Explore the SAM hive with Regedit (and Sysinternals)
Nov 21, 2023 by Thibault Debatty | 13705 views
https://cylab.be/blog/311/explore-the-sam-hive-with-regedit-and-sysinternals
The Windows Registry is a kind of database that stores a lot of important configuration parameters for Windows and installed applications. The specific of this database is that the data is actually stored in different files called hives. One of these is the SAM (Security Account Manager) hive, which stores, among others, user passwords. Let’s explore this hive a little..
The SAM hive is physically stored in %SystemRoot%/system32/config/SAM, but the easiest way to explore it is using Regedit. So run Regedit as Administrator:
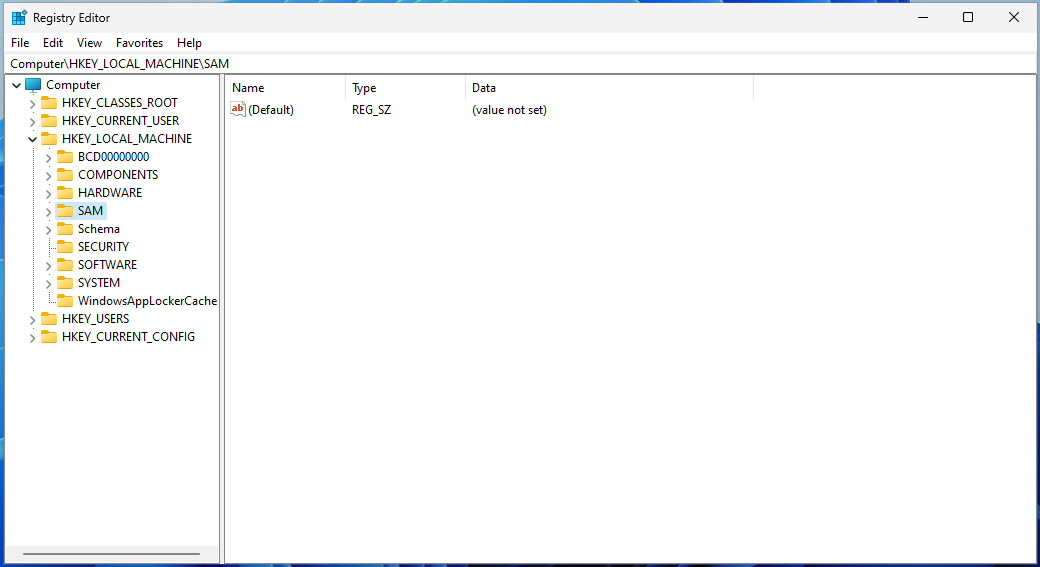
Then navigate to HKEY_LOCAL_MACHINE\SAM and you will see … nothing 🤔
The reason is that the Administrator account is actually not the most powerful account in Windows. And even the SAM hive, which contains user passwords, is not accessible for the Administrator. The real Windows superuser (the equivalent of root) is the SYSTEM user account.
Trick is, Windows has no menu option to Run as SYSTEM, so you will have to
-
Install Sysinternals to do this. You can find a tutorial in another blog post: https://cylab.be/blog/310/install-sysinternals
-
Open a command prompt as Administrator
-
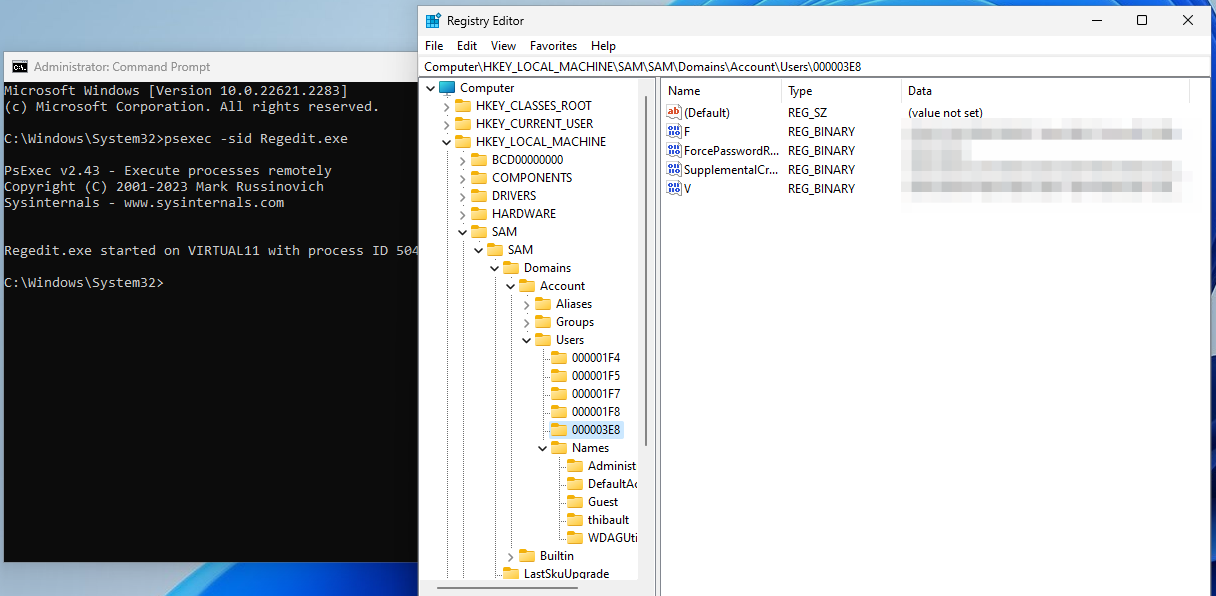
In the command prompt, use psexec (from Sysinternals) to run regedit with elevated privileges:
psexec -sid Regedit.exe
- This time, you will be able to browser the SAM hive, including the (hashed) local account passwords.
This blog post is licensed under
CC BY-SA 4.0