Information gathering with BlackWidow
Jan 10, 2020 by Thibault Debatty | 3200 views
https://cylab.be/blog/56/information-gathering-with-blackwidow
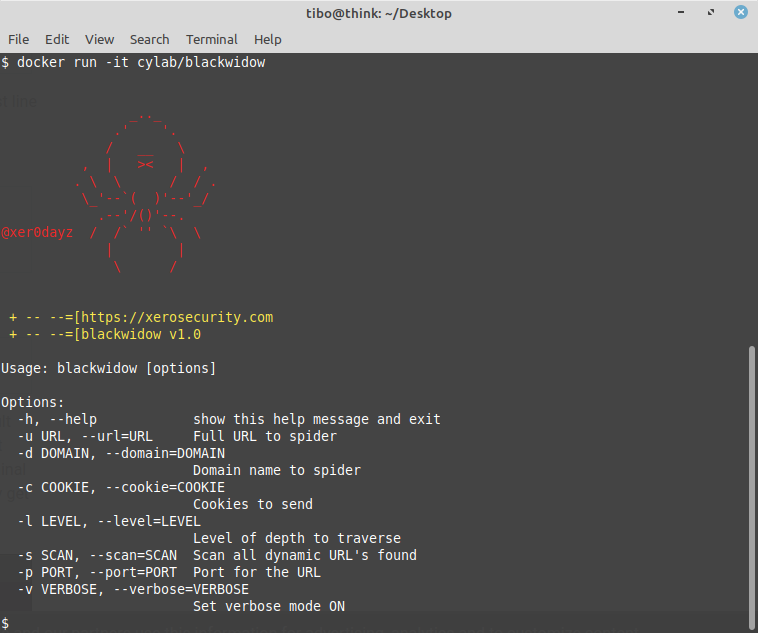
BlackWidow is a python script that automatically crawls a website to gather information like phone numbers, email addresses, form URL’s etc. Very useful during the reconnaissance phase!
The easiest way to use it is using the available docker image:
docker pull cylab/blackwidow:latest
docker run cylab/blackwidow
By default the docker image simply shows the help menu:
You can spider a full domain using
docker run cylab/blackwidow -u https://example.com
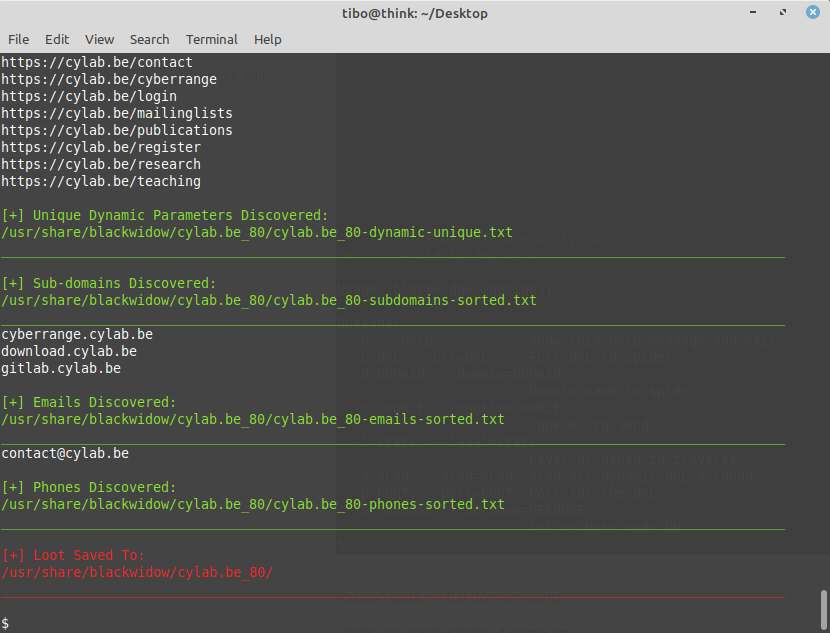
BlackWidow will display quite a lot of debug information, and at the end (or when you hit ctrl + c) it will display the report containing the found URL’s, email addresses etc.
If you add the option -s y, BlackWidow will also test all dynamic pages against some OWASP vulnerabilities like XSS, SQL injection, directory traversal, local file inclusion etc…
This blog post is licensed under
CC BY-SA 4.0