VirusTotal, what is it and what is it good for?
Jan 13, 2023 by Georgi Nikolov | 7891 views
https://cylab.be/blog/253/virustotal-what-is-it-and-what-is-it-good-for
If you have ever been a bit paranoid about files you have received per mail, or you work in a sensitive environment, you have searched online for tools which can help you analyze a file and give you a detailed overview if it could be harmful or not. Virustotal is one of the more prominent online services, which offers a way to upload any suspicious files and analyze them.
How does it work?
VirusTotal offer different ways to submit files to the platform, be that via the web-interface, browser extensions or their very own API. The interesting thing here is that, through the use of the API, we can automate the submissions to VirusTotal and integrate the service in a SOC, when a suspicious or potentially malicious file is encountered.
VirusTotal uses a large variety of antivirus scanners and URL/domain blacklisting services. Alongside that, specialized tools which serve as sandbox environments are utilized to extract valuable information about the behavior of the file.
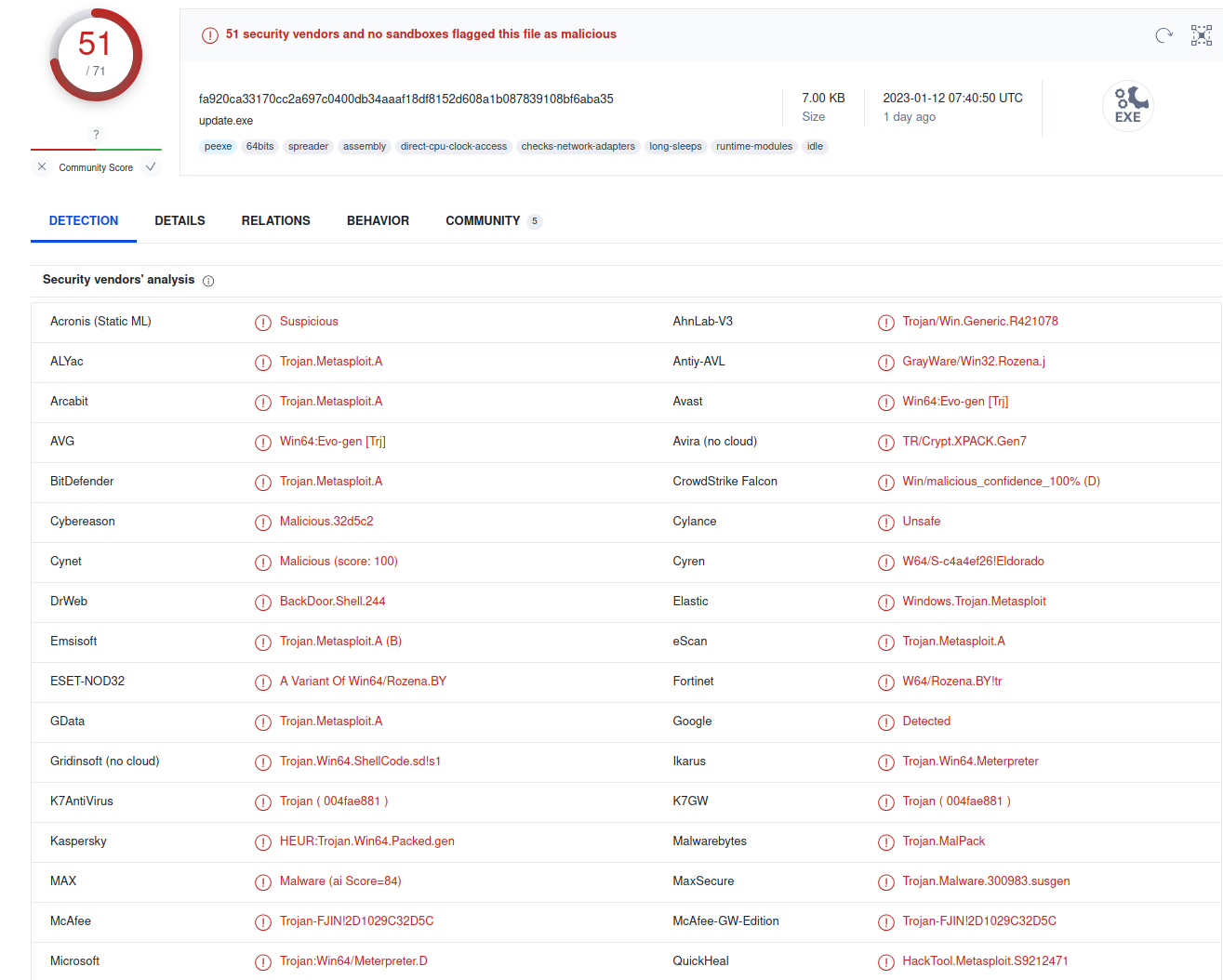
In the above screenshot we can see a sample executable, that I generated using msfvenom. The file was ran against 71 different antivirus detection programs and we can see 51 of them tagged it as malicious. To be clear, there is very little obfuscation present in the malicious executable, it was generated to be used as an example of what VirusTotal does. The goal of the file is to establish a connection between the machine it us run upon and another machine, running Metasploit. When that is done, a piece of code will be downloaded and a meterpreter connection between the two machines will be established.
If you are interested to read more about Metasploit, I wrote some time ago a short blog about setting up a simple waterhole attack using the platform, link her
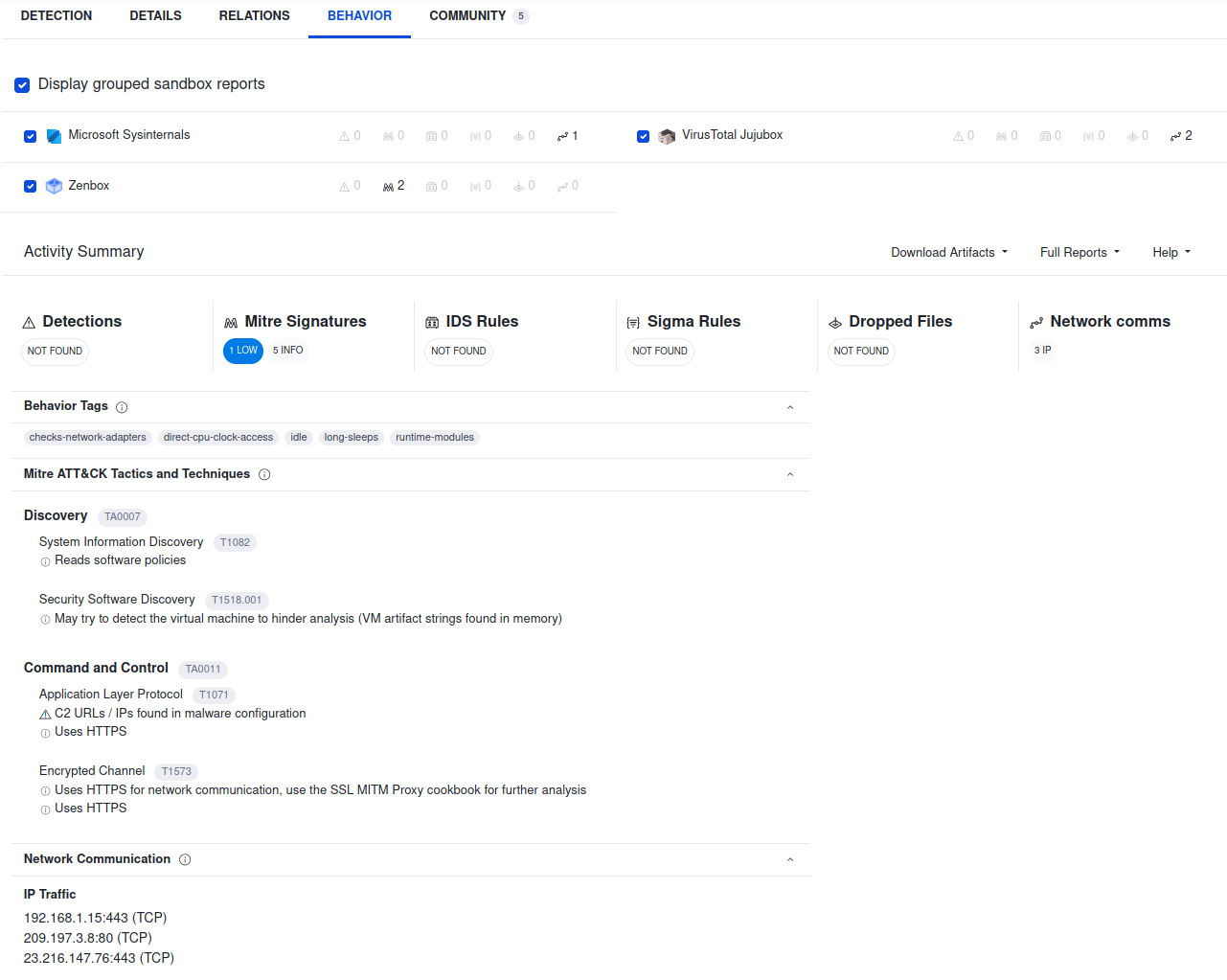
Alongside the antivirus detectors, VirusTotal will also analyze the uploaded item in a sandbox environment. Interestingly, the results of the sand-boxing are compared to online sources such as MITRE ATT&CK (which me and my colleague Paloma have written previously about here, here and here) and the Sigma Ruleset. This is quite interesting, as these freely-available repositories of APT indicators of compromise are quite well regarded and quite powerful when applied correctly.
Should we always upload suspicious files to VirusTotal?
The answer here is not that clear-cut. VirusTotal offers a quick and easy solution for analysis of suspicious files, but there is one thing which is often overlooked- its free accessibility to end-users means that malicious actors will also have access to the reports generated by the tool. In the case of new attacks, attackers might be observing if samples of their tools are uploaded to VirusTotal, signaling to them that they might have been discovered. This gives them vital information about the state of their operations and the current activity of the defenders. Furthermore, it is often ill-advised to automated submissions to VirusTotal and instead do a review based analysis of a suspicious file, before resorting to such online tools. There are similar analysis platforms that exist (such as Cuckoo Sandbox, about which we might talk more in a future blog) that offer the same detailed analysis without the drawback of possibly leaking information to the adversaries.
Conclusion
VirusTotal is very interesting, powerful and easy to use tool, which offers great benefits, but depending on your situation, must not always be the first option. Currently we are interested in learning more about complex obfuscation techniques used by adversaries and VirusTotal is an easy tool to use to test these techniques. If you are interested to work in this field, you can read more at our internship proposal.
This blog post is licensed under
CC BY-SA 4.0