Fail a phpunit test if coverage goes below a threshold
Dec 30, 2020 by Thibault Debatty | 6498 views
https://cylab.be/blog/114/fail-a-phpunit-test-if-coverage-goes-below-a-threshold
Tools like maven allow to fail a build pipeline if the coverage of unit tests goes below a given threshold. For phpunit and PHP project, there is no such option. So here is a trick to fail your pipeline if the coverage of your phpunit tests goes below a threshold.
The trick consists of 2 steps:
- run phpunit with the option
--coverage-xmlto create an xml coverage report; - use a custom script (we will call it
phpunit-thresholdto parse the xml report and fail if the coverage goes below a provided threshold.
phpunit
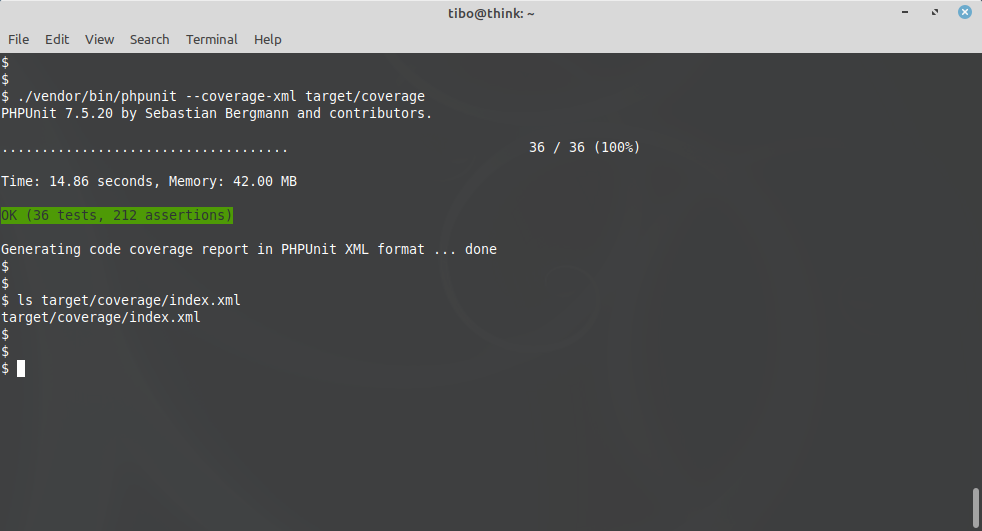
For the first step, you have to run phpunit with the option --coverage-xml:
./vendor/bin/phpunit --coverage-xml target/coverage
This will create a directory called target/coverage, with a bunch of xml report files, including one file called index.xml
phpunit-threshold
We can now create a script called phpunit-threshold.php that will parse this xml report:
<?php
/**
* phpunit-threshold.php
* check if the coverage of phpunit is above specified threshold
* https://cylab.be/blog/114/fail-a-phpunit-test-if-coverage-goes-below-a-threshold
*/
if ($argc != 3) {
echo "Usage: " . $argv[0] . " <path/to/index.xml> <threshold>
";
exit(-1);
}
$file = $argv[1];
$threshold = (double) $argv[2];
$coverage = simplexml_load_file($file);
$ratio = (double) $coverage->project->directory->totals->lines["percent"];
echo "Line coverage: $ratio%
";
echo "Threshold: $threshold%
";
if ($ratio < $threshold) {
echo "FAILED!
";
exit(-1);
}
echo "SUCCESS!
";
To use this script, we must indicate that path to index.xml as the first argument, and the desired coverage (in percent) as the second argument:
php phpunit-threshold.php target/coverage/index.xml 90
GitLab
Now you can add this test to your .gitlab-ci.yml:
test:
image: cylab/php:7.2
before_script:
# Install all project dependencies
- COMPOSER_CACHE_DIR=composer-cache composer install
script:
- vendor/bin/phpunit --coverage-text --coverage-xml target/coverage-xml
- php phpunit-threshold.php target/coverage-xml/index.xml 80
This blog post is licensed under
CC BY-SA 4.0