Cyrange : firewall configuration
Jan 28, 2022 by Thibault Debatty | 2654 views
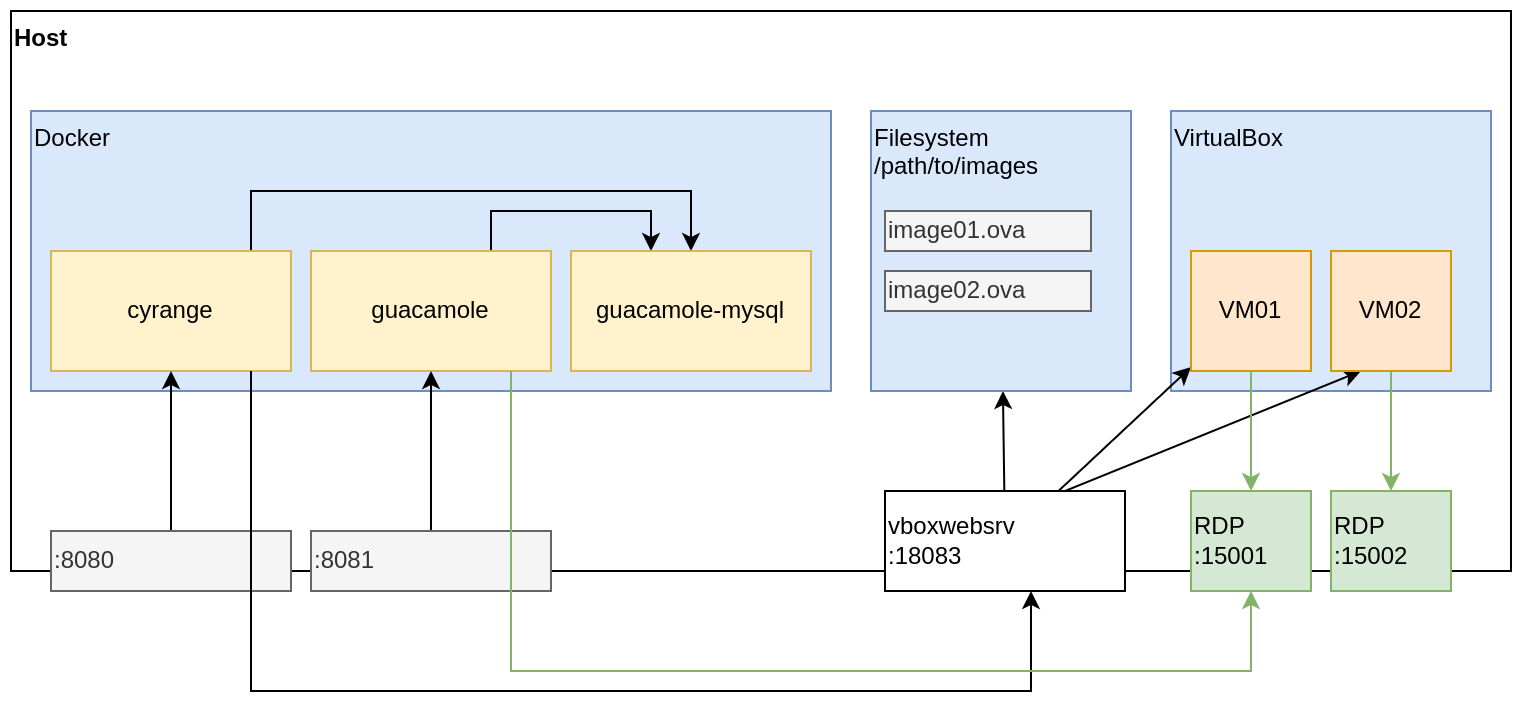
The cyrange Cyber Range is composed of multiple docker containers. After installation, here is how to configure your firewall to allow communication between the different components…
First, let’s allow SSH, HTTP and HTTPS, and increase firewall logging verbosity:
sudo ufw allow ssh
sudo ufw allow http
sudo ufw allow https
sudo ufw logging medium
Now that SSH is allowed, we can enable the firewall:
sudo ufw enable
First we must find the subnet used by our containers:
docker network inspect cyrange_default | grep Subnet
On my server, the subnet used by the cyrange containers is 172.21.0.0/16. You should adapt the examples below according to your subnet…
As we can see on the Figure above, we must allow communication from cyrange to vboxweb-srv:
sudo ufw allow from 172.21.0.0/16 to any port 18083 proto tcp
We must also allow communication from guacamole to RDP ports:
sudo ufw allow from 172.21.0.0/16 to any port 15000:15999 proto tcp
During the deployment of a VM, cyrange will connect to the VM using ssh (on a port in the range 22000-22999), to configure the guest OS. To allow connections from cyrange to the SSH port used for provisioning:
sudo ufw allow from 172.21.0.0/16 to any port 22000:22999 proto tcp
Now, your firewall configuration should look like this:
sudo ufw status verbose
Status: active
Logging: on (medium)
Default: deny (incoming), allow (outgoing), deny (routed)
New profiles: skip
To Action From
-- ------ ----
22/tcp ALLOW IN Anywhere
80/tcp ALLOW IN Anywhere
443/tcp ALLOW IN Anywhere
18083/tcp ALLOW IN 172.21.0.0/16
22000:22999/tcp ALLOW IN 172.21.0.0/16
15000:15999/tcp ALLOW IN 172.21.0.0/16
22/tcp (v6) ALLOW IN Anywhere (v6)
80/tcp (v6) ALLOW IN Anywhere (v6)
443/tcp (v6) ALLOW IN Anywhere (v6)
Finally, if you have NOT configured Apache reverse proxy, you will need to open ports 8080 and 8081 to access the web interface:
sudo ufw allow 8080
sudo ufw allow 8081
This blog post is licensed under
CC BY-SA 4.0