OWASP Dependency Check for Java
Jun 16, 2020 by Thibault Debatty | 5526 views
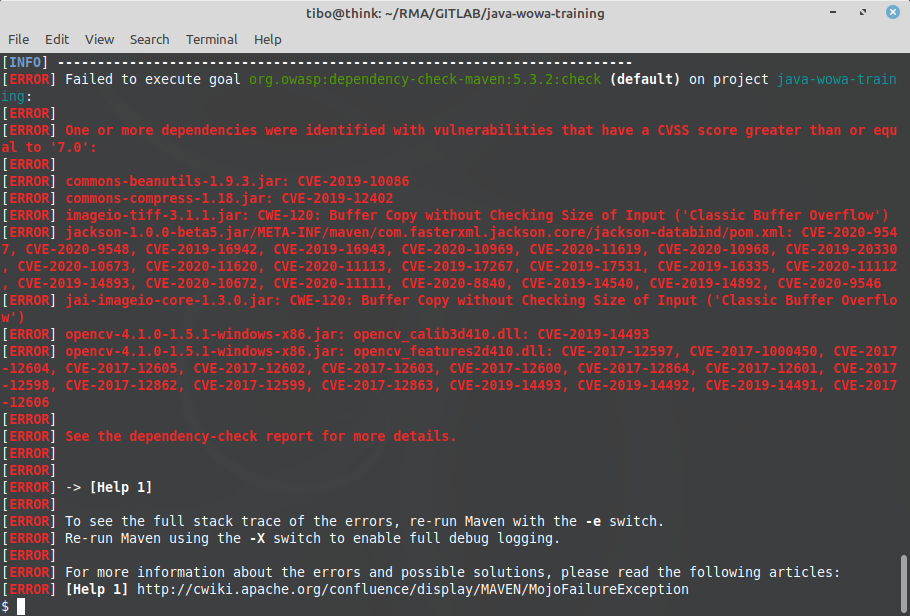
Besides avoiding bug and vulnerabilities in your own code base, creating a secure app requires you make sure that your app doesn’t rely on a library that contains vulnerabilities. In any modern project, you will have hundreds of them! Here comes OWASP dependency check to the rescue!
This tool will recursively check all dependencies of your project and compare them to the NVD (National Vulnerabilities Database) maintained by NIST.
To use OWASP dependency check, simply add the following snippet to your pom.xml:
<!-- dependency check -->
<plugin>
<groupId>org.owasp</groupId>
<artifactId>dependency-check-maven</artifactId>
<version>5.3.2</version>
<configuration>
<failBuildOnCVSS>7</failBuildOnCVSS>
</configuration>
<executions>
<execution>
<goals>
<goal>check</goal>
</goals>
</execution>
</executions>
</plugin>
With this configuration:
- maven dependency plugin will automatically be executed during the verify phase of maven (so after unit and integration tests);
- your build will fail if a dependency has a CVSS score of 7 or more.
You can also manually run the dependency check with:
mvn dependency-check:check
At the first execution, maven dependency check will download the CVSS database (roughly 100MB). This may take some time… The database will saved in ~/.m2/repository/org/owasp/dependency-check-data/. Hence, for the following executions, only available updates will be downloaded.
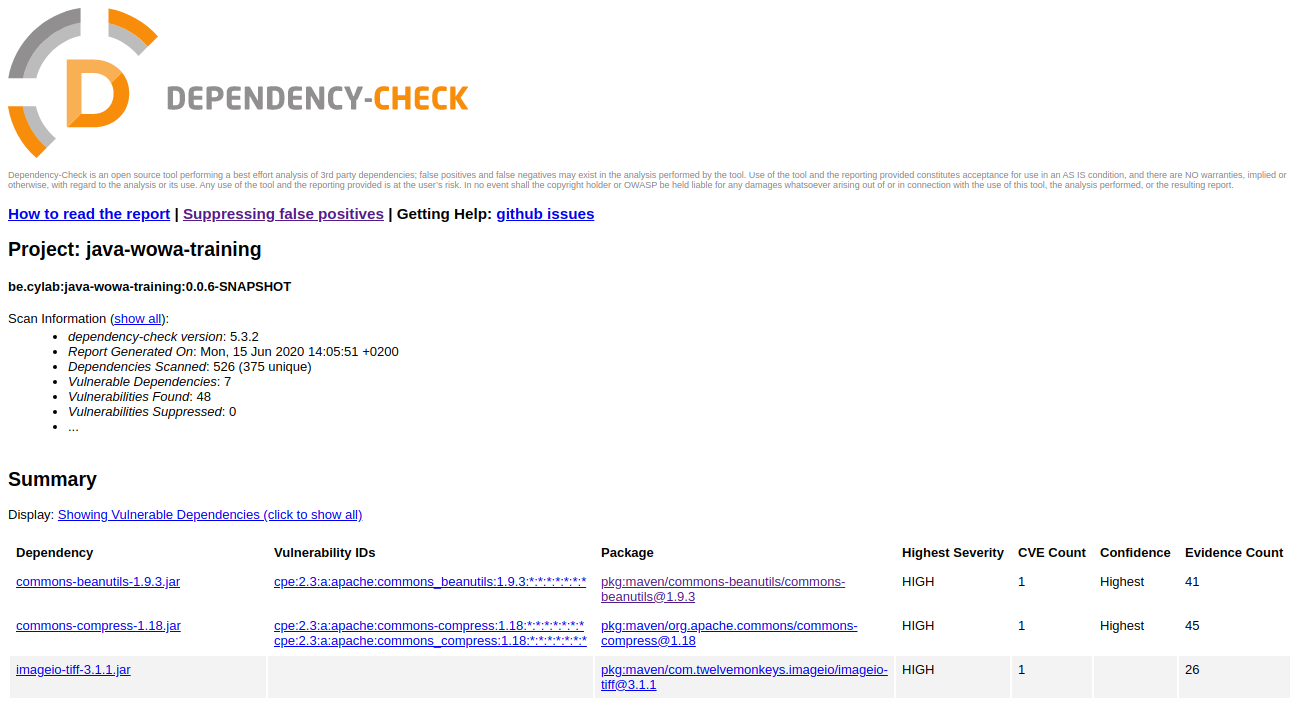
After execution, the full report will be located in target/dependency-check-report.html
Dealing with indirect dependencies
If the security notification concerns a direct dependency, it should be quite easy to fix it. Simply update your dependency in your pom.xml.
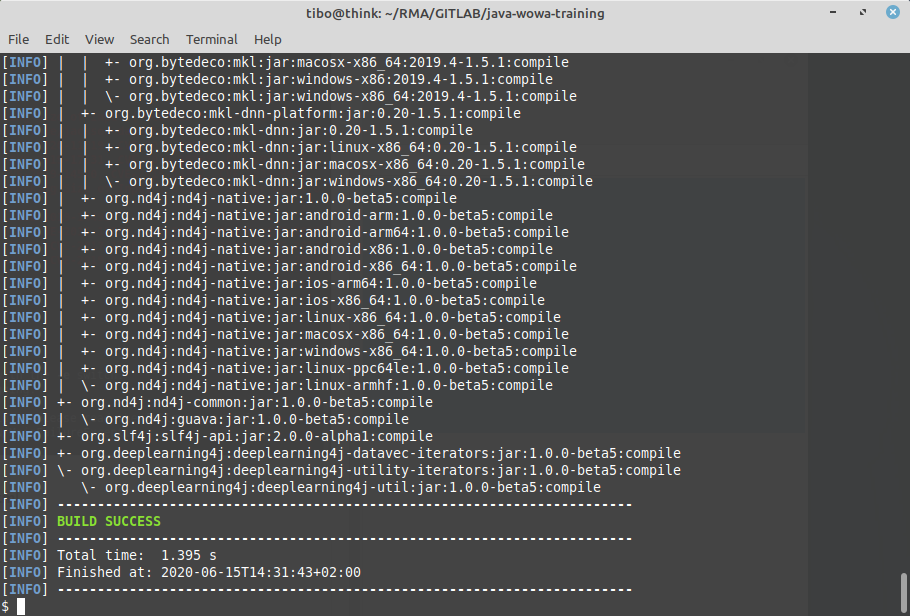
If the problem concerns an indirect dependency, you can use maven dependency tree to find which of your direct dependencies is causing the issue and should be updated:
mvn dependency:tree
Finally, if there is no update available for your direct dependency, you can still force a more recent version of the indirect library by adding a dependencyManagement section to your pom.xml:
<dependencyManagement>
<dependencies>
<!-- Manually upgrade commons-beanutils to fix vulnerability
CVE-2019-10086. Currently, the vulnerable version is only used
by com.opencsv:opencsv. When the common-beanutils are
upgraded in this dependency, we can remove this workaround. -->
<dependency>
<groupId>commons-beanutils</groupId>
<artifactId>commons-beanutils</artifactId>
<version>1.9.4</version>
</dependency>
</dependencies>
</dependencyManagement>
This blog post is licensed under
CC BY-SA 4.0