CyberChef, the Cyber Swiss Army Knife
Mar 10, 2022 by Georgi Nikolov | 3306 views
https://cylab.be/blog/206/cyberchef-the-cyber-swiss-army-knife
Don't remember all the command line tools or which parameters go where? At some point getting lost in all these terminal screens running different algorithms one after the other? Let CyberChef prepare and cook all this for you!
The main focus of our team is research into new ways we can detect and defend from emergent cyber threats, but without educating people about the dangers, it becomes hard to protect our data and private information. Our education efforts vary between giving general IT classes to the students at the Royal Military Academy and more specialized classes to private groups. In the past, we have given Awareness Training courses to the European Space Agency (ESA) and since the beginning of the year, we are busy organizing crash courses for students interested in participating in the Cyber Security Challenge. During these courses we go over some of the cyber security theory and show them practical tools, one of which is the magnificently named "CyberChef".
What is CyberChef?
During research or incident response, it is not always possible to do everything we want, usually because of time constraints. It is quite fortunate that there are tools out there, which can help us speed some some operations and present us the findings in a timely fashion. CyberChef is one such tool, as described by the creators themselves:
CyberChef is a simple, intuitive web app for carrying out all manner of "cyber" operations within a web browser. These operations include simple encoding like XOR or Base64, more complex encryption like AES, DES and Blowfish, creating binary and hexdumps, compression and decompression of data, calculating hashes and checksums, IPv6 and X.509 parsing, changing character encodings, and much more. The tool is designed to enable both technical and non-technical analysts to manipulate data in complex ways without having to deal with complex tools or algorithms. It was conceived, designed, built and incrementally improved by an analyst in their 10% innovation time over several years.
The live demo of the tool can be accessed via their CyberChef web-portal, but it is also possible to download the CyberChef code from Gitlab or download the Docker container to run the project locally.
Using CyberChef
The tool in itself is quite intuitive. There are multiple panels, which serve clearly defined purpose, as shown below.
- The right-most Operations panel shows a list of all the commands and algorithms one might want to use during an analysis. There is a handy "Search bar" to look-up something specific.
- The Recipe panel will display all the commands that we have selected in their corresponding order and once we are complete, we can click on "BAKE!" to execute them, or check the "Auto Bake" dialog box to execute them automatically.
- The Input panel is where we put the input data we would like to analyze. We can drag & drop it or use the import function to select a folder or file from our machine.
- The Output panel will show the generated output when the commands we have selected are run over the input data.
At any point we can save the sequence of commands, or recipe, and the output generated by them. This is handy if we want to share them with other people or save them for later use. It is also possible to delete the contents of the panels and reset to default so we can analyze something else.
Demonstration
During our Cyber Security Challenge courses, we often use examples of challenges presented during previous years. One such challenge, that we used, is the Alien Object Challenge. The students are presented with a JPG file and they need to investigate it and find a specific string of characters, representing a "flag".
The steps in analyzing the image file are as follows:
- Open the file and see if something can be detected from the image itself
- Look at the metadata of the file
- Extract any strange or suspicious data from the metadata
- Transform the suspicious data into something comprehensible
- Analyze the suspicious data to discover what it represents
- Find and extract the flag
Of course we can do all these steps using a variety of tools through the command line, but to speed up the process, we can use CyberChef and facilitate the analysis quite a bit.
Analyzing the Metadata
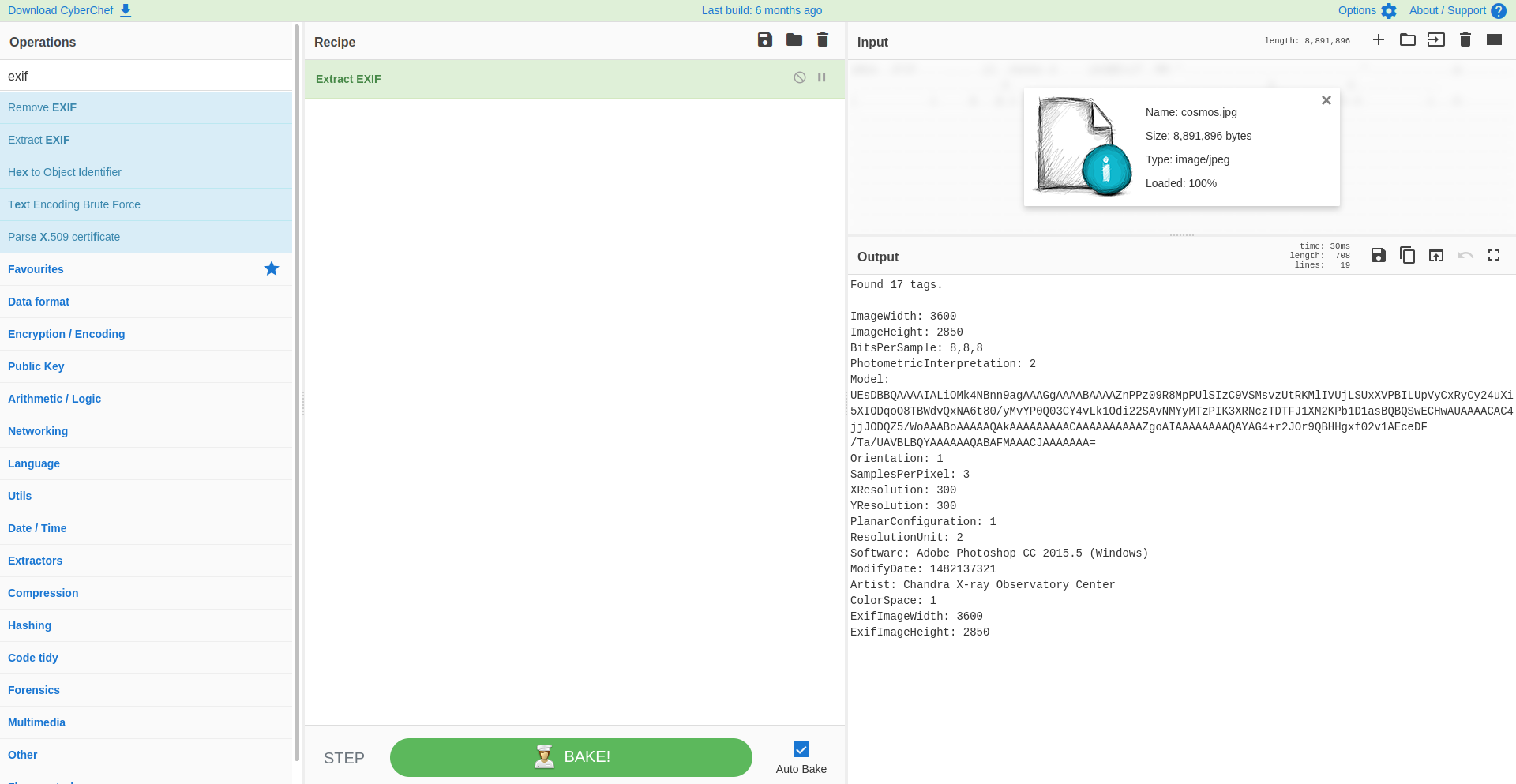
First we drag and drop our cosmos.jpg image in the Input panel. Then we need to use the correct operation to check the metadata, in this case we will search for the "Extract EXIF" command.
We can see already in the Output panel the metadata, which is presented to us in a clear and readable way. Something that seems off, is the field "Model", it contains a long string of characters, which is not normal.
Extracting the suspicious data
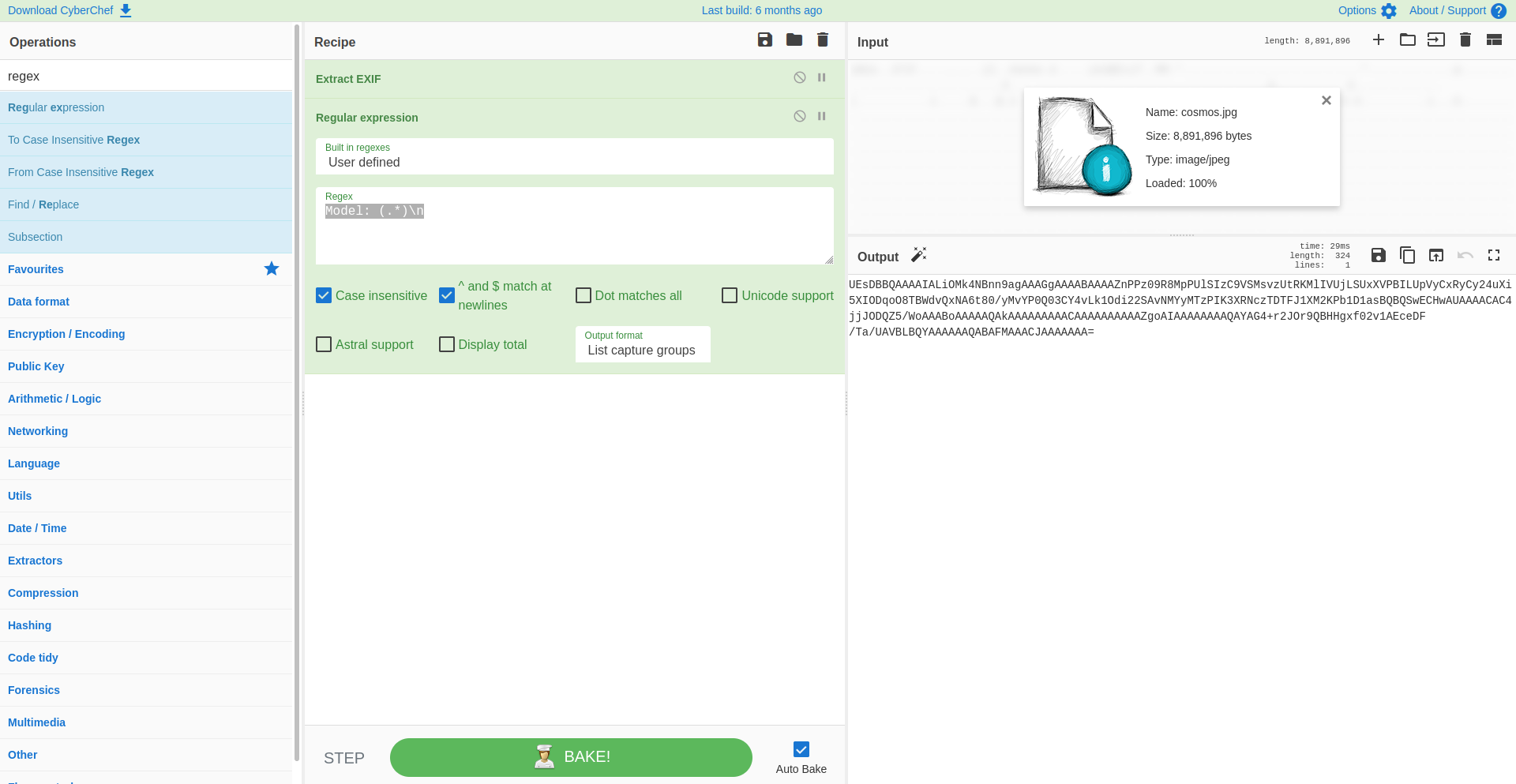
To extract the data, we can use a regular expression, or regex for short. We can search for the "Regular expression" operations in the Operations panel and drag & drop it in our Recipe panel. There we are presented with some options to fill in:
- Select a build in regex : in this case we will opt for one we will define
- Regex : here we will extract the data from the "Model" field using the following regex:
Model: (.*) - Extra options : we will set the operation to be case sensitive and match new lines.
- Output format : we just need the value of the "Model" field so we will select "List capture groups"
Now in the Output panel we only see the long string of characters.
Transform the suspicious data into something comprehensible
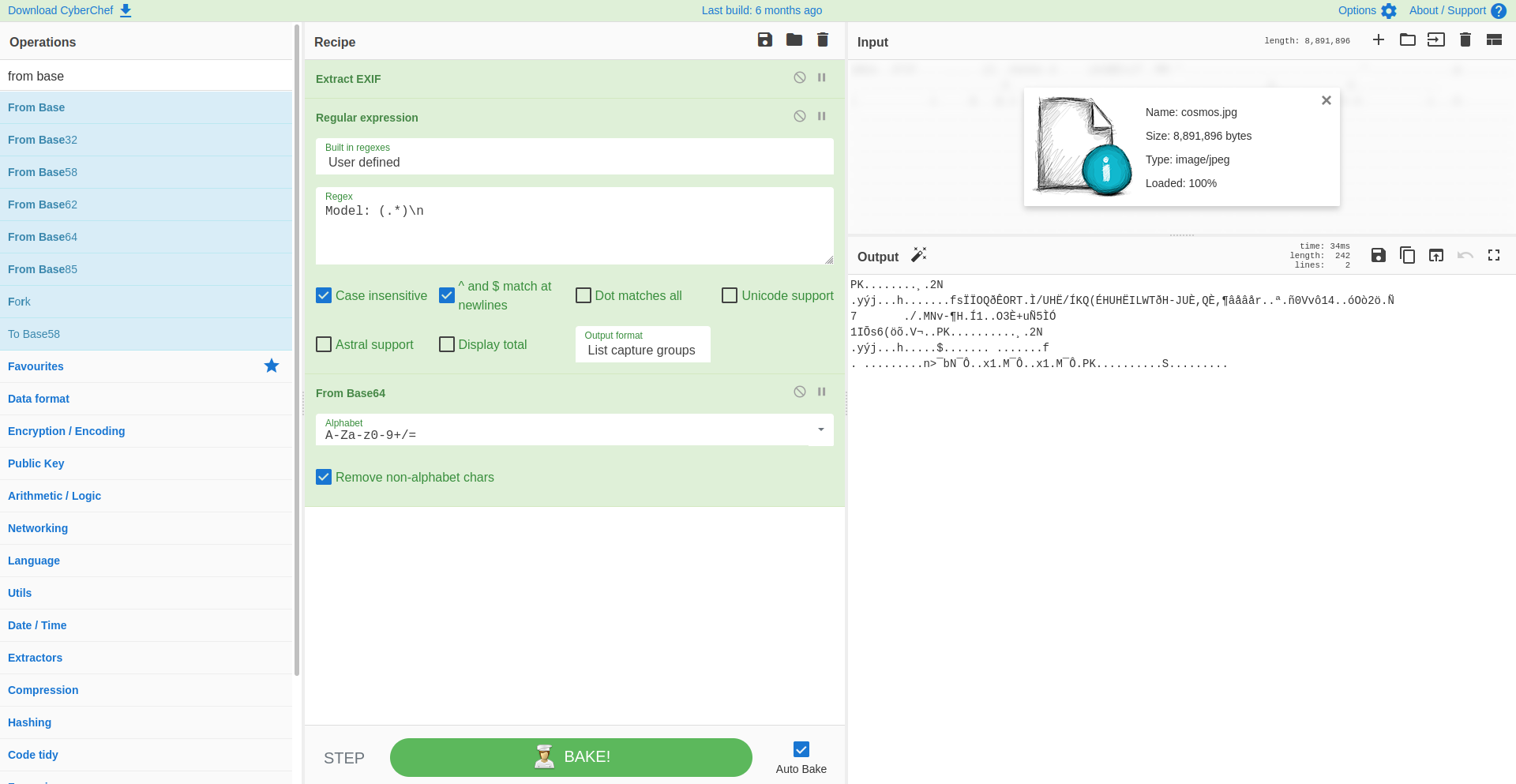
For those with some IT knowledge, we can see that the string of characters ends with a = symbol. This usually means that this is a string encoded in base64. To decode it, we can search for the "From Base64" operations and drag it into our Recipe panel. Directly the string from the previous step is transformed into something new.
Sadly the output hasn't become any more readable, but it does give us extra information about what we are looking at. The starting two characters PK signify that this is a zip file, following the list of signatures found on the Wikipedia source list. The interesting thing is that if we hover over the magic wand on the top right of the Output panel, it will show us that we can unzip this data and what the contents would be.
Extract the flag
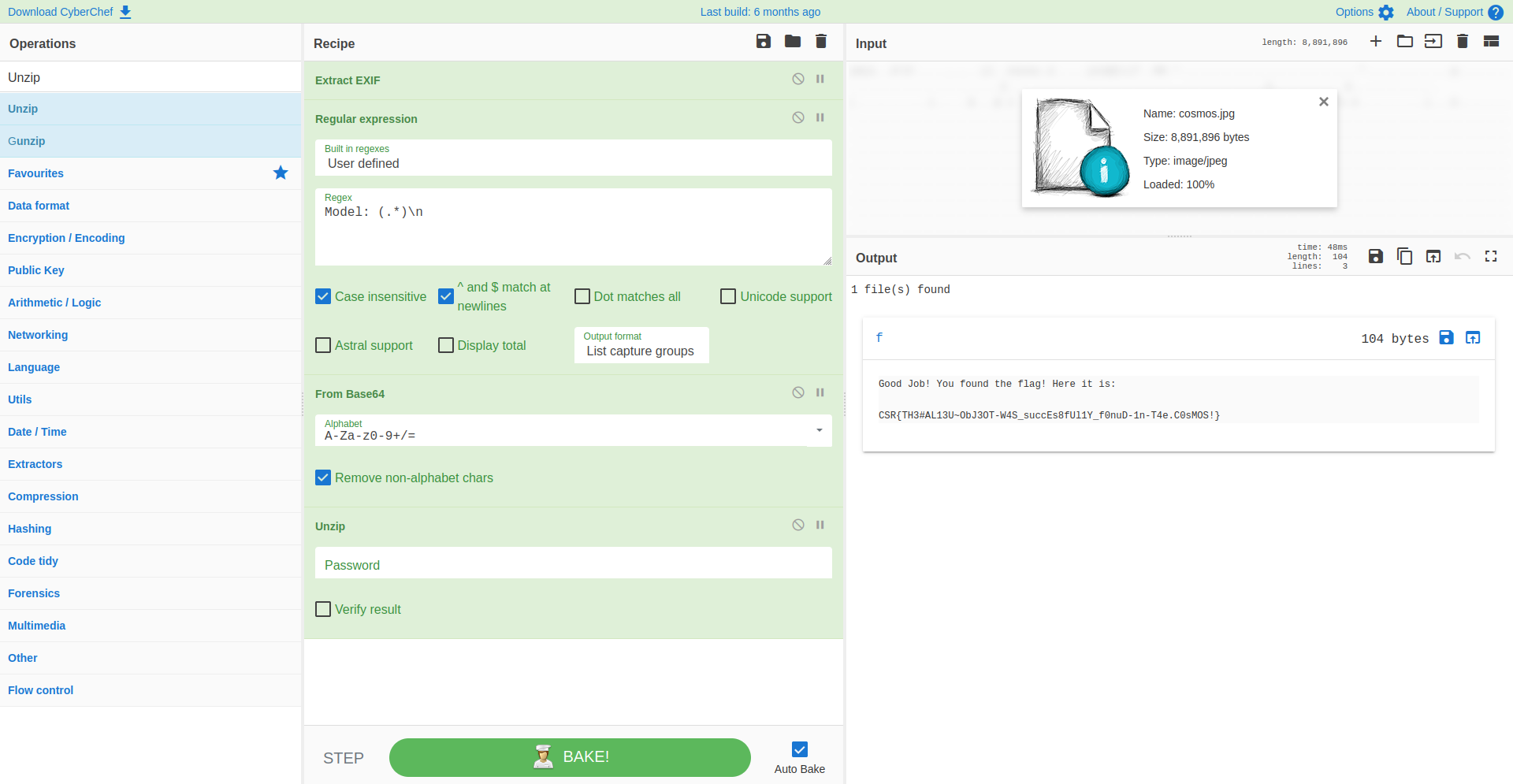
So now we can search for the "Unzip" operation and drag it into our Recipe. Directly we can see that the data in the Output panel has changed to a link named f. When clicking on it, we are presented with the contents of the zip and our flag!
Conclusion
As a researcher or cyber analyst it is often important to know how to use different tools and commands through the command line, but it is not always feasible to spend long amounts of time to test every possible solution, or even remember the right sequence of parameters! This is why it is great to be able to refer to tools, such as CyberChef, to do the heavy lifting for us. In the same vein, students can familiarize themselves with certain techniques and concepts they might encounter often, when dealing with cyber defense and data analysis.
This blog post is licensed under
CC BY-SA 4.0