Password guessing with Hydra
Oct 21, 2020 by Alexandre Croix | 16365 views
A password is like a “key” used to open a specific door or vault. In this vault, there can be different personal documents, pictures, banking information… It is obvious that a user wants its personal documents secure. If the “key”, therefore the password, is easy to find, the vault can be as strong as you want, it will be easy to open it.
Password attacks
It is really important to make a strong password to reduce the risk your account will be hacked.

A hacker can perform two kinds of password attack: a password cracking attack and a password guessing attack.
Password cracking
Password cracking is a brute-force attack. By some means, the hacker has obtained the hash code of a user’s password. On his own computer, he is able to try all possibilities and find the password that generates this code.
This kind of attack can be improved by using a dictionary to perform the attack or by using some information about the victim (dog’s name, address, etc.). If the hacker has enough time, he will be able to recover the correct password and use it to log in in the future. Hashcat is a well-known tool for hashcode recovering. This tool is designed to be used on CPU,s GPUs and in multi-threads.
Password guessing
In this method, the hacker performs some guesses to log in with the victim account on a platform, website, etc. For example, the hacker can try to connect to Gmail if he knows the email address of the victim. This method has the advantage that it does not require a password hash code, but a lot of websites, systems have implemented some defensive mechanisms. After several wrong attempts, the account will be locked for a specific time and the user can be alerted for these attempts.
Because of these protections, a password guessing attack is slow. It is necessary to wait between attempts to avoid a lockout.
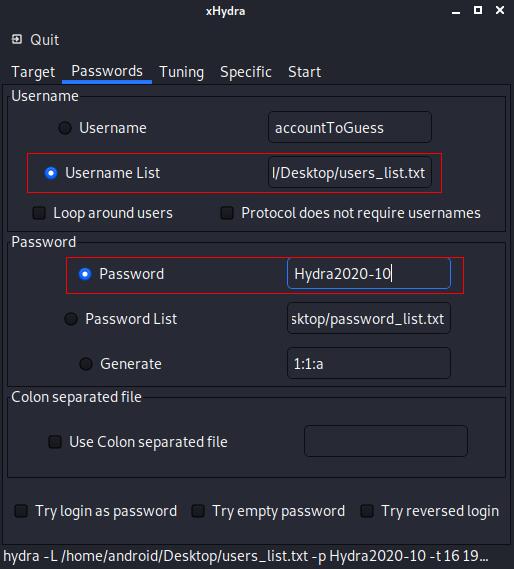
A Password Spray Attack is a password guessing attack where the hacker uses a single password with a list of users. Usually, this attack type is very efficient in a company network for example.
Hydra
Hydra is a very good tool for password guessing attacks. Hydra can be used in command line or with the (very good) Gui version: xHydra. Hydra is compatible with a lot of protocols (ssh, http-post, SMB, socks5, etc.).
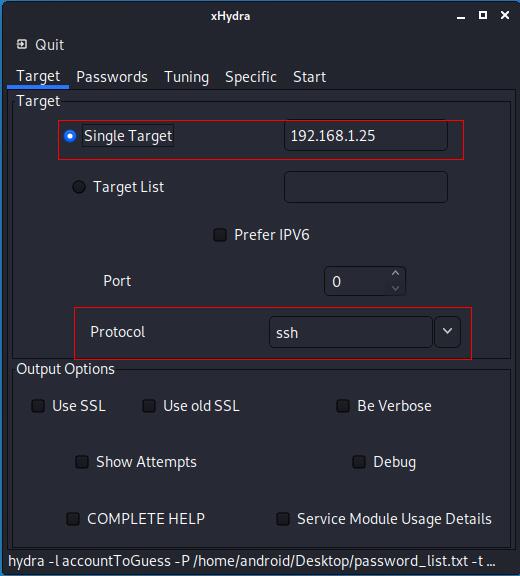
On the first tab, we can select the target IP address and the protocol used for the attack. Here we used a single target and the ssh protocol, but it is possible to use a list with several IP addresses.
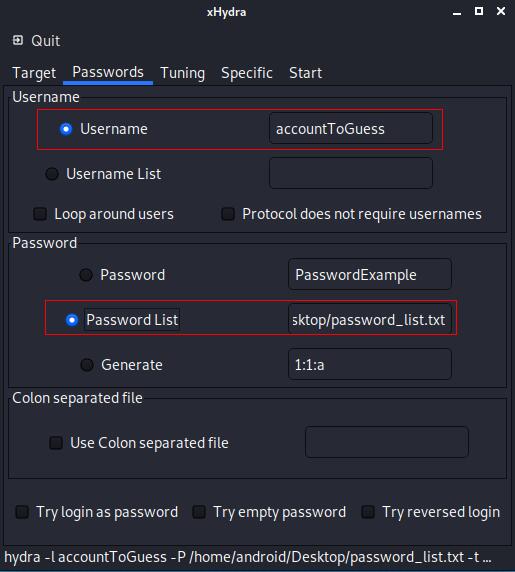
This second screenshot shows the settings for a classic password guessing attack. The first rectangle is the account name in which the hacker will try to connect in. The second one is the filename with the list of possible passwords. Of course, it is possible to use some social engineering to create this list.
In many organisations, the password must be changed every 90 or 120 days. Good guessing is to use the Year or the Season in the password. For example: Hydra2020-10 or WinterHydra2020.
This third screenshot shows the settings for a Passwords Spray Attack. We use a list of username and a single password.
The two last tabs are specific settings like proxy settings, debug print, etc. To run the attack, there is a Start button on the Start tab.
We can also see, at the bottom of the window, the command to perform this attack with the command-line tool.
Conclusions
Currently, big companies like Google, Facebook, Microsoft, etc. implement defensive mechanisms against password guessing. On your potential personal systems (server, website), it is important to set up security.
In all cases, the use of strong passwords is very important. The most important, is to NOT use the same password for several platform. A different password for all your account is the best solution.
A password manager can help you to improve the security of your different accounts. Dashlane, Keepass, Bitwarden or LastPass are good password managers you can use.
This blog post is licensed under
CC BY-SA 4.0