Mitre Att&ck in Practice - Part I : Navigator & Atomic Red Team
Jul 14, 2022 by Paloma de la Vallée | 8641 views
Tools Offensive Security Red Teaming
https://cylab.be/blog/224/mitre-attck-in-practice-part-i-navigator-atomic-red-team
One of our previous blog post presented the Mitre Att&ck Framework and the associated Mitre Att&ck Matrix. This post is the first of a set of three that will present how to link the Mitre Framework with open source tools to design and test offensive actions in practice.
The Mitre Att&ck Navigator
Next to the classical Matrix, the Mitre Corporation has developed an online tool offering various ways to use the Matrix, called the ‘Navigator’. It can be leveraged to deploy the usual use cases of the Matrix. An introductory video is available online that demonstrates the functionalities of the Navigator; we’ll only be looking at some very specific aspects here.
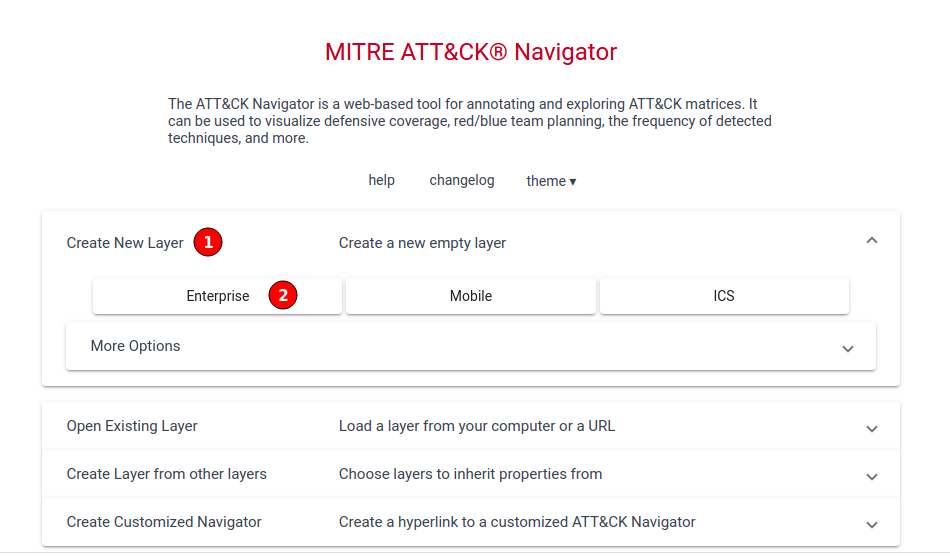
The Navigator is available here. To use the Navigator, let’s first create a new Layer and choose the Enterprise realm.
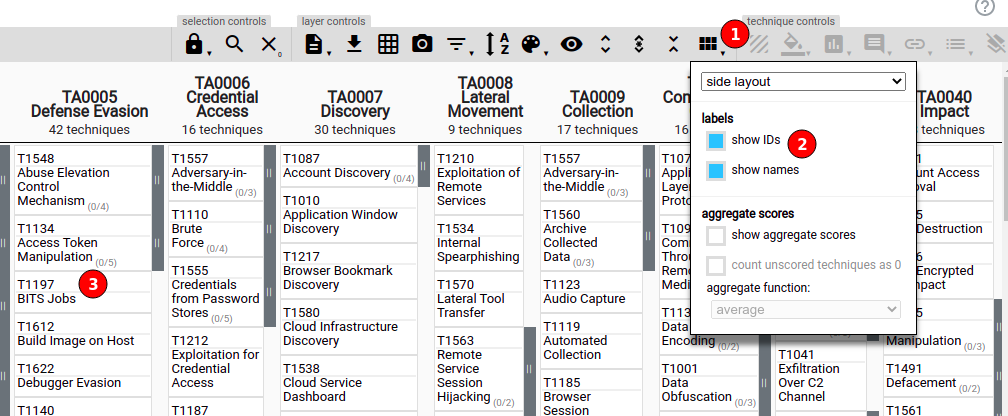
The interactive version of the Mitre Att&ck Matrix is then presented. All the Techniques are shown in individual cells gathered in columns corresponding to the Tactics. It is possible to display the Techniques IDs: it suffices to click the Matrix Configuration icon on the top left to drop down an options menu, and toggle the ‘show IDs’. The cells then include the Techniques codes of the type Txxxx. These IDs are often mentioned, possibly together with the names, to refer unequivocally to specific Techniques.
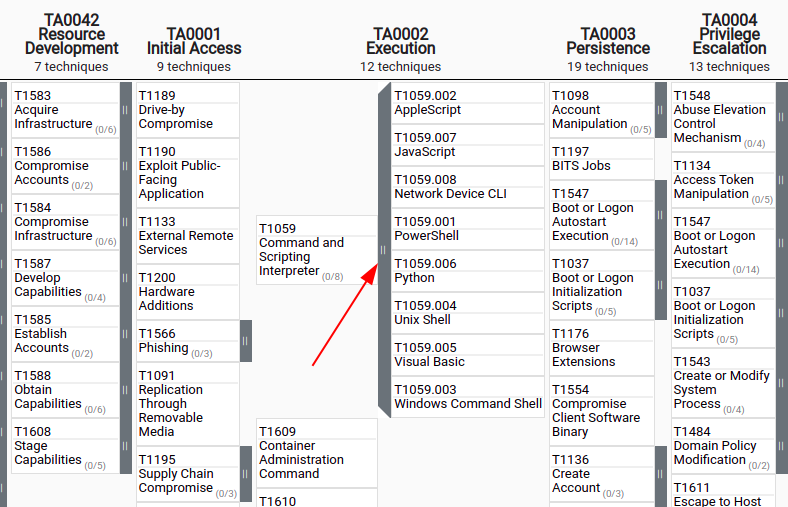
Where appropriate, some Techniques have been split in groups of sub-techniques, these are indicated on the Navigator by the grey zone. Clicking this grey zone expands (collapses) the group to display (hide) the individual sub-techniques. This greatly improves the readability of the Matrix.
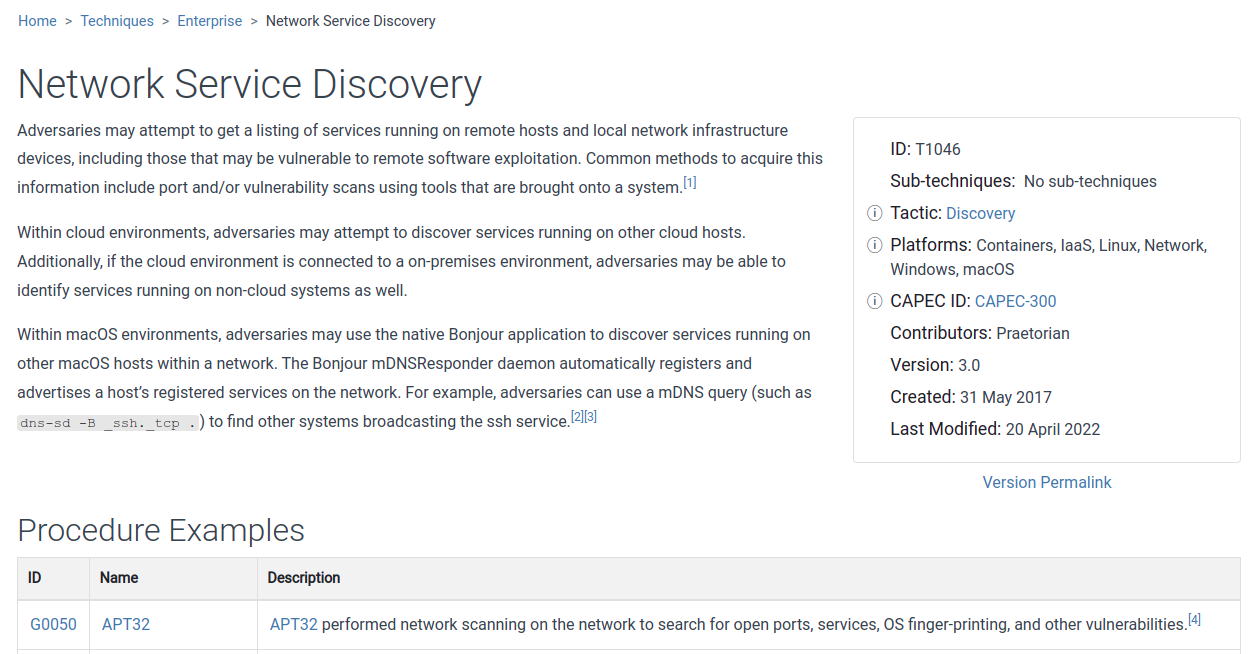
Right-clicking a Technique opens a menu with an option to View Technique: selecting this option opens the Mitre page of the Technique in question, with the full description and curated information that could be gathered through forensic analysis of real-world attacks.
Neat.
Atomic Red Team
However, while the Mitre page usually provides very useful and reliable intelligence, it does not describe how to deploy the Technique in question. Take for instance the Technique ‘T1046 Network Service Discovery’. The page of this technique offers precious few details on the best way to perform an actual network service discovery.
This is where the Atomic Red Team (ART) enters the scene. Atomic Red Team is a collection of code snippets that allow to actually execute a Technique, collection mapped on the Mitre Att&ck Framework. The repository is maintained by the team of Red Canary, and is organized with the idea to ease testing the sensitivity of IT systems to various Techniques.
The atomics are sorted by Technique IDs, and ready to be deployed. Each atomic consists of a series of tests that are described in detail in a yaml file for processing and a markdwon file for readability. For each test, the file describes the supported OS, and the commands for an appropriate executor.
For instance, in the case of the T1046 mentioned above, the atomic proposes 8 tests: the first test is a port scan that can be executed on Linux or MacOS, the proposed command should be executed by a shell.
While not all Techniques have an associated atomic, the ART proposes quite a lot of tests for the usual OSes.
Nice.
The automated way - Invoke-Atomic
The repository of ART can be simply cloned, and the commands executed manually to great success. However, the ART goes further and provides a tool called Invoke-Atomic that, after installation, automates the execution of the atomics. It is based on PowerShell, and can be deployed on Linux or MacOS after installation of PowerShell Core. After a bit of installation kung-fu, the ‘Invoke-AtomicTest’ module is available.
Different ways to use Invoke-Atomic are proposed on the github repository. The most usual commands are:
- List all the available tests:
Invoke-AtomicTest All -ShowDetailsBrief - List the tests of an atomic:
Invoke-AtomicTest <atomic code> -ShowDetailsBrief - Request the execution of an atomic:
Invoke-AtomicTest <atomic code> - Request the execution of specific tests:
Invoke-AtomicTest <atomic code> -TestNumbers n1,n2
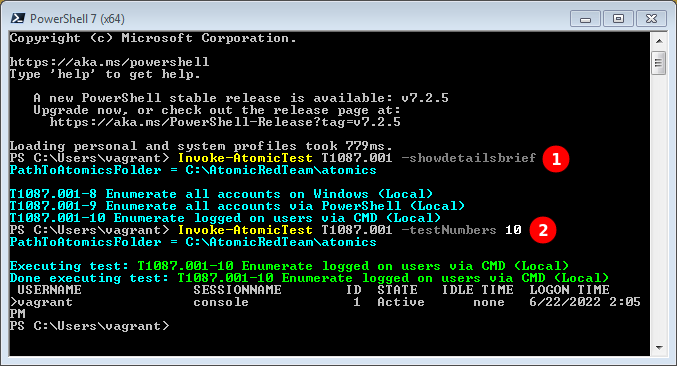
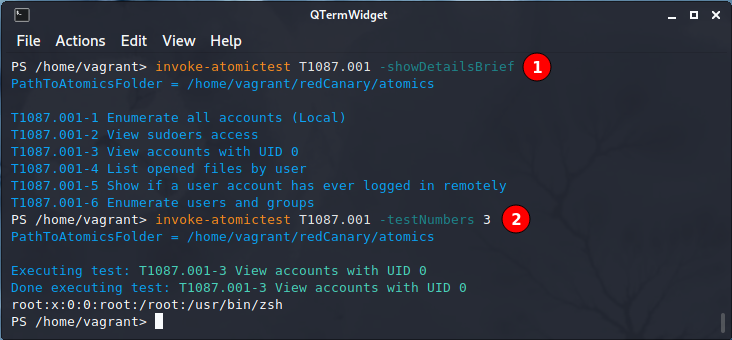
Only tests relevant for the running OS will be proposed. For instance, the atomic T1087.001 reveals different tests on Windows and Linux.
On Windows 7:
On Kali Linux 2021.3:
Those two examples show how the same atomic, or the same Technique, are automatically executed differently on Windows- or Linux-based OSes.
Great!
Conclusion
The combination of the Mitre Att&ck Navigator and the ART allows to explore the Framework from the offensive and defensive positions in many ways.
The Navigator reflects the Att&ck Matrix, and facilitates the exploration of the various steps of the Kill Chain. Thanks to the Techniques IDs, the link with the ART atomics is immediate, and the actual deployment of some offensive Techniques on IT system made easier.
The ART repository does not cover all the Techniques of the Mitre Att&ck Matrix, indeed it mainly lives off the land. However, it is still an interesting collection of tests that can be performed at a relatively low cost. And it can be seen as a repository of commands to execute specific Techniques in the context of a Red Teaming engagement.
This blog post is licensed under
CC BY-SA 4.0