulation, realistic threat modelling, and effective scenario-based cyber awareness training.
Simplification Strategy and Implemented Systems
To ensure feasibility and maintain pedagogical focus, the naval cyber range adopts a simplified model of a Mine Countermeasure (MCM) warship. While based on real ship architecture, the simulation omits general-purpose IT infrastructure and reduces network complexity to facilitate deployment and experimentation.
Key simplifications include:
- Replacing Multi-Function Consoles (MFCs) with standard Linux machines.
- Omitting firewalls, VLANs, Active Directory, and deployment systems.
- Abstracting weapon systems, secure communications, and time synchronization.
Despite these abstractions, the simulation retains essential naval logic (e.g., platform control and mission management), enabling realistic training while supporting modular expansion.
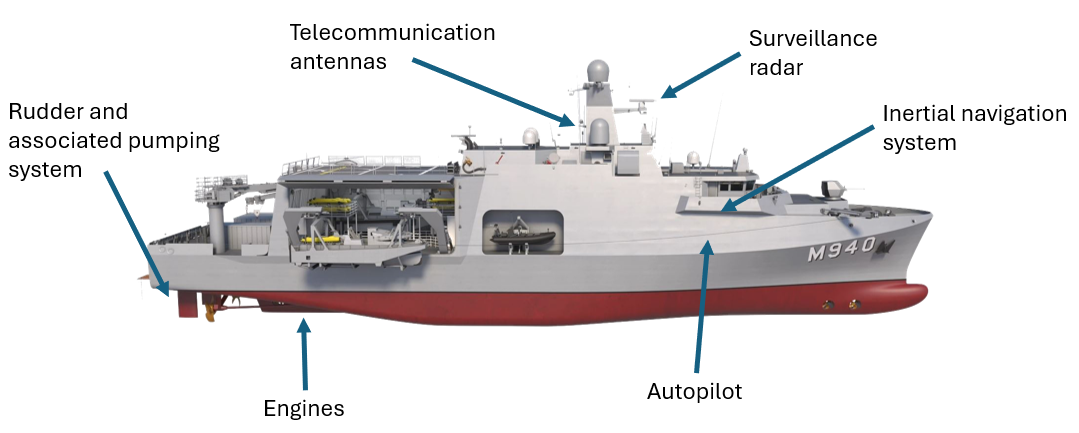
Simulated Ship Systems and Protocols
A representative set of shipboard systems has been implemented including radar, autopilot, steering gear, propulsion, and navigation displays. Each system preserves core behaviors while remaining lightweight and adaptable.
The architecture leverages real maritime communication protocols to ensure coherence and realism:
- NMEA 0183 for navigation and autopilot data,
- Modbus TCP for engine and PLC communications,
- ASTERIX and Navico BR24 for radar transmissions.
This ensures domain-specific traffic patterns, supporting meaningful scenario-based training and cybersecurity experimentation.
Platform Selection and Simulation Requirements
To support the design and implementation of the naval cyber range, both platform-level and simulation-level requirements were formulated based on technical objectives, available hardware, and lessons from related work.
Platform Requirements
The simulation platform must provide:
- Ease of deployment and maintenance, enabling rapid prototyping and limited configuration overhead;
- Extensibility and exportability, allowing future upgrades and external reuse;
- Low cost, preferably relying on open-source or freely available solutions;
- Graphical user interface for intuitive management;
- Support for virtual machines and network devices for realistic emulation of shipboard components.
Simulation Needs
To meet training and experimentation goals, the simulation environment must provide:
- Configurable networking to replicate ship-specific communication paths;
- Custom resource allocation, including CPU and RAM per VM;
- Graphical access to user interfaces, enabling trainee interaction with simulated systems.
Selected Platform: EVE-NG
After evaluating several options, EVE-NG (Emulated Virtual Environment - Next Generation) was selected as the most appropriate platform. It achieves a balance between realism, modularity, and efficient resource usage. EVE-NG provides:
- A unified emulation environment for VMs and network devices;
- Precise emulation of network behaviour, essential for realistic naval scenarios;
- Long-term adaptability through a modular architecture;
- An intuitive Graphical User Interface (GUI) and community edition availability, eliminating licensing costs.
The chosen deployment is based on a dedicated server featuring 24 vCPUs, 128 GB of RAM and 10 TB of storage, which provides sufficient capacity for multi-component scenarios. In future phases, the platform can be extended with clustering or upgraded to the Pro Edition to support additional features such as multi-user environments.
Implementation of the Naval Cyber Range
Now that the systems to simulate and the simulation platform have been identified, the key remaining question is: how can we simulate the behavior of a warship’s digital systems in a way that is both realistic and efficient?
Design Principles and Architecture
Two main challenges arise: how to keep the simulation resource-efficient while reflecting realistic shipboard network behavior, and how to generate and deliver coherent operational data to all onboard systems involved in the simulation.
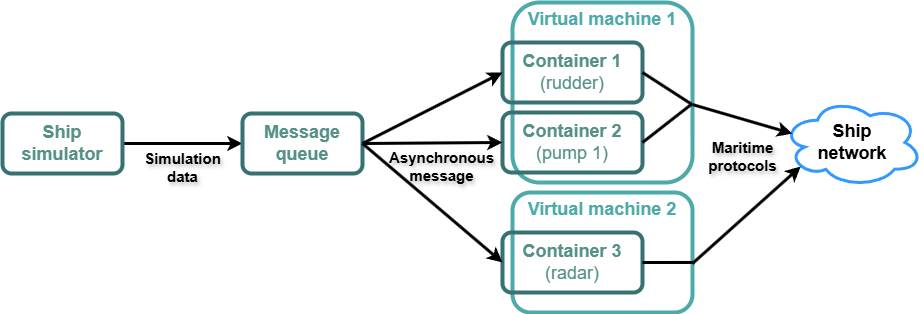
The solution adopted in this project relies on the principle of a centralized ship simulator, based on the open-source Bridge Command software, connected to a separate internal network dedicated solely to simulation purposes. This simulator produces realistic data such as the vessel’s position, heading, speed, and radar outputs. This data is then distributed to all other simulated systems across the network.
To efficiently manage computing resources, the systems of the ship are implemented using a combination of virtual machines (VMs) and lightweight containers. Each virtual machine can host several containers, each representing a specific function or subsystem of the ship (e.g., rudder control, radar interface, navigation). These containers communicate with the ship simulator via a dedicated message queue, receiving only the data they need to function and injecting their outputs back into the simulation.
To create a seamless experience, traffic between containers is injected into the network using real maritime communication protocols. Each container has a unique IP address, so any external observer analyzing the network would see data exchanges that resemble those of an actual ship. This approach greatly enhances realism while keeping the infrastructure lightweight and scalable.
The simulation also includes additional services such as internet access, web browsing, internal emails, and internal DNS resolution to support realistic user interactions and cyber training scenarios.
Use of Existing Components and Open Source Distribution
Several components of this project are based on modules initially developed by the MaCySTe project (Maritime Cyber Security Testbed) led by the University of Genoa. [1] These components were adapted and redistributed across the different virtual machines to match the architecture of a modern naval vessel.
All source code, configurations, and setup scripts for the current project are publicly available under the GNU Affero General Public License (AGPLv3) on GitHub at the following address:
https://github.com/LaquayL/RMA-Naval-Cyber-Range
Exportability, Modularity, and Extensibility of the Project
Throughout the design and development of the naval cyber range, a strong emphasis was placed on making the platform fully exportable, modular, and extensible. These characteristics were essential to ensure that the solution could evolve over time, adapt to new research goals, and support operational training in various contexts.
From the outset, the project was structured to support:
- Rapid deployment on new hardware or simulation platforms.
- Easy addition of new modules or shipboard systems.
- Integration of new cyber threats and attack vectors.
- Creation and customization of cyber-awareness scenarios.
This flexibility ensures that the naval cyber range can be reused, shared, and adapted across different use cases and institutions. Whether the goal is to develop new technical components, expand existing capabilities, or run awareness missions in new operational environments, the platform is ready to support these future needs with minimal rework.
Overview of the Graphical Interfaces
To support cyber awareness training, several user interfaces have been designed to simulate realistic roles on board a modern ship. Based on the shipboard systems selected in this project, three operational roles were defined: radar operator, engine and rudder operator, and chart (WECDIS) operator. Each role is linked to a dedicated desktop virtual machine within the EVE-NG platform.
In addition to these interactive roles, two other graphical interfaces are available: one for the cyber range manager, and another for observing the bridge view of the ship simulation. These are not intended for trainee interaction, but they help coordinate and contextualize the training.
Role-Based Interfaces for Crew Members
Each of the three crew roles has access to one or more web interfaces depending on their assigned responsibility:
Radar Operator: Monitors radar contacts using two interfaces based on different radar protocols.
Engine and Rudder Operator: Controls the ship’s propulsion and steering via navigation panels, controls the autopilot (heading, tracking and speed modes) and monitors the Steering Gear System (SGS).
Chart Operator (WECDIS): Follows the ship’s position and track on an electronic nautical chart, and can define navigation routes.
These interfaces are accessible from within the simulated network using simple URLs. Each trainee focuses only on their assigned tools, helping them stay immersed in their specific role during the scenario.
Ship Simulation Display
Although trainees do not directly control the ship through the simulator, a visual interface is available showing the vessel’s perspective from the bridge, as generated by the simulation software (Bridge Command). This display can optionally be projected for all participants to enhance realism.
Cyber Range Manager Interface
A separate interface is provided for the cyber range manager, who oversees the scenario. This interface allows the manager to trigger and supervise simulated cyberattacks during the training session. It is only accessible from a dedicated management machine that is not part of the ship network.
This control interface is modular, allowing new attacks and targets to be added easily in future scenarios.
Overview of the Cyber Awareness Scenario
To demonstrate the capabilities of the naval cyber range, a complete cyber awareness scenario has been implemented. This scenario serves as a proof-of-concept, designed to replicate a plausible cyber intrusion in a naval environment while remaining accessible to non-specialist trainees. Its objective is to train users to recognize signs of compromise, respond appropriately, and gain insight into typical attack patterns targeting IT and OT shipboard systems.
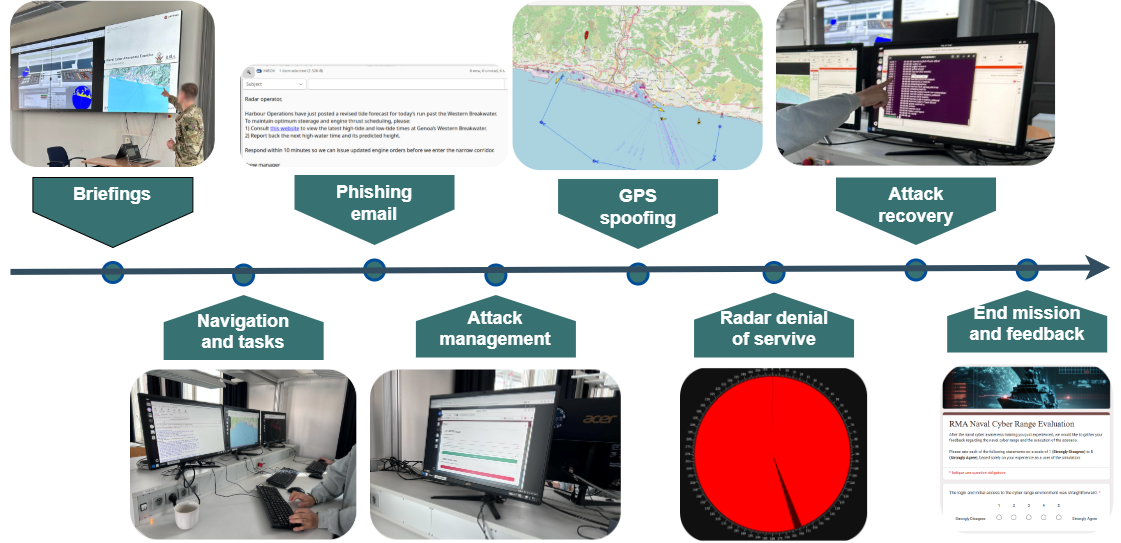
The scenario is structured to reflect a realistic cyber attack progression, beginning with an initial infection via phishing and culminating in the disruption of operational shipboard systems. The cyber attack is composed of the following main stages:
-
Initial compromise: A phishing email is sent to the radar operator. Upon clicking a malicious link, a malware installer is downloaded and executed, deploying the malware in the background.
-
Command and control (C&C) activation: Once installed, the malware establishes contact with a command and control server, enabling remote access and activation of predefined attacks by the cyber range manager.
-
Lateral movement: The attacker uses the infected radar machine to pivot to a more critical system, the Integrated Bridge Management System (IBMS) server, extending their reach to additional operational data, including navigation signals.
-
Attack execution: Two main attacks are launched: a GPS spoofing attack that misleads the WECDIS operator about the ship’s position, and a denial-of-service attack that floods the radar display with fake signals, rendering it unusable.
-
Trainee response: Trainees must detect the presence of the malware, stop the malicious process, identify and secure malware files, and investigate system logs to reconstruct the attack sequence.
The scenario is carefully balanced to ensure both technical realism and pedagogical clarity, taking IT officers as target audience. It highlights key phases of cyber operations, such as social engineering, process monitoring, lateral movement, and OT disruption, while encouraging trainees to apply basic forensic and incident response techniques. This structure makes it ideal for awareness training sessions and offers a reusable template for future scenario development.
Evaluation
System Performance and Resource Usage
The evaluation of the naval cyber range highlights CPU availability as the main performance constraint. Despite the use of lightweight containers to reduce the number of required virtual machines, the full simulation still demands around 20 CPU cores to operate effectively. The current hardware, offering 24 physical cores, limits the potential for further expansion or increased trainee concurrency.
In contrast, memory and disk usage remain well within safe limits. The system’s 128GB of RAM and 10TB of storage are sufficient to support current operations and allow room for added complexity or future developments. Overall, while CPU usage can peak significantly during intense activity, the platform demonstrates stable performance suitable for its intended training and research purposes.
Training Session Evaluation
To evaluate the practical effectiveness of the naval cyber range, a cyber awareness session was conducted with volunteer trainees at the Royal Military Academy. The scenario followed the provided timeline, covering mission briefings, navigation tasks, and staged cyber attacks.
A video summarizing this cybersecurity awareness session is available at the following address:
Demonstration Video of the Naval Cyber Range
Trainees operated dedicated virtual machines corresponding to different crew roles, while a cyber range manager supervised the simulation and injected threats. The mission involved navigating past hostile zones while performing routine tasks. Midway through the session, a phishing attack triggered a malware infection, leading to GPS spoofing and radar denial-of-service incidents. Trainees had to detect, investigate, and remediate the compromise while maintaining mission operations.
The session demonstrated the platform’s usability, realism, and pedagogical relevance. Participant feedback confirmed the immersive and instructive value of the scenario, supporting its future refinement and broader deployment.
Overall, the session was successful in delivering a realistic and engaging training experience. The maritime context, coupled with role-specific tasks and dynamic interaction with the scenario manager, maintained strong participant involvement throughout. The cyber attack sequence effectively tested the trainees’ reflexes under pressure, while the final remediation phase supported technical learning and teamwork.
Feedback from participants confirmed the scenario’s clarity and realism, though highlighted performance issues with virtual machines and the need for more focused guidance during forensic steps. These insights validate the naval cyber range as a promising tool for structured cyber awareness training, with clear paths for future improvement.
Exportability and Reusability
Exportability and reusability were key design drivers throughout the project. The naval cyber range can be redeployed in a matter of hours on new machines or cloud platforms using the publicly available configuration files and source code. This confirms the platform’s readiness for reuse in other training or research contexts. Future improvements, such as a dedicated installation guide, could further simplify adoption by external users and promote wider dissemination.
Evaluation Summary and Future Perspectives
The naval cyber range developed in this thesis demonstrates clear strengths as a modular, scalable, and flexible platform for both cyber awareness training and research in the maritime domain. Its architecture, based on open-source tools and containerized systems, allows for easy extension, reproducibility, and reuse across varied deployment contexts. The successful execution of a training session with volunteer trainees confirmed the practical relevance of the platform, highlighting its capacity to support immersive, mission-oriented scenarios and effective cyber attack simulations.
However, several limitations temper its current scope. The number of trainees that can be supported simultaneously remains low due to hardware constraints, and the manual nature of session management imposes significant demands on facilitators. Moreover, while the simulated network accurately reflects essential components of a Mine Countermeasure (MCM) vessel, several operational subsystems and cybersecurity mechanisms remain to be implemented.
Future improvements are both feasible and well-identified. These include enhancing system responsiveness through higher CPU allocation or cloud-based deployment, expanding the threat scenario library, automating session control and scoring, and integrating AI agents for real-time supervision or adaptive training. From a research standpoint, the cyber range offers promising opportunities for machine learning integration, anomaly detection experiments, and the generation of realistic maritime traffic datasets. Further system realism and complexity, such as the inclusion of encrypted communications, Intrusion Detection Systems (IDSs), or sonar, would elevate the platform’s utility for advanced cybersecurity evaluations.
In the long term, with incremental development and institutional collaboration, the platform could evolve into a full-scale maritime cyber range, bridging simulation and hardware components for training and research at operational levels.
Conclusion
This work presents the first operational naval cyber range, specifically designed to be used by Belgian Defence. By validating a functional proof of concept, the project demonstrates strong potential for both cyber awareness training and cybersecurity research in maritime environments. The modular and extensible design enables scalable development, supports a wide range of threat scenarios, and opens the door to future enhancements, such as automation, AI integration, and increased realism. Beyond its immediate technical contributions, this platform also lays the groundwork for future collaborations aimed at advancing maritime cyber defence capabilities. Finally, this thesis does not mark the end of a project, but rather the beginning of a broader ecosystem of possible developments, research initiatives, and operational applications in the field of naval cybersecurity.
References
[1] G. Longo et al., MaCySTe: A virtual testbed for maritime cybersecurity, SoftwareX, vol. 23, p. 101426, Jul. 2023.
[2] Belgium Naval & Robotics and Naval Group, MCM BE-NL Program: Whole Warship & Container Digital Domain SSRS CDRL DC.3, Version B, Apr. 8, 2024.
[3] Belgium Naval & Robotics and Naval Group, MCM BE-NL Program: Platform & Navigation Domain SSRS CDRL DC.3, Version B, Apr. 8, 2024.
[4] Belgium Naval & Robotics and Naval Group, MCM BE-NL Program: Combat Domain SSRS CDRL DC.3, Version B, Apr. 8, 2024.
[5] Belgium Naval & Robotics and Naval Group, MCM-BENL Program: System/Subsystem Design Description MCMPF, Version F, Apr. 30, 2024.
[6] Belgium Naval & Robotics and Naval Group, SSDD CS: Combat System System/Subsystem Design Description, Version H, Apr. 30, 2024.
This blog post is licensed under
CC BY-SA 4.0



- Introduction
- Problem Statement and Objectives
- Research Gaps and Opportunities
- Simplification of the MCM Warship Network Architecture
- Simplification Strategy and Implemented Systems
- Simulated Ship Systems and Protocols
- Platform Selection and Simulation Requirements
- Implementation of the Naval Cyber Range
- Exportability, Modularity, and Extensibility of the Project
- Overview of the Graphical Interfaces
- Overview of the Cyber Awareness Scenario
- Evaluation
- Evaluation Summary and Future Perspectives
- Conclusion
- References