Install and use different versions of PHP
Dec 18, 2022 by Thibault Debatty | 2361 views
https://cylab.be/blog/249/install-and-use-different-versions-of-php
When working on different projects, you may have to switch between different versions of PHP. In this blog post we show how to install and use different versions PHP on Ubuntu.
Install different versions of PHP
To install different versions of PHP we will install the ondrej/php PPA repository:
sudo apt install software-properties-common
sudo add-apt-repository ppa:ondrej/php
sudo apt update
Now we can install the desired version(s) of PHP. For example:
sudo apt install php7.4-cli php8.1-cli
At the time of writing, you can choose from
php5.6php7.0php7.1php7.2php7.3php7.4php8.0php8.1php8.2
You can also check available versions by yourself with
sudo apt search php.*-cli
Switch between and use different versions of PHP
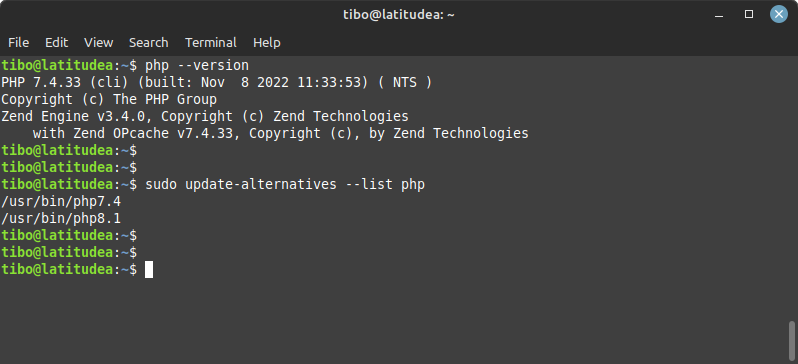
So now you should have different versions of PHP installed. To know which version is currently in use, you can simply type
php --version
To switch to another version, you can use update-alternatives. First you can list the installed versions with
sudo update-alternatives --list php
Now you can change to another version with update-alternatives --set. For example:
sudo update-alternatives --set php /usr/bin/php8.1
This blog post is licensed under
CC BY-SA 4.0