Static code analysis for Laravel
Jun 30, 2020 by Thibault Debatty | 4673 views
In a previous blog post we presented PHPStan, a static code analyzer for PHP. If you are developing a Laravel application, you can of course use PHPStan to validate your code. However, Laravel has a lot of subtleties and auto-magic that make static code analysis challenging. This is where Larastan comes into play: a wrapper around PHPStan that adds support specifically for Laravel.
Installation
As usual, with composer:
composer require --dev nunomaduro/larastan
Then you have to create a configuration file called phpstan.neon :
includes:
- ./vendor/nunomaduro/larastan/extension.neon
parameters:
paths:
- app
level: 5
This file uses neon syntax, which is actually pretty similar to yaml.
Usage
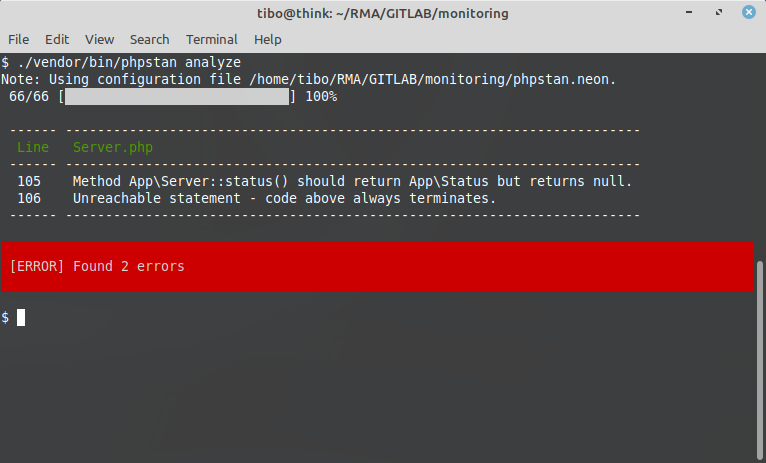
You are now all set to use phpstan for your Laravel project.
vendor/bin/phpstan analyze
Levels, rules and GitLab integration
There is a lot that can be configured in PHPStan. You can find all details in our previous blog post on PHPStan.
This blog post is licensed under
CC BY-SA 4.0