Elaborated new phishing method targeting Belgian people -- Part 1
Dec 10, 2024 by Cylab Researcher | 1805 views
https://cylab.be/blog/382/elaborated-new-phishing-method-targeting-belgian-people-part-1
A chilling Saturday afternoon
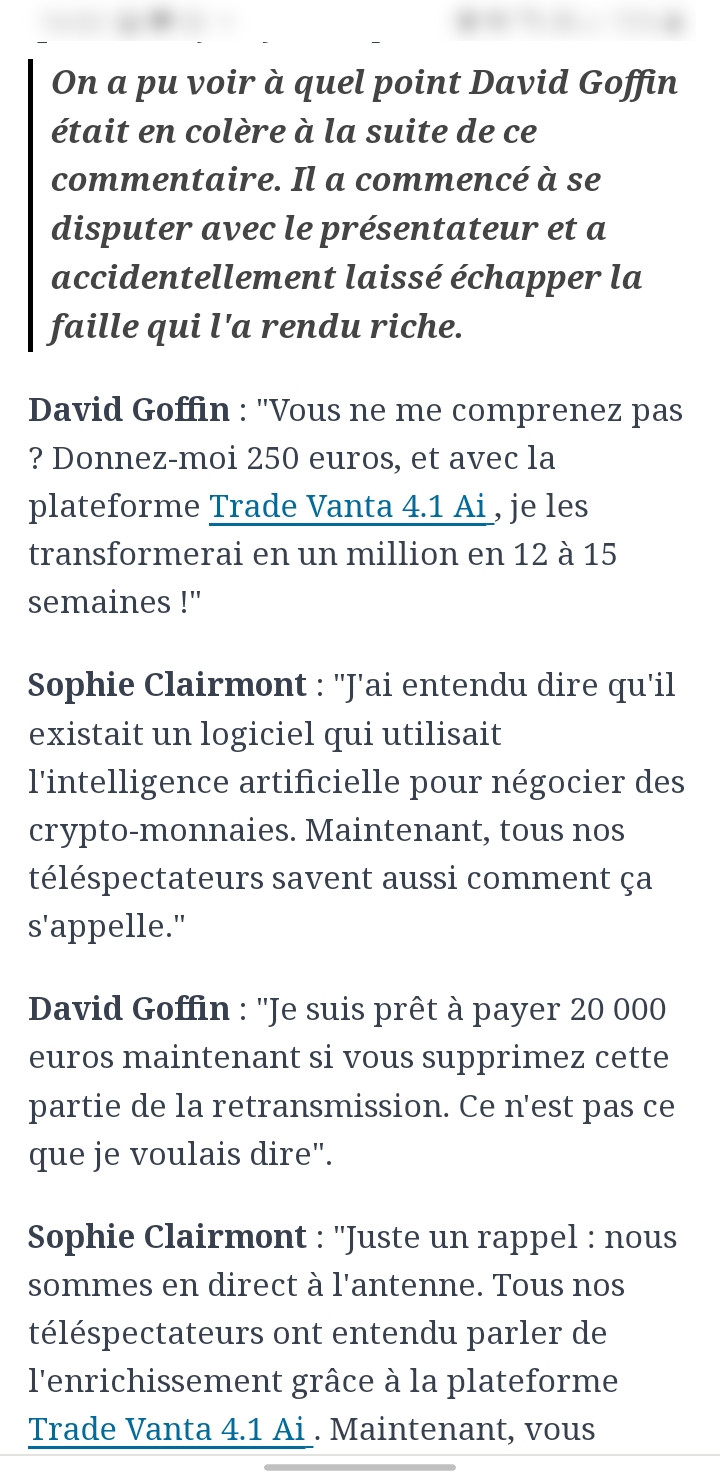
Aaaah the weekend at last… What better way to relax than with a little video? Oh wait! Here’s some bad news: it’s not true that David Goffin has been arrested by the police? This famous professional tennis player. Oh dear!
So this is where my investigation begins. First of all, I was rather surprised by the quality of the deep fake/photo montage in these ads. It’s obvious that for people who specialise in this field, this image is fake. Nonetheless, we have to recognise its quality in comparison with other existing phishing methods. That’s precisely where this scam is interesting, in its realism, and that’s what I’ve decided to analyse in this article. Because it’s not just the photomontage that makes this scam realistic, but many other aspects too. We can imagine that crooks have learned to use AI by now.
| Scamming ad | Page displayed |
|---|---|
 |
 |
Clicking on the link
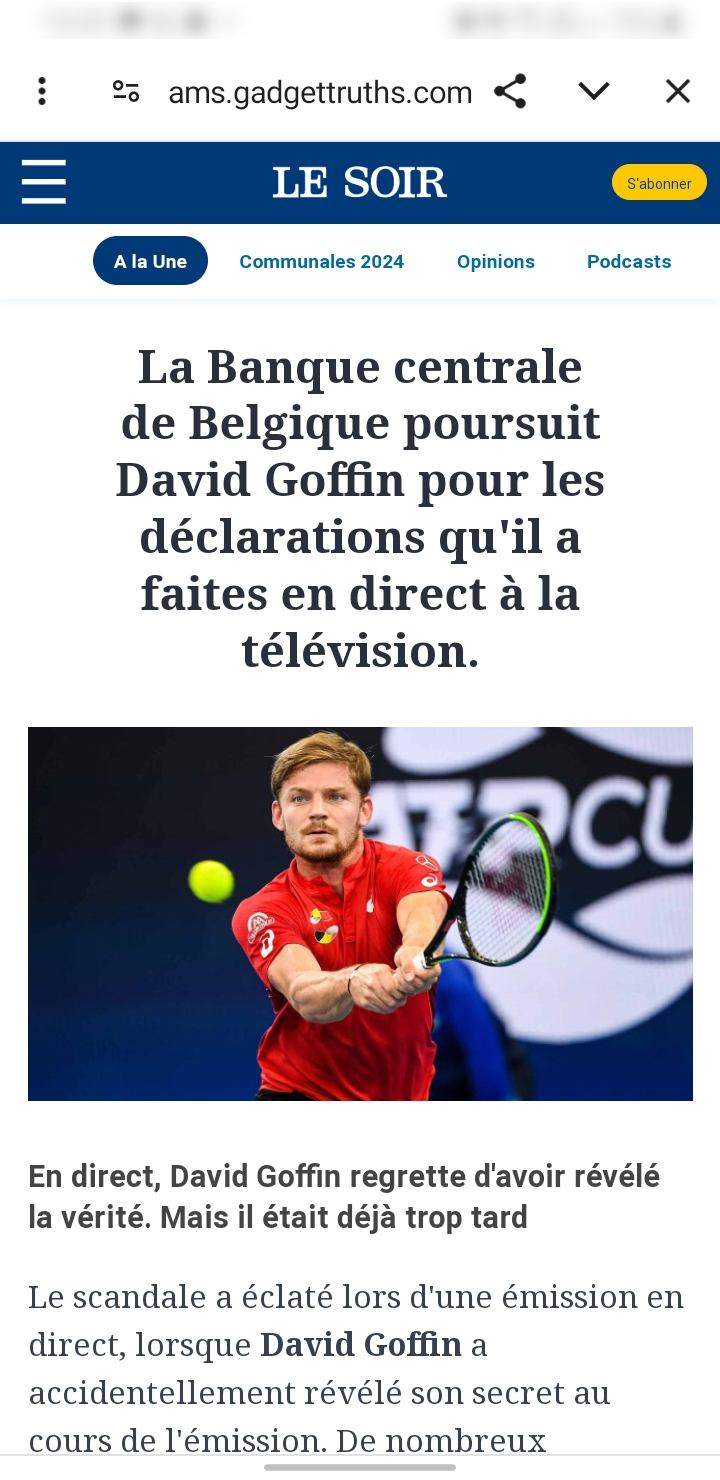
When you click on the link, you are redirected to a Le Soir magazine copycat, where you can see a conversation between ‘David Goffin’ (it’s not him) and a journalist. The first indicator of fraud is the domain name of the website, which is not at all that of the magazine. This domain address also changes. Sometimes it’s ams[.]gadgettruths[.]com, sometimes ams[.]trendclove[.]com, and so on. (more IOCs in part 2)
To return to the article itself, we can see that David recommends a platform for making money: Trade Axions 7.3 AI and when we click on it we are asked to create an account and, no doubt further on, to deposit money in it.
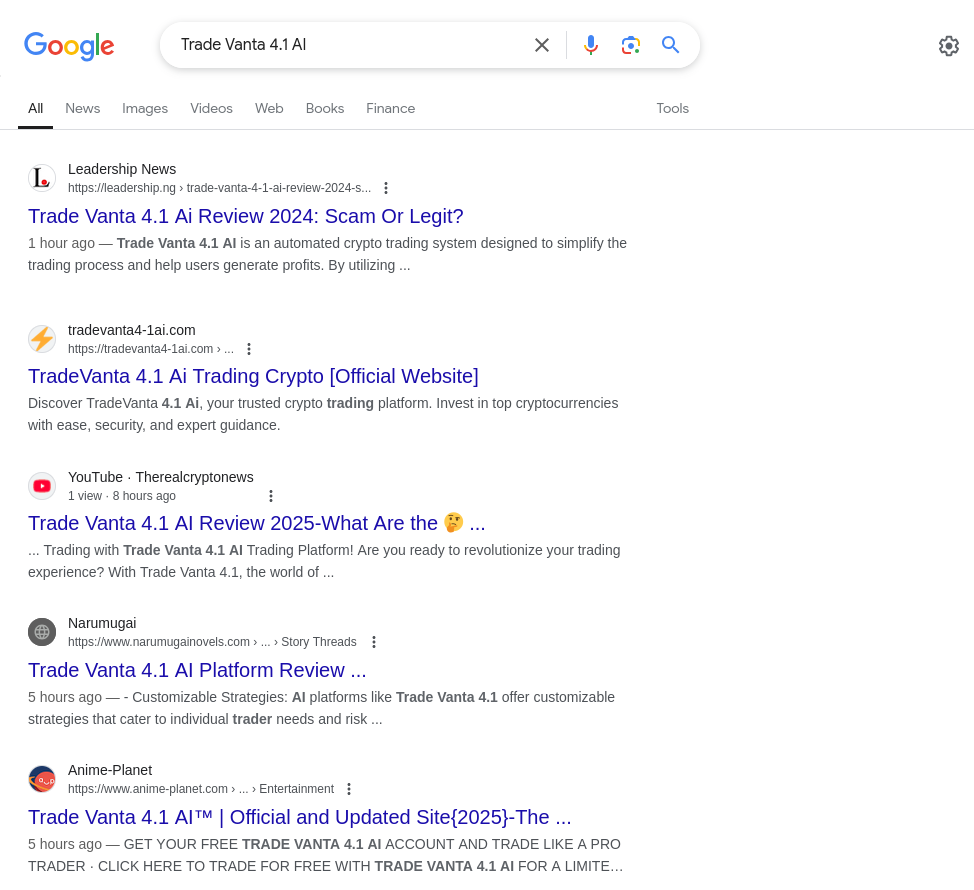
An informed user might want to check whether this application can really make him rich. As a result, if you type `Trade Axions 7.3 AI into Google, you’ll see a host of sites debating whether the platform is a scam or legitimate. This is another example of how sophisticated phishing can be.
Unscrambling the link
When the original link is opened in the browser from a computer, we can see that we are being redirected to a moviefelt[.]com site that looks completely legitimate. The most likely reason for this difference in the way computers and phones work when it requests a web page. In order to make the advert appear legitimate, the scammers have to ensure that the Google bot does not see the scam. And so be able to fool Google’s checks to appear to be a legitimate advert. We can therefore note a second advanced mechanism for this phishing method since it could go unnoticed by a Google detection system or a human inspector who may be qualified.
Below is a screenshot of the Youtube ad if you open it on a computer. We can clearly see that you’re not on the phishing website.
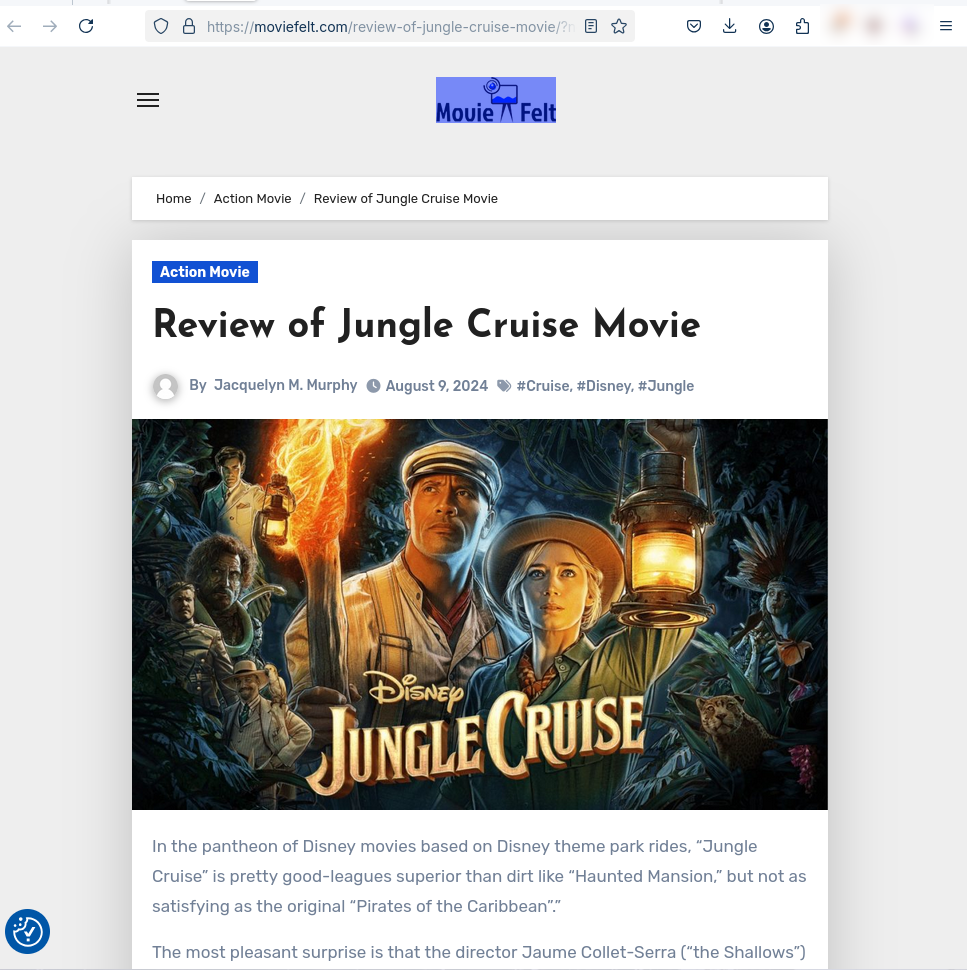
Access the page from a computer
Changing the user agent
It’s rather annoying not to be able to access the phishing page from a computer, for a number of reasons. Firstly, it would be useful to analyse the phishing site from a computer and perhaps find some interesting information. Secondly, because it would also be interesting to understand the bypass mechanics in order to improve scam detection capabilities. Finally, because this could make it possible to build a tool or a script to identify a multitude of malicious domain names. As we saw earlier, the phishing website is hosted on a multitude of domain names.
So the first thing to do to try and access the phishing website is simply to change the user agent to the one on my phone, because I’m sure it’s functional. To do this, I type ‘What’s my user agent’ into Google, retrieve it and then modify the request in Burp in order to carry out the test. I send the request with my phone’s user agent but… What a surprise! I still end up on the ‘Review of Jungle Cruise Movie’ page. The attackers really want the bypass to be more complex.
Intercepting traffic
So I decided to install Android Studio and intercept Android traffic with Burp to be able to see the headers of TLS requests. By the way, to configure Burp for Android, I recommend the very good blog post by Jeroen Beckers.
So let’s put the 2 headers into perspective. HTTPS header from Android:
GET /review-of-jungle-cruise-movie/ HTTP/2
Host: moviefelt.com
Cookie: hcsid=49730285418650213893; cookieyes-consent=consentid:QWxleEdQVFpiVGZSVUZYN0tDZGtzWk9yN2JpQlEwTXY,consent:no,action:yes,necessary:yes,functional:no,analytics:no,performance:no,advertisement:no
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Linux; Android 7.1.1; Android SDK built for x86 Build/NYC) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/55.0.2883.91 Mobile Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Referer: https://moviefelt.com/
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.8
HTTPS header from a computer:
GET /review-of-jungle-cruise-movie/ HTTP/2
Host: moviefelt.com
Cookie: hcsid=49730285418650213893; cookieyes-consent=consentid:QWxleEdQVFpiVGZSVUZYN0tDZGtzWk9yN2JpQlEwTXY,consent:no,action:,necessary:yes,functional:no,analytics:no,performance:no,advertisement:no
Sec-Ch-Ua: "Chromium";v="131", "Not_A Brand";v="24"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "Linux"
Accept-Language: en-US,en;q=0.9
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.6778.86 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: https://moviefelt.com/
Accept-Encoding: gzip, deflate, br
Priority: u=0, i
Ok, let’s delete what we have on the computer that we don’t have on the phone. So there aren’t many areas of difference left. What’s more, we also know that changing the User Agent isn’t enough on its own. If we take a closer look, we can see that the only other difference is in the Accept field. The server checks the User Agent AND the Accept header. If we take a closer look at this field, we can see that on the computer, files of type application/signed-exchange are accepted. According to web.dev, Signed exchanges are a delivery mechanism that makes it possible to authenticate the origin of a resource independently of how it was delivered. In any case, whatever it is, the version of my chromium on Android doesn’t support this type of file. So it’s with this little trick that crooks manage to fool Google’s security checks. Therefore, in order to access to the web page of the phishing website, we have to change the User Agent and delete the application/signed-exchange from the Accept field. This will help us in the next blog post to create a script in order to identify the scammer’s domain names.
Conclusion
Phishing schemes are becoming more and more advanced, and with the advent of AI they are likely to become more and more realistic. It’s true that when you see this first photomontage, you quickly realise that it’s a hoax. Nevertheless, we can imagine that the crooks have surely used deepfake tools to make this montage. Analysis of the text on moviefelt[.]com shows no use of AI to generate the text. So for the time being, the scammers are not using AI to generate realistic text on web pages. However, it is conceivable that in the near future they will use this technology to automate their process. This highlights a possible new way of detecting them.
Taking all this analysis into account, we can conclude that fraudsters are currently using 4 advanced phishing schemes:
- Semi-realistic photomontage
- Making the Google search results mislead the victim by passing off the tool as legitimate
- Give a different version of a web page on a computer and smartphone browser
- Automatic generation of domain names
It’s important to highlight these 4 points because they help identify their behaviour and make it easier to identify them automatically. In all cases, it will always be a game of cat and mouse between detection and bypassing detection. However, we’re highlighting the 3rd point here, which will certainly help to strengthen Google’s detection capabilities if it’s taken into account.
Future work
Since these domain names are active and can be used to defraud people, they need to be reported to CERT. However, since Google’s systems didn’t identify this type of phishing, I’ll be detailing in my next blog post how to build a script to list the different domain names. Part 3 will also be devoted to identifying the crooks behind this phishing.
This blog post is licensed under
CC BY-SA 4.0